FortiGate Firewall Policy: Rules, Types & Configuration
What Are Firewall Policies?
Firewall policies define which traffic matches them and what FortiGate does when traffic does match, should the traffic be allowed? Initially FortiGate basis this decision on simple criteria, such as the source of the traffic then if the policy doesn’t block the traffic FortiGate begins a more computational security profile inspection often known as Unified Threat Management (UTM), such as Antivirus, Application Control and Web Filtering if you have chosen it in the policy.
Those scans could block the traffic if for example it contains the virus otherwise the traffic is allowed. Will Network Translation Address NAT be applied if Authentication is required, firewall policies also determine answers to these questions.
After processing is finished FortiGate forwards the packet towards its destination. FortiGate looks for matching firewall policies from top to bottom and if the match is found the traffic is processed based on the firewall policy, if no match is found the traffic is dropped by the Default Implicit Deny firewall policy.
FortiGate Firewall Policy Types & Components
Each FortiGate Firewall policy matches traffic and applies security by referring to the objects that are identified such as addresses and profiles.
1. Objects used by the policies:
- Interface and Zone
- Address, User, and Internet service object
- Service definitions
- Schedules
- Nat Rules
- Security Profiles
2. Policy Types:
- Firewall Policy (IPv4, IPv6)
- Firewall Virtual wire pair (IPv4, IPv6)
- Proxy
- Multicast
- Local-in Policy (Origin and Destination is FortiGate itself)
- DoS
- Traffic shaping
How are Policy Matches Determined?
When a packet arrives each policy has a matching criterion which you can define using following objects:
- Incoming interface and Outgoing interface
- Source IP address, User, Internet services
- Destination IP address or Internet Service
- Service IP Protocol and Port number
- Schedule applies during configure times
When the traffic matches the firewall policy FortiGate applies action configured in firewall policy. If the action is set to deny FortiGate drops the session and if the action is set to accept FortiGate applies other configured setting for packet processing, such as Antivirus scanning, Web Filtering or Source NAT.
Interfaces and Zones
Packets arrive on incoming or ingress interface, routing determines the outgoing or egress interface. In each policy you must set a source and destination interface even if one or both are set to any. Both interfaces must match the interface policy criteria to be a successful match. You can group interfaces into logical zones.
By default, you can select a single interface as incoming interface and a single interface as outgoing interface, however you can enable multiple interface selections from firewall GUI. When you choose ANY interface option you cannot select multiple interfaces for that interface.
Policy Matching Criteria
Matching By Source:
In each firewall policy you must select the source address object. You can refine the definition of source address by also selecting a User or User Group, FQDN (Fully Qualified Domain Name) can also be used as source address, but it must be resolved by DNS and cached in FortiGate.
If a User is added as a source, then FortiGate must verify the user before allowing or denying access based on the firewall policy. There are different ways a user can authenticate for local users; the username and password are configured locally on FortiGate.
For remote user such as LDAP or Radius FortiGate receives the username and password from the remote user and passes this information to the authentication server, the authentication server verifies the user login credentials and updates FortiGate after firewall receives that information it creates access to the Network based on the firewall policy. FortiGate Single Sign On (SSO) user information is retrieved from the domain controller access is granted based on group information on FortiGate.
Matching By Destination:
FortiGate checks destination addresses for a match you can use address objects, Internet Service Database (ISDB) objects in a policy. The address object may be a hostname, IP subnet or range. If you configure FQDN as an address object make sure you configure the FortiGate device with DNS servers, FortiGate uses DNS to resolve FQDN address objects to IP addresses, which are what appears in the IP headers. You can use geographic addresses or ranges of IP addresses allocated to a Country; you can update these objects through FortiGuard.
Why is there no option to select a user? The user identification is determined at the ingress interface and packets are forwarded only to the egress interface after user authentication is successful.
Internet Service Objects
Internet service is a database that contains the list of IP addresses, IP Protocols and Port Numbers used by the most common internet services. FortiGate periodically downloads the newest version of this database from FortiGuard, you can select these as Source or Destination in the firewall policies.
What happens if you want to allow traffic only for a few well known internet service destinations such as Facebook or Dropbox?
When configuring firewall policy you can use Internet service as the destination, which contains all the IP addresses, Ports and Protocols used by that service. You cannot mix regular objects with Internet Service Database (ISDB) objects, and you cannot select service on a firewall policy, as the ISDB object already has services information which is part coded. Compared with address objects which you need to check frequently to make sure that none of the IP addresses have changed or appropriate ports are allowed. Internet service helps make this type of deployment easier and simpler.
Policy Scheduling
Schedule adds a time element to a policy. You might use a policy to allow backup software to activate at night or create a test window for remote addresses that is allowed for testing purposes. Schedule can be configured and use 24 hours’ time clock there are few configurations settings worth mentioning:
- Recurring: If you enable all day traffic will be allowed for 24 hours for the day selected. While configuring recurring scheduler if you configure stop time earlier than the start time the stop time will occur the next day.
- One Time: The start date and time must be earlier than the stop date and time. You can also enable Pre-expiration event log, which will generate an event log and number of days before the schedule expires.
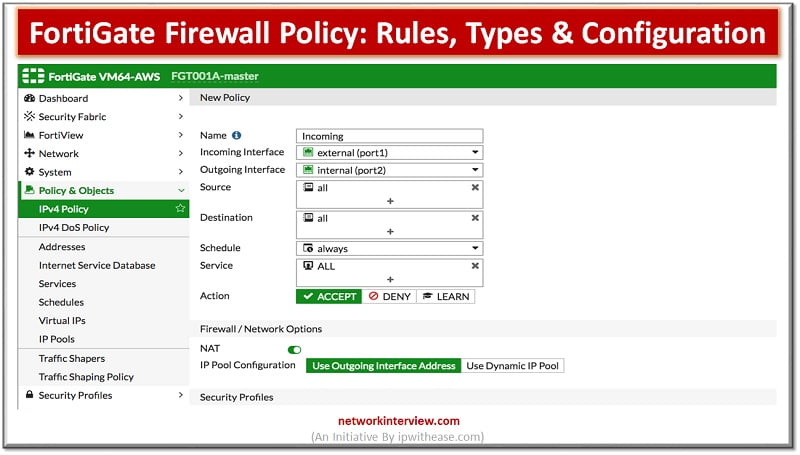
Configuring FortiGate Firewall Policy
When you configure a new firewall policy on the GUI, you must specify a unique name for the firewall policy because it is enabled by default. This helps the administrator to quickly identify the policy they are looking for. You can make this feature optional on the GUI on the feature visibility page by Allowing Unnamed Policies.
There are many options you can configure on the firewall policies such as Firewall and Network options, Security profiles, logging options and enabling and disabling a policy. When creating firewall objects or policies a UUID (Universally Unique Identifier) attribute is added so that logs can record these UUID’S and improves functionality interpreting with FortiAnalyzer.
When creating firewall policies remember FortiGate is a stateful firewall as a result you need to create only one firewall policy that matches the direction of the traffic that initiates the session, FortiGate will automatically remember source, destinations and allow replies.
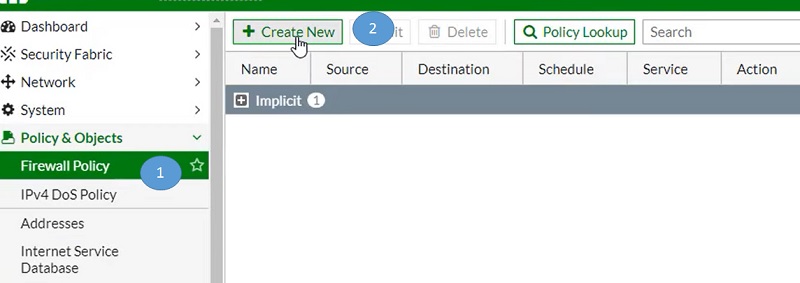
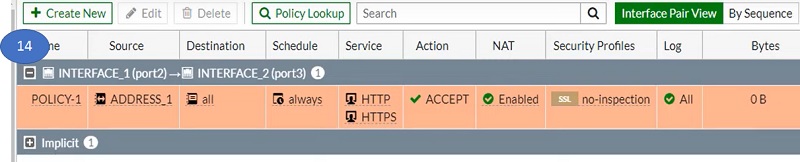
Please refer step 1 to step 14 to configure Security policy in FortiGate firewall
- Go to Firewall Policy
- Select Create New Tab in left most corner
- Fill options in the screen, Name the policy
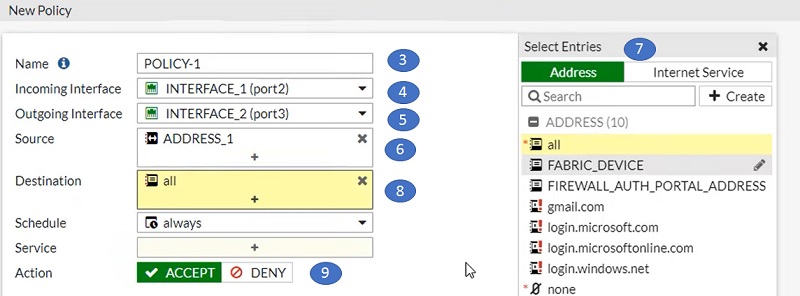
- Select Incoming interface of the traffic
- Select outgoing interface of the connection

- Select list of IP address/subnet of source
- Select list of IP addresses from Address objects
- Select destination Address
- Select Action as Accept/deny as per requirement

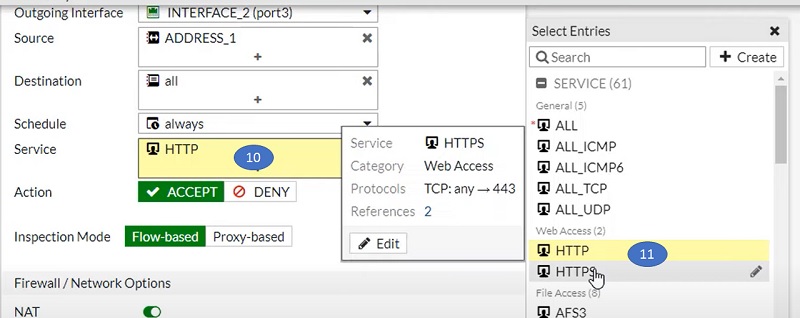
- Select port/service
- Select the services from Service object (right most corner)

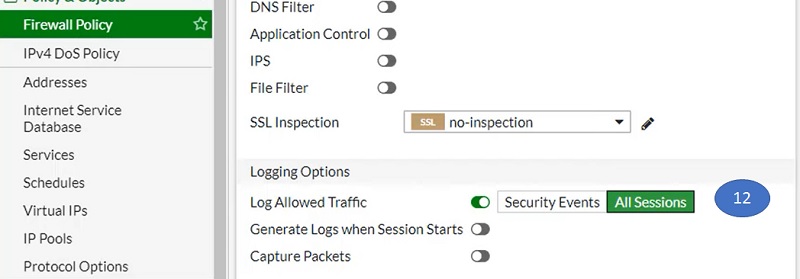
- Allow logging to the sessions
- Select OK

- Policy will look like the pic below.

Security Profiles
One of the important features that a firewall policy can apply is security profile, such as an IPS and Antivirus. A security profile inspects each packet in the traffic flow when the session is already conditionally accepted by the firewall policy.
When inspecting traffic FortiGate can use one of two methods. Flow based inspection or Proxy Based inspection. Different security features are supported by each security type.
Security profiles configured in firewall policies protect the network by blocking threats, controlling access to certain applications and URLs, and preventing specific data from leaving your network.
Continue Reading:
FortiGate VDOM Configuration: Complete Guide
Routing Configuration in FortiGate Firewall: Static, Dynamic & Policy Based