CASB vs Proxy: Understand the difference
A common question arises in the mind of IT focals related to Cloud access security broker (CASB) service products such as we already have a web proxy firewall then how is this different? Is CASB a replacement for web proxy/ firewall? As web proxies and firewalls have visibility into all traffic over the organization network which also includes traffic from cloud services. However, there is a significant difference between the two and CASB is not a replacement for web proxy or firewall.
Today we look more in detail about cloud access security broker (CASB) and web proxy, what are the significant differences between both products, its advantages etc.
About CASB
Cloud access security broker (CASB) is a cloud hosted solution placed between cloud service customers and cloud service providers to implement security, compliance and governance controls and security policies for cloud-based applications and help to extend security controls of infrastructure over the cloud. There are four pillars of CASB namely visibility, compliance, data security and threat detection.
- Visibility – into user activity over cloud applications such as who uses which cloud application, their departments , locations and devices being used
- Compliance – identify sensitive data in cloud and enforce DLP policies to ensure data compliance objectives are met
- Data security – implements data security such as encryption, tokenization and access control inclusive of information rights management
- Threat protection – detect and respond to malicious threats, privilege user threats and accounts compromise
Features of CASB
- Identification of malware attack and its prevention from entering it into organization network
- User authentication checking of credentials and ensures access to granted to only appropriate resource
- Web application firewalls (WAF) designed to breach security at application level instead of network level
- Data loss prevention to ensure users cannot transmit organization confidential information or intellectual property outside its boundaries
- Provides detailed, independent risk assessment for each cloud services
- Enforces risk-based policies
- Controls user access based on context
- Apply machine learning to detect threats
Use cases for CASB
- Discovery of cloud application and risk rating assignment
- Adaptive access control
- Data loss prevention
- Behaviour analytics for users and entities
- Threat protection
- Client facing encryption
- Pre-cloud encryption and tokenization
- Bring your own key management
- Monitoring and log management
- Cloud security posture management
How does CASB work?
CASB working involves securing data flow to and from cloud environments by implementation of organization security policies and protection against cyber attacks, malware prevention and provide data security with encryption and make data streams non-interceptive for hackers. It uses auto discovery to locate cloud applications in use and identify high risk applications, users and key risk factors.
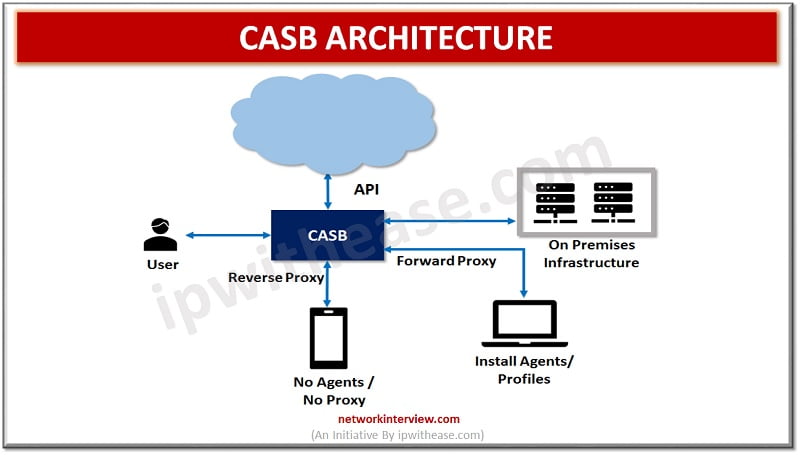
CASB can be deployed in forward or reverse proxy mode to enforce online controls however similarities stop here with web proxy. CASB is focused on deep visibility and granular controls for usage of cloud. it can be deployed in API mode to scan data at rest in cloud services and enforce policies across cloud applications data.
About Proxy
Web proxies offer broad protection against network threats, and offers limited visibility into cloud usage, without any integration to CASB it tracks cloud access over corporate networks. Some customers use network security solutions to terminate SSL and inspect content for malware, proxies and firewalls and bucket cloud services into high level categories which usually do not cover the underlying function of the services such as CRM, file share or social media. Usually, web proxies redirect URL access requests to an alternate web page hosting a notification that URL is blocked (millions of illicit sites containing pornography, drugs, gambling etc.).
Firewalls can be configured to block traffic from a specific IP address in the same manner. But it lacks detailed and up to date cloud registries with cloud service URLs and IP addresses to extend this access control functionality over to cloud services. As routinely new URLs are introduced by cloud service providers and IP that are not blocked which leads to ‘proxy leakage’ in which employees may have access to websites which IT does not want them to visit. CASB works as complementary technology to web proxies and can leverage existing network infrastructure to gain visibility into cloud usage.
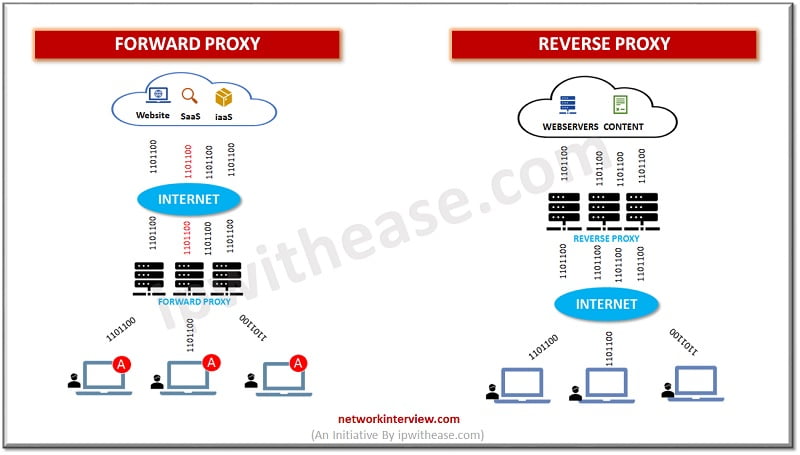
Web proxies capture data about cloud usage occurring over the network but cannot differentiate between cloud usage and internet usage.
Comparison Table: CASB vs Proxy
Below table summarizes the difference between the two:
FUNCTION | CASB | PROXY |
| Log Collection | CASB solutions detect which users are using which cloud services by ingestion of log files | Capture cloud usage over network but can’t differentiate between internet usage and cloud usage |
| Packet Capture | CASB ingests part of traffic into existing network solution and gain visibility into data in packet capture | Usually inspects web traffic and block URLs based on policies and redirects user to a web page indicating URL is blocked due to varied reasons such as gambling ,illegitimate sites etc. |
| Access | Access over browser, mobile applications and desktop apps, sync client | Browser only |
| Use Cases | Quarantine sensitive data and malware, encrypt sensitive data at rest , remove public shares of sensitive data | Stop malware Encrypt sensitive data in real time Govern on or off managed network devices |
| Products | MacAfee MVISION, Microsoft defender, Symantec CloudSOC etc. | SmartProxy, Brightdata, Oxylabs etc. |
Download the comparison Table: CASB vs Proxy
Continue Reading:
CSPM vs CASB: Detailed Comparison
Tag:comparison, virtualization



