
What is SSH(Secure Socket Shell)?
SSH PROTOCOL
SSH (or Secure Shell) is a protocol that facilitates secure communications between two systems using a client/server architecture and allows users to connect to a host remotely. Unlike other remote communication protocols such as FTP or Telnet, SSH encrypts the connection session, making it impossible for someone to obtain unencrypted passwords.
SSH is designed to replace older and less secure methods to register remotely on another system through the command shell, such as telnet or ssh. A related program, the SCP, replaces other programs designed to copy files between hosts such as RCP. Since these old applications do not encrypt passwords between the client and the server, avoid using them as long as possible. The use of secure methods to register remotely to other systems reduces security risks for both the client system and the remote system.
SSH FEATURES
SSH protocol provides the following types of protection:
- After the initial connection, the client can verify that it is connecting to the same server to which it was previously connected.
- The client transmits its authentication information to the server using a robust 128-bit encryption.
- All data sent and received during the session is transferred through 128-bit encryption, which makes it extremely difficult to decrypt and read.
- The client can forward X11 applications from the server. This technique, called X11 forwarding, provides a secure means to use graphic applications over a network.
Since the SSH protocol encrypts everything it sends and receives, it can be used to secure insecure protocols. The SSH server can become a conduit to make insecure protocols secure by using a technique called port forwarding, such as POP, by increasing the security of the system in general and data.
Red Hat Enterprise Linux contains the general OpenSSH package (OpenSSH) as well as the OpenSSH server (OpenSSH-server) and client (OpenSSH-clients) packages.
WHY USE SSH?
Users have a variety of tools at their disposal that allows them to intercept and redirect network traffic to gain access to the system. In general terms, these threats can be cataloged as follows:
Interception of communication between two systems – In this scenario, there is a third party somewhere in the network between entities in communication that makes a copy of the information that passes between them. The interceptor may intercept and retain the information, or may modify the information and then send it to the recipient to which it was intended.
- This attack can be mounted through the use of a sniffer package – a very common network utility.
- The personification of a particular host – With this strategy, an interceptor system pretends to be the recipient to whom a message is intended. If the strategy works, the user’s system does not realize the deception and continues communication with the wrong host.
This occurs with techniques such as DNS poisoning or IP spoofing (IP address deception).
Both techniques intercept potentially confidential information and if this interception is done for hostile purposes, the result can be catastrophic.
ENCRYPTION TECHNIQUES
The significant advantage offered by SSH over its predecessors is the use of encryption to ensure the secure transfer of information between the host and the client. Device refers to the remote server you are trying to access, while the client is the computer you are using to access the host. There are three different encryption technologies used by SSH:
- Symmetric encryption
- Asymmetric encryption
- Hashing
SYMMETRIC ENCRYPTION
Symmetric encryption is a form of encryption in which a secret key is used for both encryption and decryption of a message, both by the client and by the host. Indeed, anyone who has the key can decrypt the message that is transferred.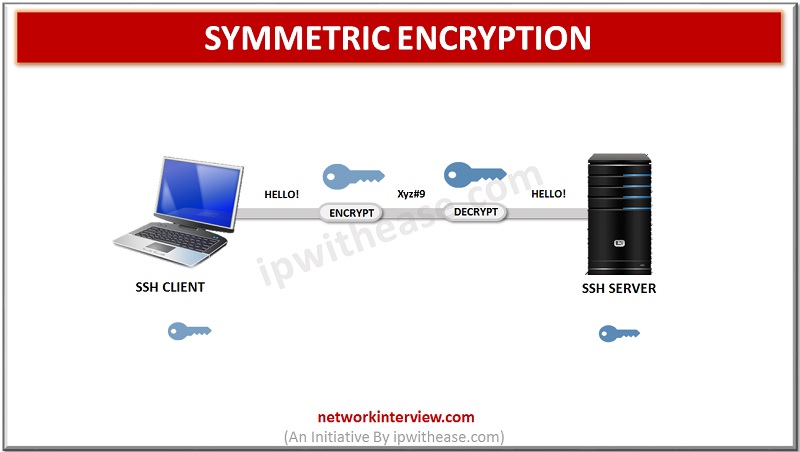
Symmetric encryption is often called a shared key or shared secret encryption. Normally there is only one key that is used, or sometimes a pair of keys where one key can be easily calculated with the other key.
Symmetric keys are used to encrypt all communication during an SSH session. Both the client and the server derive the secret key using an agreed method, and the resulting key is never disclosed to third parties. The process of creating a symmetric key is carried out using a key exchange algorithm.
ASYMMETRIC ENCRYPTION
Unlike symmetric encryption, asymmetric encryption uses two separate keys for encryption and decryption. These two keys are known as the public key and the private key. Together, these keys form the public-private key pair.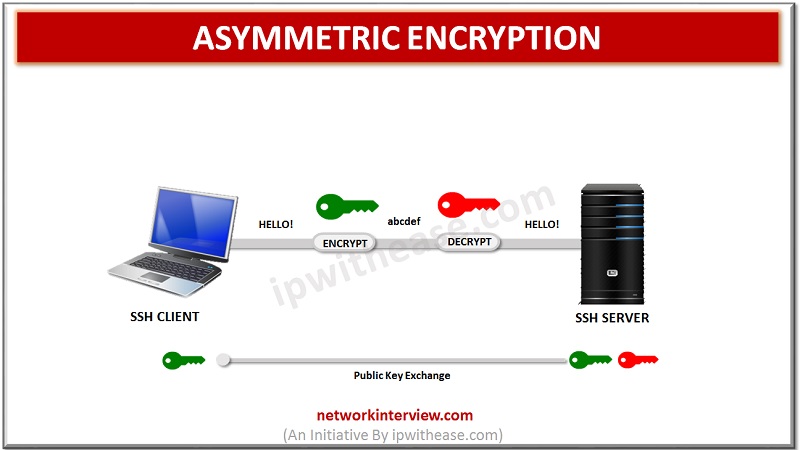
The public key, as the name suggests, is openly distributed and shared with all parties. While it is closely linked to the private key in terms of functionality, the private key cannot be calculated mathematically from the public key. The relationship between the two keys is highly complex: a message encrypted by the public key of a machine can only be decrypted by the same private key of the machine. This unidirectional relationship means that the public key cannot decrypt its messages or decrypt anything encrypted by the private key.
The private key must remain private, that is, for the connection to be secure, no third party should know it. The strength of the entire connection lies in the fact that the private key is never revealed since it is the only component capable of decrypting messages that were encrypted using its public key. Therefore, any party with the ability to decrypt publicly signed messages must possess the corresponding private key.
Unlike general perception, asymmetric encryption is not used to encrypt the entire SSH session. Instead, it is only used during the symmetric encryption key exchange algorithm. Before initiating a secure connection, both parties generate temporary public-private key pairs and share their respective private keys to produce the shared secret key.
Tag:protocol



