What is Cryptography? 3 Types of Cryptography Techniques
Introduction to Cryptography
Cryptography is crypto + graphy, where “crypto” means “hidden” or “secret” and “graphy” means “to write”.
Cryptography is a technique through which the information/data is communicated securely/secretly. This technique is irreplaceably essential in the present world of cyber-attackers and hackers. The Cryptographic technique uses a code/algorithm to transform the data/information into an encrypted form (i.e. Ciphered Text). This encrypted data reaches the destination in a hidden/encrypted form thereby preventing any threats of attackers/hackers.
The algorithm is made up of a large number of keys and combinations, thus making it hard to decode by the attackers. The information can only be read after decryption at the destination end through the encrypted key code.
Thus, the data/information remains completely hidden and integral throughout its transmission, and cannot be misused by any unauthorized bodies.
Techniques Used In Cryptography:
The two major techniques that are used in cryptography are:
- Encryption
- Decryption
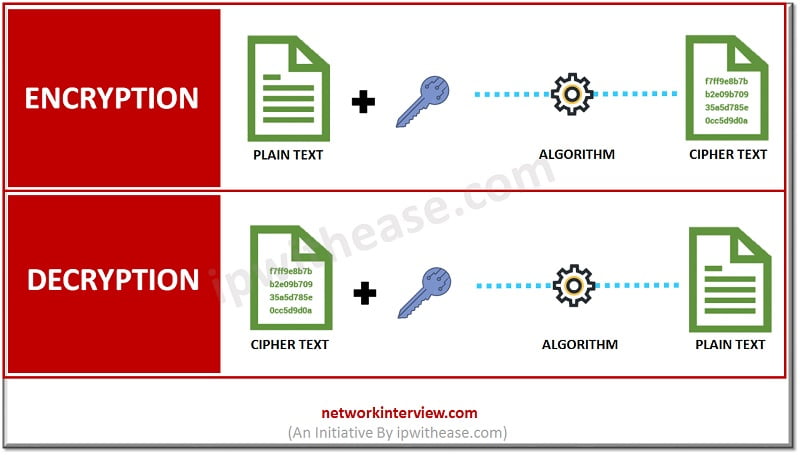
Encryption: It is the process through which the information is encoded. Thus, it converts plain text into ciphered text.
Decryption: It is the process through which the encoded information is decoded. Thus, it converts ciphered text back to the plain text.
Types of Cryptography
The three main types of cryptographic techniques are:
1) Secret Key Cryptography (SKC)/ Symmetric Key Cryptography:
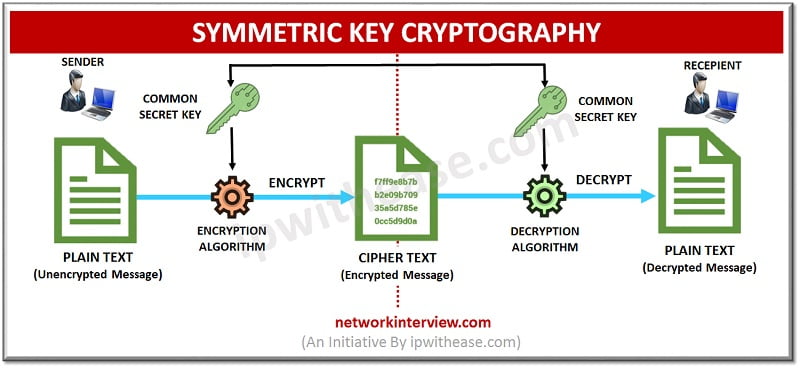
In this type, only one secret key is used for both the encryption and decryption, thus it is also called Symmetric Key Cryptography.
Benefit: It is simple and fast for encrypting large amounts of data.
Drawback: The key distribution between the sender and receiver is the critical part. As the key distribution should be done in highly secured manner.
2) Public Key Cryptography (PKC)/ Asymmetric Key Cryptography:
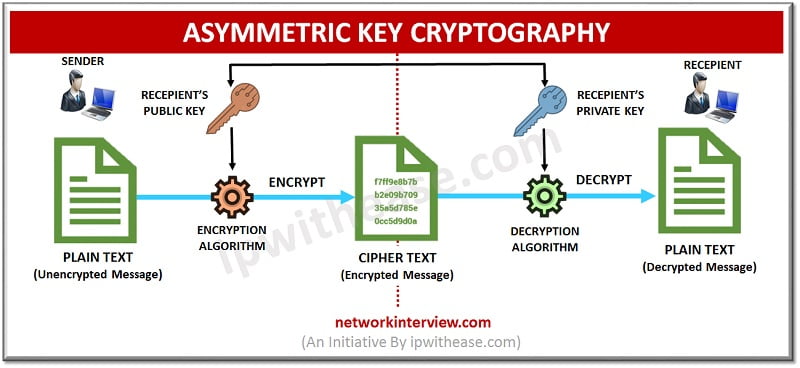
In this type two different keys are used, a public key is used for encryption and a private key is used for decryption, thus it is also called Asymmetric Key Cryptography. The public key can be accessed by anyone. And the private key can only be accessed by the owner. So, the information is encrypted by the sender using the receiver’s public key and the decryption of the message is done by the receiver using his/her private key. As the person doesn’t have access to the private key, the information remains confidential.
Benefit: Non-Repudiation can be achieved by using Asymmetric cryptography.
Drawback: It is much slower as compared to symmetric cryptography. It can only encrypt smaller pieces of data i.e. 2048 bits or smaller.
3) Hash Functions:
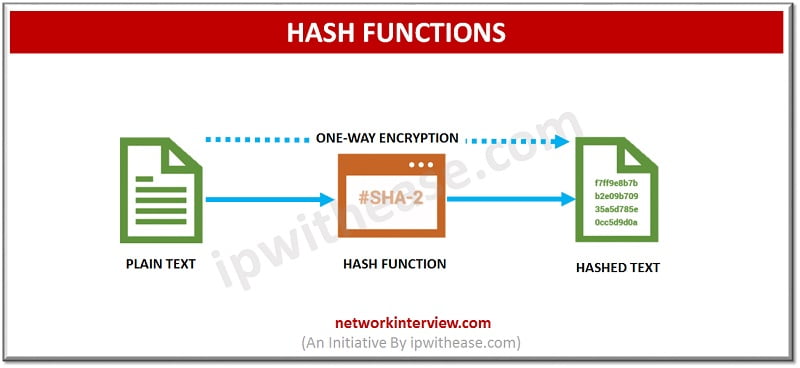
It is different from symmetric/asymmetric type of cryptography as it does not use any key. Moreover, unlike the first two types Hash functions is one-way encryption. A hash value of fixed length is assigned to the text. It is irreversible as the plain text is not recoverable from the hashed text.
Benefit: Hash functions are used to encrypt passwords by many operating systems.
Benefits of Cryptography
The main benefits of Cryptographic technique are:
- Confidentiality of Information: This technique provides a complete confidentiality of Information, as the information cannot be accessed by any unauthorized body.
- Integrity of Data: This also ensures the integrity of data during transmission, as no changes can be made to the data.
- Authentication: The cryptographic technique protects against any forgery/spoofing as only authenticated senders and users can access the data.
- Non-Repudiation: This technique also ensures non-repudiation service as there is no chance of denial once the digital signature is done.
Drawbacks of Cryptography
Apart from the various benefits of this technique, there are some drawbacks related to effective usage:
- Difficulty of Access: Sometimes a strongly encrypted may become difficult to access even for a legitimate user.
- Selective access control: Realization of selective access control is also not possible through cryptography.
- High- Cost: The cost of infrastructural set up of cryptography is quite high.
- Not Full-proof: Cryptography cannot provide full proof security against vulnerabilities like poor design, protocol or procedures. So, a defensive infrastructure set up is required.
Continue Reading:
What is Blockchain technology?
Tag:Security



