Cisco FTD URL Filtering: How does it work?
Pic: Showing How Cisco FTD URL Filtering works
URL filtering or content filtering is one of the key features of firewalls. It helps to prevent access to harmful and malicious content which could cause data loss, system crash, virus or worm infestation and provides employees access to good and reliable websites relevant for the business. Cisco URL filtering works in a similar way and based on the reputation rating or general classification of the website, risk level provides controlled access to Internet websites by configuring URL based policies and filters on the FTD.
In today’s lesson we will cover in detail about how Cisco FTD URL filtering functionality works, how it is configured and used.
Cisco FTD URL Filtering
URL filtering feature lets you control websites which users’ access on the network. URL filtering is majorly based on category and reputation or you can also opt for manual filtering where you can manually specify individual URLs, group of URLs, URL lists and feeds to achieve a more granular level of custom control over web traffic.
FTD URL classification could be based on categories (classification) + reputation (risk level which can vary from High risk (1) to well known risk (5). If reputation level is set to ‘allow’ , all subsequent levels will be allowed also vice versa if reputation level is selected as ‘block’ , all subsequent levels also will be blocked.
URL filtering can be configured on HTTP, HTTPS, SSL.
HTTP filtering – URL filtering will be performed on plain text and configured in Access Control Policy (ACP) by matching application and configuring URL filter
HTTPS filtering – FTD detect URL during SSL handshake from certificate CN , it disregards subdomains in CN and matches root domain only
SSL filtering – Manual filtering is not supported and it is configured in SSL policy to match categories
Manual filtering – You can override URL categories and groups by manual URL configurations. But wildcard characters are not supported
In FTD individual rules can be placed within categories and use to match based on zone, networks, VLANs tags, Users, Applications, Ports, URLs, SGTs. Based on rules actions can be considered to do when the match is available such as Allow, Trust, Monitor, Block, Block and Rest, Interactive block, interactive block with reset.
Limitations of FTD URL filtering
- Connection establishment with 3-way TCP handshake post receiving SSL exchange or HTTP request only FTD will be able to act
- Uncategorized URLs will pass thru unless they are blocked explicitly
- It does not block search on blocked categories
- Appliances with low memory perform more generic matches
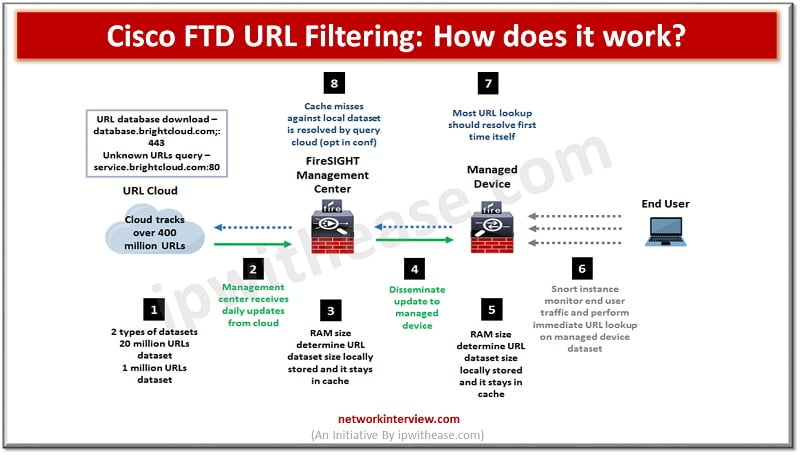
How does the Cisco FTD URL lookup process work?
To accelerate the URL lookup process, URL filtering works on a local dataset installed on FirePower system locally. Availability of memory determines type of dataset availability as per below table.
Dataset Type | Memory Requirement | |
| Ver 5.3 | Version 5.4 or higher | |
| 20 million URL dataset | 2GB | 3.4 GB |
| 1 million URL dataset | <= 2 GB | <= 3.4 GB |
Cisco FTD URL Filtering Configuration
Prerequisites to be met:
- URL filtering licences for FirePower Threat defense devices
- URL filtering licenses for classic devices
- Assign URL filtering license to each managed device which will filter URLs
- At least one managed device must have URL filtering license assigned to it
- FirePower appliances are configured to connect to Internet on ports 443/tcp (HTTPS) and 80/TCP (HTTP) and to download or query URL category and reputation data
Configure URL filtering with category and reputation.
Step 1: In access control rule editor, click URLs tab
Step 2: Click the Category tab in Categories and URLs list
Step 3: Find and select categories of URL need to be added to the Category list. If you want to match web traffic irrespective of Category then choose Any category. Click on Search for a category prompt above Category list and type the category name.
Note : Maximum of 50 items to the selected URLs can be added to match a single URL condition.
Step 4: To qualify your category selections click a reputation level from Reputations list. If reputation level is not selected by default, it would be Any which means all levels.
Step 5: Click Add to Rule to add selected items to Selected URLs list
Step 6: Save to continue
Example
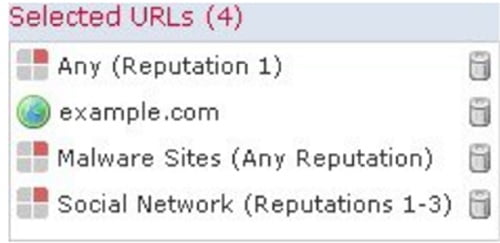
Block | Category or URL | Reputation |
| Malware sites | Malware websites | Any |
| Any URL with high risk (level 1) | Any | 1-High risk |
| Social networking sites with risk levels 1 to 3 | Social network | 3 – Benign sites with security risks |
| example.com | the URL object name | none |
Manual URL filtering
Manual URL filtering is used to supplement or override URL filtering by category and reputation. We can control web traffic by manually specifying individual URLs, groups of URLs, or URL lists and feeds. This lets you do more granular control to block web traffic.
Step 1: In access control rule editor, click URLs tab
Step 2: Click the URL tab in Categories and URLs list
Step 3: Find and select URLs need to be added from URLs list. To search for URL objects, groups, global lists, custom lists and feeds or URL categories to add, click the Search for a URL prompt above URLs list, type either name of object or value of a URL or IP address in the object. The list updates as you type. To select object click it
Note: Maximum of 50 items to the selected URLs can be added to match a single URL condition.
Step 4: Click Add to Rule to add selected items to Selected URLs list
Step 5: Save and continue
Continue Reading:
URL Filtering vs Proxy : Know the difference
FAQs
Is FTD a zone-based firewall?
As a firewall, FTD utilizes a zone-based system, the same security traffic CLI is not necessary for communication to take place between different interfaces.
What is URL Filtering in FTD?
The Cisco FTD URL Filtering feature provides the capability to regulate the websites that individuals on your network can view, depending on its category, reputation, a mixture of both category and reputation, as well as manually-entered URLs.
How Does URL Filtering Work?
URL filtering technology utilizes a database of URLs to determine whether or not web traffic should be allowed to pass through, depending on the details stored in the database.
What is the difference between URL Filtering and Domain Filtering?
In comparison to DNS filtering, which centers on blocking domains, URL filtering enables you to secure users by obstructing access to precise URLs. Furthermore, URL filtering concentrates on HTTP/HTTPS traffic and provides user-oriented rules for allowing, cautioning, or impeding access to web categories or particular URLs.



