What is SAST (Static Application Security Testing) ?
Introduction to SAST
Application security testing makes applications more resilient to security threats and identifies weaknesses and vulnerabilities in application source code. Initial days software code testing was done manually however as organizations matured and software’s became modular in nature and more and more open-source components being used large number of unknown vulnerabilities started surfacing in, the threat vector spectrum is broadened. The need was felt for automated testing tools so organizations started using a wide variety of tools to test the source code before applications are launched in production environments.
Today we will learn about one such software testing methodology which is a white box testing technique and known as Static application testing technique.
About Static Application Security Testing
SAST is an integral part of application security for more than 15 years. Considering application vulnerabilities will continue to be the most common external cause of attack it is safe to say SAST will have a long road ahead. Year 2019 report of Forrester shows the majority of external attacks were carried out by exploiting software vulnerabilities (42%) contribution or via web applications which contributed 35% to breaches.
It is a white box testing methodology where source code is analysed from inside out while other components are at rest.
Pros and Cons of Static Application Security Testing
PROS
- Integration of security testing at the initial stages of software development helps to detect vulnerabilities in proprietary code in the design stage itself when they are easy to resolve and saves costly efforts of addressing them closer to release date or when application is already released
- Helps development teams to comply to secure coding practises
- Automated SAST workflows help to easily detect common vulnerabilities like buffer overflows, SQL injection, cross site scripting etc.
CONS
- SAST don’t cover run time issues, configuration problems, issues with authentication, access control, cryptography which are tough to detect in pre-production source code. It does not cover open-source vulnerabilities which comprises of 60% to 80% of source code now a days
- SAST results throw a high number of False+ves, costing development and security teams to spend a lot of time and effort to sort out false alarms and only work on genuine issues. 53% of the issues detected are non-existent (False+ves)
- One scan can take several hours for a large code to scan. Once the results are displayed, they require analysis which means additional efforts from development and security teams. SAST points out only potential vulnerabilities but how they will be exploited or is it really a risk is let to developers to figure out
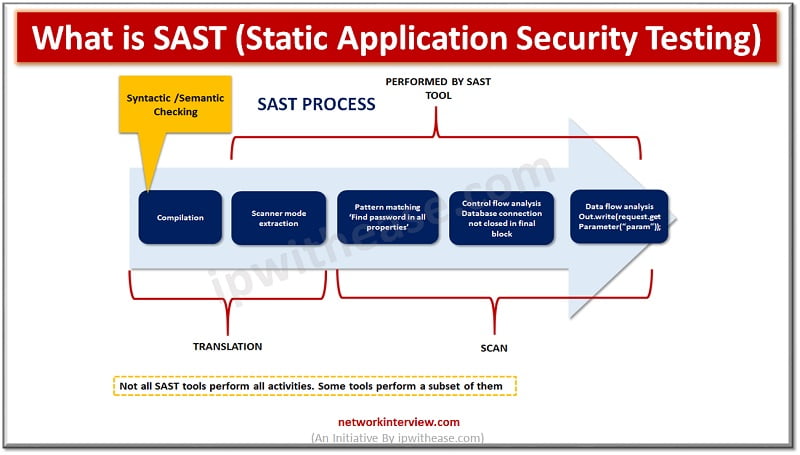
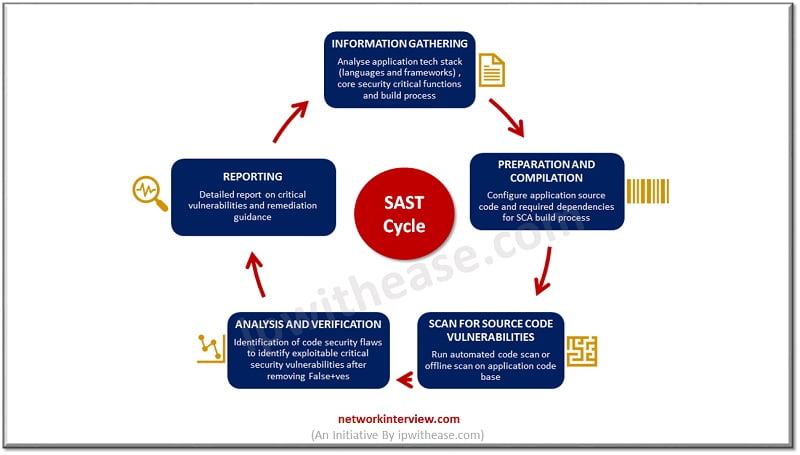
How Static Application Security Testing works?
Static Application security testing tests source code at rest, without running it. It is usually implemented at the coding and testing stages of development, integration in CI servers and into IDEs. It scans organizations in house code and design to detect flaws that indicate weaknesses which could lead to security vulnerabilities in software.
SAST scans are based on a predefined set of rules which define the coding errors in source code which are required to be fixed and assessed. SAST scans are designed to define some of the most common security vulnerabilities such as SQL injection, input validation, stack buffer overflows and so on.
SAST is integrated in SDLC (Software Development life cycle) usually to help to improve organizations security appetite.
How to choose the right Static Application Security Testing tool?
There are many products available in the market offering SAST capabilities. So how to choose right tool once can use below criteria:
- Language support – which languages organization use SAST tool used should offer complete coverage of those languages
- Vulnerabilities coverage – make sure the SAST tool chosen covers at least all of OWASP’s top ten web application security vulnerabilities.
- Accuracy – Accuracy of SAST tool to be checked before making the choice
- Compatibility – SAST tool should integrate with frameworks already used so that it can be integrated with ease into SDLC
- IDE integration – SAST tool that can be integrated with your IDE can save valuable remediation resources
- Ease of Integration – SAST tool which is easy to setup and integrates seamlessly
- Scalability – SAST tool should be scalable to support more projects and developers going forward
Conclusion
SAST is a static code analysis tool and acts like a building watchman similar to building watchman checking for unlocked doors and open windows that can provide entry to an intruder, a static code analyser looks like the source code to check for coding and design flaws that could allow for malicious code entry point.
Continue Reading:
What is Penetration Testing or Pen Test?
Tag:Security



