What is an SSH Key? An Overview of SSH Keys
Modern cloud infrastructure highly relies on SSH keys and they are the foundation of secure access management in the cloud ecosystem. The SSH keys establish secure communication between servers and clients and provide faster access as compared to traditional password-based authentication techniques.
SSH keys are generated in pairs of public key and private key wherein public key is publicly shared with server and private key is stored securely on user system. Public key is like a lock we use to secure our home and private key is like a lock key which the house owner only owns. SSH keys are hard to steal or guess hence they are more secured to traditional password-based authentication mechanisms which are slower, cumbersome and prone to compromise.
In this article we will learn more in detail about SSH key, what is the purpose of SSH keys and their key characteristics.
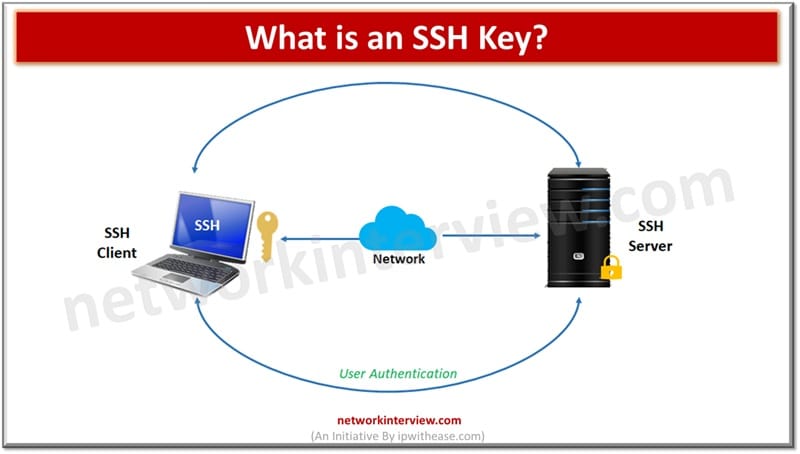
SSH Key
SSH (Secure Shell) is used to manage networks, operating systems and configurations. It is widely used by all major cloud providers such as Amazon, Google, Microsoft and others. Almost every organization uses it, a modern counterpart of traditional password-based authentication mechanisms they offer computer independent services. Access grant and control who can access what, provisioning and terminations of user accounts, credentials all is handled by SSH keys.
SSH key authentication is an identity proving mechanism which incorporates a pair of keys for said purpose. When a user tries to login into the system the server issues a challenge using the public key. Response to challenge is provided by the user’s private key. If the response matches access is granted. If responses do not match then access is denied. SSH is used to protect user identity, encrypted messages and establishment of secure connectivity between server and client. The complete process is totally automatic without any manual intervention.
Advantages of using SSH keys instead of passwords
A high level of security is provided by SSH keys compared to its counterpart a traditional password-based authentication mechanism. as keys are complex and longer difficult to break and more resilient to brute force attacks or password guesses.
Access management is simpler as users need not remember multiple passwords across systems. With SSH key authentication users require only a private key.
Asymmetric encryption offers better protection as even if someone gains access to the public key still they cannot identify the corresponding private key to complete authentication requirements.
How to use SSH Keys?
SSH keys can be generated, stored and managed across operating systems to enable secure access to remote servers. To generate SSH keys on Linux/Mac and Windows systems we can use below command.
For Linux-Mac systems use ssh-keygen command
Mention encryption key such as RSA
Choose secure passphrase for private key and save generated keys in a folder
For Windows systems we can download and install SSH client such as PuTTY / GitBash
Best Practices to Use and Manage SSH keys
- Periodic Updation of SSH keys to ensure protection against unauthorized access
- Periodic rotation of keys to prevent breaches
- Monitoring and record SSH keys last update and rotation details
- Establish a schedule or reminder for SSH key updates or rotation
- Establish an automated process for SSH keys update or rotation instead of relying on manual effort
- Check vulnerabilities on your SSH keys
- Based on role and responsibilities , SSH keys access is to be granted to authorized users only
- Have a naming convention in place for SSH keys so as to identify the purpose they are meant for
- Configure firewall rule and restrict access of SSH keys from specific IP addresses
- Enforce strong passphrase policies for SSH keys
- Use RBAC (Role based access management) for granular management of SSH keys use
- Review and revoke not required SSH keys
- Setup logging and monitoring mechanism for SSH keys usage
- To have an additional layer of security on top of SSH keys consider implementing MFA (Multi-factor authentication) or 2FA (2 factor authentication)



