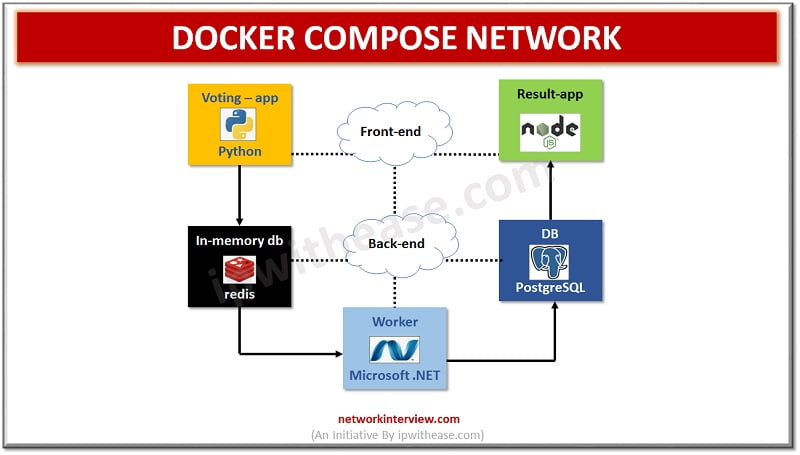
Docker Compose Network Host: Docker Networking
Introduction to Docker Networking
Docker is a centralized platform which supports packaging, deployment and applications execution. Docker has become a model for building and running containers and it is a combination of command line interface and daemon process which solves common software problems such as installation, publishing, removal, and management of containers. Dockers make packaging easier. An application inside a container is easier to scale and can run on different cloud platforms like AWS, Google cloud services and Azure.
In this article we will learn more about the network aspect of docker , how it works , setting up docker networks , its features, functions and limitations and so on.
Docker Compose Network Host
Networking is all about communication within processes and docker networking takes it one more step ahead. Docker networking is majorly used to establish communication between docker containers and the outside world using a host machine which is running docker daemon.
Dockers support a variety of networks which fit as per use cases. Docker networking is very different from virtual machine or physical machine networking. Docker typically uses bridge network and can support host networking but only on Linux. In docker containers network isolation is done using a network namespace instead of using the entire networking stack. Hundreds of containers can run on a single docker host.
Communication rules between containers and host systems are defined by networks and their configuration provides complete isolation for containers, which enables building applications that work together securely. A Compose by default sets up a single network for each container. Docker handles communication between containers by creating a default bridge network and allows to create different types of network drivers out of the box such as bridge, host, and none.
Bridge driver – when a docker is started all containers connect to the default bridge network. Bridge network solves port conflict problems. Docker uses ip tables on the host machine to prevent access outside the bridge.
Run ‘docker ps’ command to check status of containers
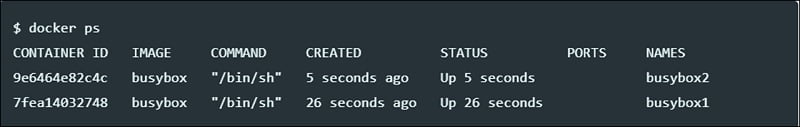
Verify if containers are connected to bridge network
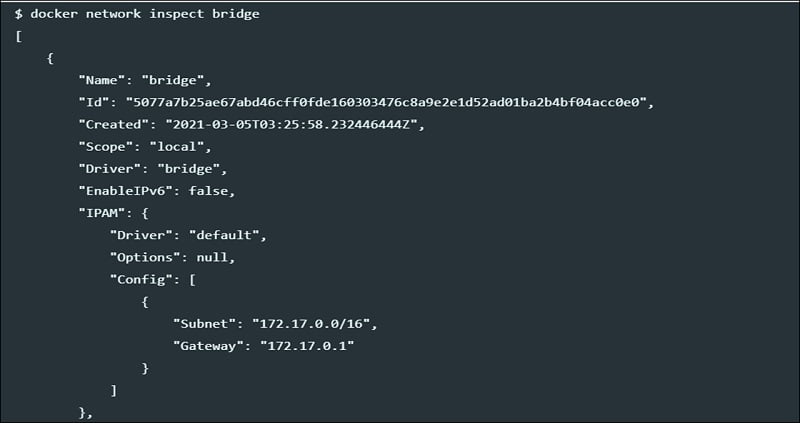
However, it is not suitable for production; the containers communicate via IP address so every time you run a container, a new IP address gets assigned to it. It may be suitable for local development but not sustainable for applications running in production.
Also, another problem is that it will allow unrelated containers to communicate with each other which may pose a security risk.
The Host driver uses networking provided by the host machine. And removes network isolation between the container and the host machine where docker is running. It has one limitation as it does not work on docker desktop and Linux host is required to use it. Downside is it can’t run multiple containers on the same host having the same port.
The None driver does not attach containers to any network. Containers don’t access external networks or communicate with containers. This is ideal when you want to disable networking on a container.
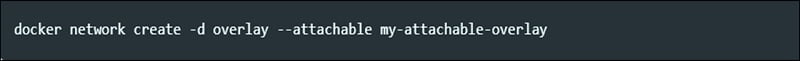
The overlay driver is a multi-host communication , it allows containers across hosts to communicate with each other irrespective of the bother about setup. To create an overlay network for docker swarm service below command is used.

To create overlay network use below command
The Macvlan driver connects docker containers directly to the physical host network. They are best suited for legacy applications which need to be modernized by containerization and running them on cloud infrastructure but required to be attached to physical networks due to performance purpose. In this setup MAC addresses are assigned to containers.
Features of Docker Compose Network Host
- Easier and faster configuration
- Improves productivity
- Application isolation can be achieved as each container is independent to another
- Swarm supports clustering and scheduling
- It routes incoming request for published ports on available nodes of active container
- Security Management feature helps to save secrets from Swarm itself
Ways to setup Docker Compose Network Host
Custom networks – instead of using default networks we can also specify a custom network within the top-level network key which allows to create more complex topologies and let you specify network drivers and options.

Each container can specify which networks to connect to with service level keyword ‘networks’. A custom name can be provided to network .

External (pre-existing networks) can be used with docker compose using the external option.

Instead of defining custom networks, default network settings can be changed by defining any entry with name default under ‘networks’ keyword.
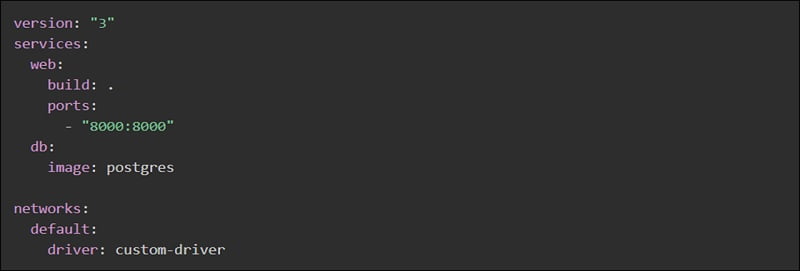
Multiple docker compose files can also be an option to change your application for different environments such as production, dev, test , staging etc. Docker Compose will read two files by default – a docker-compose.yml file, and an optional docker-compose.override.yml file. The docker-compose.override file could be used for storage of overrides of the existing services or define new services.
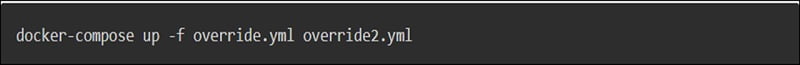
While using multiple configuration files, make sure that paths are relative to the base Compose file which is specified first with the -f flag.
Continue Reading:
VM vs CONTAINER – Detailed Comparison
Tag:cloud



