
What is Spoofing? Detailed Explanation
Introduction to Spoofing
Today, in the cyber security community “spoofing” is called as any fraudulent or malicious practice in which communication is established from an unknown source, usually disguised as a known source to the receiver.
In order to understand how “spoofing” works, consider it as a trick from hackers where specific email software is used in order to change email, sender’s name, address and source IP. The resultant output looks like a normal email from a company’s domain address.
Spoofing emails nowadays usually are sent from fake banks and public organizations (Ministry of Social Affairs, etc), which can lead to victim’s curiosity about winning a big prizes or a big amount of money (Lottery, Funding Opportunities, etc.) and thereby stealing individual’s personal information (Name, Address, Telephone, etc).
Techniques – Methods of Spoofing
Nowadays, the most common techniques used for ”spoofing” on the web are the following:
ARP SPOOFING
In this method, the hacker sits (quietly) on a network along with the victim and tries to crack the network’s ip address using the Address Resolution Protocol (ARP). This kind of networks are usually private networks with access from a normal wireless router, where the victim’s computer is connected.
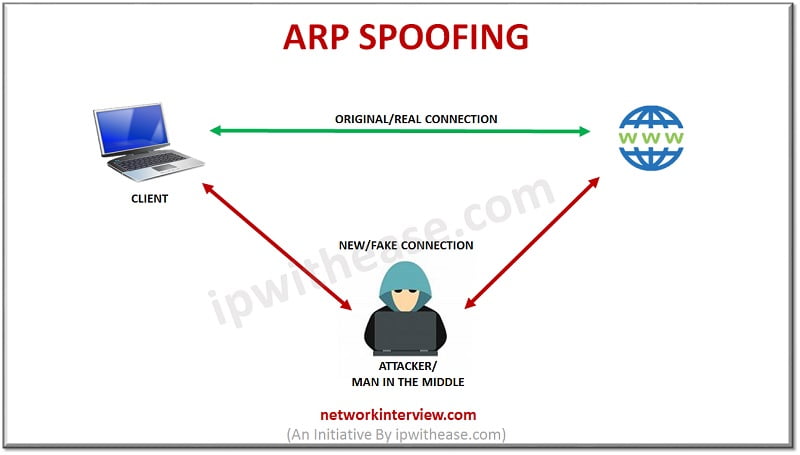
In this kind of attack method, the attacker performs multiple roles. The main role is to modify data between the router and the victim. The hacker can also intercept and stop various data exchanges in between this communication.
The victim on the other hand will not understand any malicious activity unless ARP Spoofing Detection Software is used. Also, a precaution may be considered like periodical check of website’s statistics for network spikes or service unavailability errors.
IP SPOOFING
In this type of method, the main idea is that the hacker impersonates, or in simple words, uses a specific IP address (fake one), in order to hide his identity and deceit the victim. Then the hacker sends information (data packet) to the victim, who is unaware of the legitimation of the source IP.
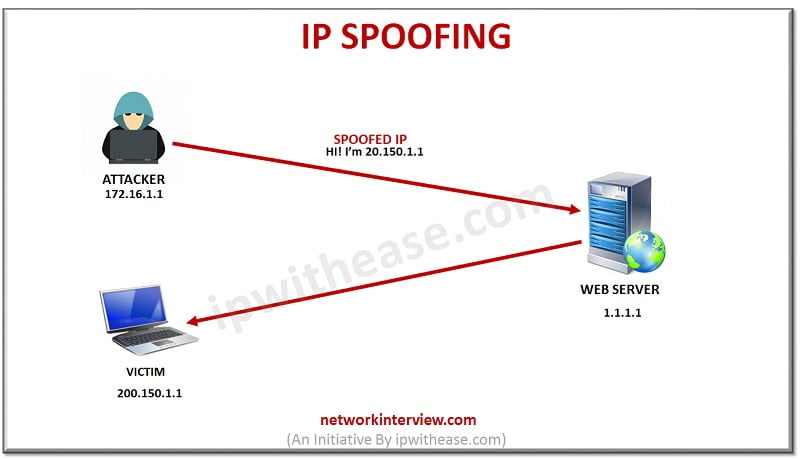 A careless mistake of identification for such an attack, can lead to leakage of personal information (Name, Address, Telephone, etc). A prevention can happen if the victim considers carefully the hackers sent information.
A careless mistake of identification for such an attack, can lead to leakage of personal information (Name, Address, Telephone, etc). A prevention can happen if the victim considers carefully the hackers sent information.
DNS SPOOFING
In order to understand this type of method, a short briefing of DNS Domain should be explained. This technology in simple words is huge database of public ip addresses and hostnames that helps the user to remember specific web pages such as (Google, Facebook, etc).
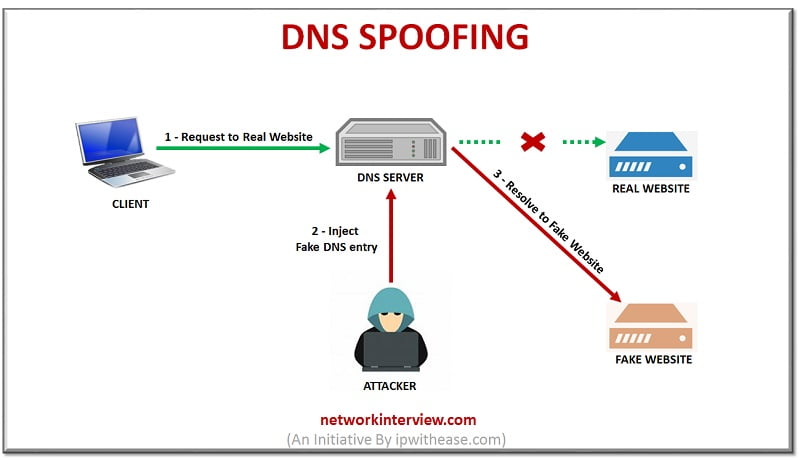
DNS Spoofing involves corrupting the DNS Domain and misleading the victim to a different (fake) domains. Many search engines are aware of the vulnerability and try to remove spoofed domains from their database. They also try to address any type of inconsistencies and errors with user feedback forms.
Mitigation from Spoofing/ How to Protect?
In order to protect yourself from spoofing, you have to realize that these kind of attacks can come in so many different shapes. Most of the effective tips have been shared below:

- Stay Sharp: The most effective way to deal Spoofing is to stay alert, observe any signs of such an attack. Try to avoid answering misleading emails and try not to open links with strange domain names.
- Antivirus Software: Nowadays, high end solutions are being offered by Antivirus companies that prevent such kind of attacks or they simple warn the user of the outcome of a “click” on your computer. Try to keep your antivirus up to date and don’t hesitate to invest some money on antivirus and its subscription.
- Report Spoofing: A very significant way of dealing with spoofing attacks is to report any weird activities faced in everyday life. Many companies offer a contact form for spoofing on their website. In addition to that, local authorities like Police Department will be happy to receive your report and the relevant cybersecurity department will react as expected.
Related – What is VPN?
Conclusion
Considering the current Spoofing Methods, the network security community needs to be aware of the gravity of problem and commit themselves towards safeguarding people’s personal information. Therefore Government Funding opportunities should arise to help security experts deal with these problems and live in a safe world.
Tag:Security



