What Are the different types of Network Security Devices & tools
There are several aspects to security and Network Security is one of the key components in this. Network security protects networks from unauthorized access and threats. Organizations deploy or adapt measures to protect networks from malicious attackers. Network security devices are meant to protect networks from insider and outsider attacks.
These can be physical or virtual or software components and sometimes some act as passive devices which only inform about intrusions and sometimes active devices which block suspicious traffic and third category is of preventive devices which are used to scan networks and identify potential security threats.
In today’s topic we will look more in detail about different types of network security devices and tools, and understand their purpose and use.
Network Security Device Types
Network security devices could fall in the category of
- Active,
- Passive and
- Preventive devices broadly.
Depending on their nature either they detect threats and inform, take actions on identified threats, or perform proactive scans to detect potential security loopholes. Sometimes a device might combine capabilities of different types of devices into one device for unified network threat management.
NAC
Network access control is meant to control access to diverse network assets. These are designed to manage authorization functions and access authentication for specific users only.
Firewall
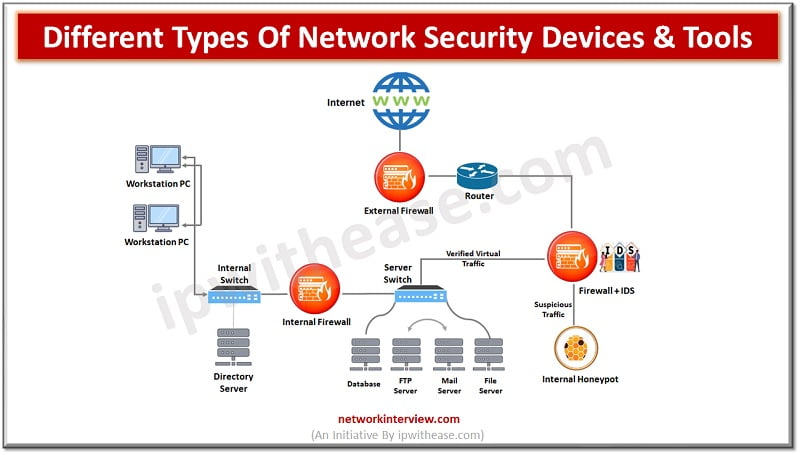
The most commonly used network device which is used as the first line of defense by organization is firewalls. Firewall is a network security management system which regulates network traffic based on protocols. Firewall acts as a barrier between trusted internal networks and the Internet. In other words, we can call it a gateway to the outside world or Internet.
Firewalls could be software, hardware, or virtual appliances. Firewalls block traffic based on IP address, port, protocols, current state and at times they do combine other functions also such as DHCP for dynamic allocation of IP address, or a remote access to private network via secure authentication certificates and logins.
Web Application Firewall
Web Application firewall (WAF) are similar to regular firewalls only but majorly used in cloud hosted environments. They block traffic based on suspicious activities or predefined rules But as the name specifically they help to protect applications by filtering and monitoring HTTP traffic between web applications and Internet , in other words a WAF operates at layer 7 of OSI model and not designed to protect all kinds of attacks.
IDS & IPS
Intrusion detection systems (IDS) and Intrusion prevention systems (IPS) are appliances which monitor network traffic based on rules and monitor malicious activities in the network and log information about such activities and take actions such as blocking port, dropping malicious traffic, isolating infected machines etc.
The alarm is set to trigger information regarding any malicious activity in the network, dropping of packets, resetting the connection to protect IP address from blocking, intrusion detection systems also perform correct cyclic redundancy checks (CRC), prevent TCP queueing issues and clean up unwanted transport and network layer options.
Content Filtering Devices
Content filtering devices screen mails and web pages and generate access denied action if undesirable or unauthorized web page or email is encountered. Content is scanned for multiple categories such as pornography, hate speech, shopping, and marketing contents etc. Content filtering could be performed at multiple levels such as web filtering, email filtering, web page and email screening etc.
Anti-malware Software
Anti-malware software lets administrators identify, block or remove malware. Malware policies can be customized to identify both unknown/ known malware sources. It constantly searches for network vulnerabilities and includes data leakage prevention tools also, IP blacklisting, anti-spyware and antivirus software, outbound traffic proxies, egress filtering etc.
VPN Gateways
VPN gateways securely connect two or more devices or networks together in a VPN infrastructure. A VPN gateway could be a server, router, firewall or any other device with internetworking and data transmission capability. VPN gateways are configured to pass or block or router VPN traffic.
Network Devices Backup & Recovery
Network devices backup and recovery is usually performed using configuration management tools else it would be difficult to individually go to each network device and perform backups in larger setups. Configuration management tools help to schedule devices backup, track user activity, and spot changes in configurations versions via a centralized GUI web interface
Continue Reading:
6 Types of Firewall: Network Security
VPN vs Proxy vs Tor: What’s the Difference?
Tag:Security



