
WEP vs TKIP vs CCMP: Understanding what each encryption technique offers
Understanding each Encryption Technique
When we dive in-depth to explore more about wireless key management and encryption technologies, then we would find that network protocols play an imperative part in it. As we are dealing with the technologies that are effectively used for the encryption feature on wireless networks, it is essential that they precisely cover trusted access, swift transmission across the points, confidentiality and privacy.
Introduction
There are different types of protocols that are successfully used in the field of encryption technologies and wireless key management. But here, our emphasis is going to be on three specific types of protocols and what they can offer to us against one another. The comparison is going to be made in between WEP vs TKIP vs CCMP and what are the specializations that they carry when they play against each other on specific parameters.
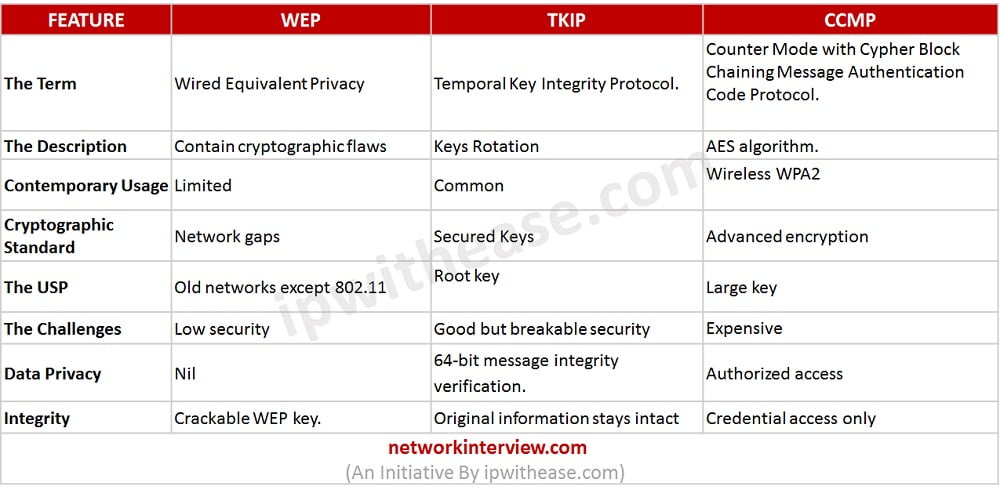
WEP is short for Wired Equivalent Privacy and it is one of the protocols that are not commonly used these days.
TKIP is abbreviation for Temporal Key Integrity Protocol.
The 3rd is the list is CCMP. It is one of the most common technologies that are employed in WPA2 on modern-day basis. It stands for Counter Mode with Cypher Block Chaining Message Authentication Code Protocol.
One of the key reasons behind limited usage of WEP is that some of the cryptographic flaws are not conducive for a long term from the wireless network standpoint. In contrast to WEP, TKIP has been specially built in order to rotate the keys around, so that the users do not face the same problems in encryption that they may run across in obsolete WEP protocol.
Further, CCMP is used in conjunction with Advanced Encryption Standard (AES) algorithm. Infact from usage perspective, WEP protocol is mostly non-existent in the current modern wireless networks unlike TKIP which is commonly used. CCMP may be used, however it is generally referred to when the user is setting up wireless network in the form of WPA2 and in terms of parentheses it might have TKIP.
When talking about cryptographic standard, one of the successes of the TKIP Cryptographic Standard over WEP standard is that it creates the keys together. The key made in this protocol is more secure because it changes on a constant basis. CCMP carries more advanced encryption standard in comparison of both the other technologies discussed.
When USP (Unique selling point) of these encryption protocols compared, the root key in case of TKIP is mixed with the initialization vector in order to achieve unique nature of security. The ability of sequence countering is one of the most effective tactics to avoid reply attacks. CCMPs value add is that it has a larger size key and comprises of a larger block size to conduct the encryption.
In terms of data integrity, WEP has data confidentiality which is better than traditional wired network, but it can only safeguard your network against average users. TKIP implements a 64-bit message integrity verification. It simply denotes the fact that the information transferred could not be changed in somewhere between the conversation. Whereas, in case of CCMP, only certain people are authorized to receive the information and the information is only shared when the user on the other end of the network is really a genuine one.
Related – Wired vs Wireless
Comparing WEP vs TKIP vs CCMP : Encryption technique
Conclusion
We made the comparison above WEP vs TKIP vs CCMP, to reach the verdict that for the older hardware WEP and TKIP are the better options. But if you can upgrade to newer hardware, facilitate more computing resources and data safety is utmost priority then CCMP is a considerable choice!
Continue Reading:
What is Blockchain technology?
Tag:comparison, Security



