What is mDNS(Multicast DNS)?
What is mDNS?
The method of using familiar semantics of operating, packet formats and interfaces of DNS programming in small network without a DNS server is termed as Multicast DNS or mDNS. Every network node with mDNS reserved multicast address of 224.0.0.251 is sent with IP packets and response to the same is given with service capabilities by devices.
Multicast DNS or mDNS is a combined effort by DNS Extensions and Zero Configuration Networking working groups’ participants. While the working group Zeroconf drives the requirements, DNSEXT group has its chartered work item as details implementation. mDNS has most of its working team as people who are participating actively in both the working groups.
Related – DNS vs mDNS
While a completely zeroconf name resolution demands, the better method for giving this functionality is taking the existing standard DNS protocol and making minimal changes in it. The application programmers are saved with this from the need of learning new APIs, writing code of application in two diverse methods. In other words, it states that no changes are needed in most of the existing applications so that they can correctly work in Zeroconf network using mDNS.
Engineers are also saved with this from the need of learning a protocol that is completely new. Also, no updates are needed for understanding formats of new packets since DNS packets could already be displayed and decoded by the exiting tools of network packet capture. Over port 5353, the UDP queries could be used for contacting with the mDNS service.
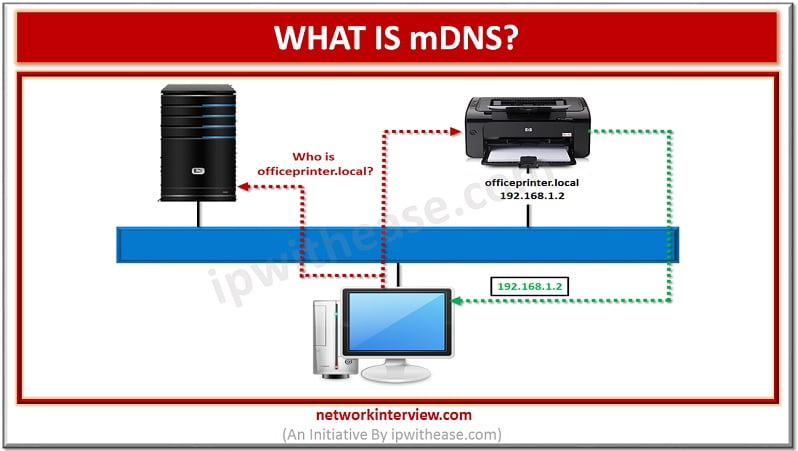
Multicast DNS uses suffix of .local, like http://abc.local. Let’s say my mDNS capable PC wants to send a request to domain name with suffix of .local, it will be a multicast query to all the devices on the LAN that (devices should be supporting mDNS), asking the device with that specific domain name (via suffix) to identify itself. The correct device then responds with another multicast and send its IP address. This way, since the computer knows the IP address of the device, it can therefore send normal requests.
DNS is presently supported on Windows, Linux, iOS and OSX, however not by Android.
Vulnerabilities:
Your server information could be collected by hackers when the service is queried in case of exposure of your mDNS to Internet. This information includes device MAC address, services that are running on the machine etc. For an attack preparation, hackers can make use of this information.
Also, the UDP dependence of mDNS makes it vulnerable to exploitation for performing the attacks of amplification. In this, the target IP address of the attacker could be spoofed for saturating it with your server’s mDNS replies.
How to check the vulnerability of the server?
For the purpose of querying mDNS service, following is the command that could be used as root from remote machine:
# nmap -Pn -sU -p5353 –script=dns-service-discovery <Your-server-IP>
Resolution:
The design of Multicast DNS is intended to be used inside local network. This reflects that direct exposure of this service should be avoided to Internet. In other words, it should not be exposed to the environment where it could be accessed directly by the untrusted clients.
For this issue mitigation and server protection, availability of different options is there such as:
- If the mDNS service is not in use then it should be disabled. This solution is both effective as well as easiest one.
- Firewall should be configured so that inbound connections could be filtered to the server UDP/5353. Also, only the hosts/ network IPs that are trusted ones should be allowed that demand access to mDNS service by contacting it.
Related – DNS Interview Q&A
Tag:services



