Palo Alto Security Profiles and Security Policies
Below are the key profile types provisioned in Palo Alto Firewall. Lets discus all the profile types one by one –
Palo Alto Security Profiles & Security Policies
While security policy rules enable to allow or block traffic in network, security profiles scans applications for threats, such as viruses, malware, spyware, and DDOS attacks. When traffic matches the rule set in the security policy, rule is applied for further content inspection such as antivirus checks and data filtering.
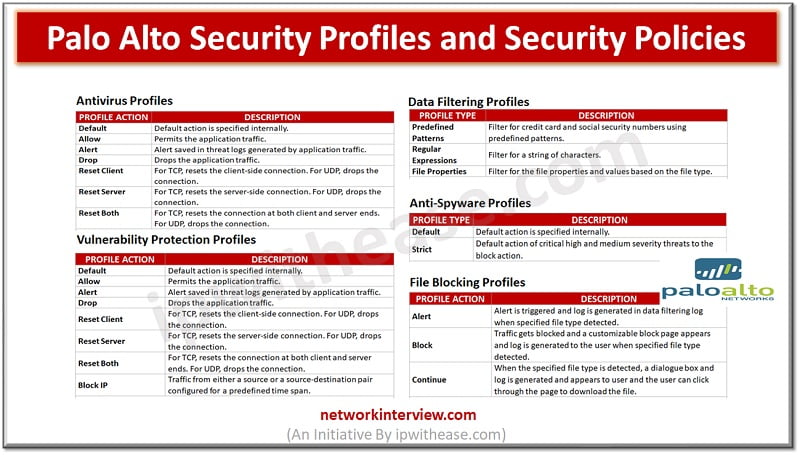
Antivirus Profiles
Antivirus profiles blocks viruses, worms, and Trojans as well as spyware. Palo Alto protects user data from malware without impacting the performance of the firewall. This profile scans for a wide variety of malware in executables, PDF files, HTML and JavaScript viruses and compressed zipped files.
Anti-Spyware Profiles
Anti-Spyware profiles block spyware on hosts, allowing to detect malicious traffic leaving the network from infected clients. Anti-Spyware profile is applied on various levels of zones. Profile can be customized or one of the following profiles types can be selected when applying Anti-Spyware to a Security policy rule:

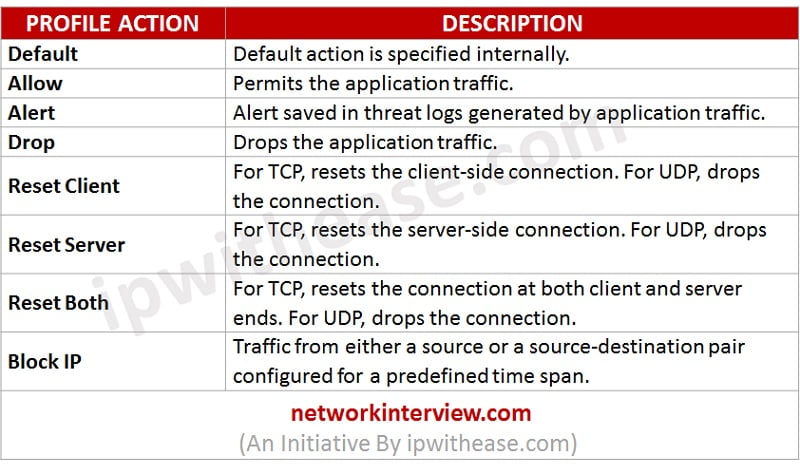
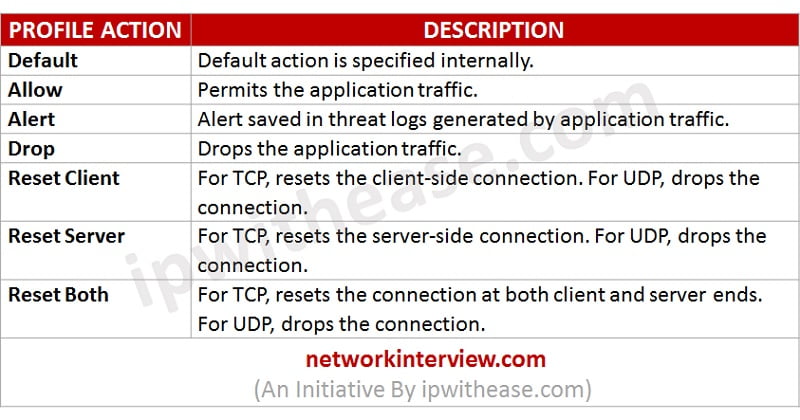
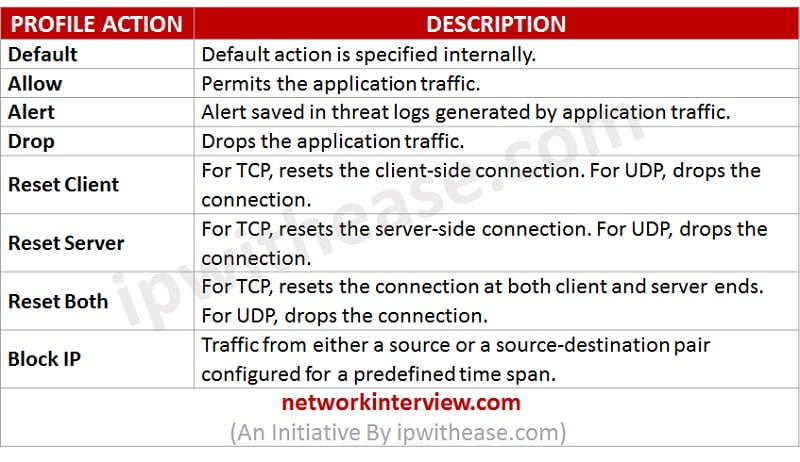
Vulnerability Protection Profiles
Vulnerability Protection profiles protects from unauthorized access to the systems. It protects against threat entering into the network. For example, it helps in protection against buffer overflows, illegal code execution, and other attempts to exploit system vulnerabilities. Default option in vulnerability protection profile protects clients and servers from all the critical high and the medium severity threats. When the firewall detects a threat event, the following actions can be configuring:
URL Filtering Profiles
URL Filtering profiles enable to monitor and control how users access the web over HTTP and HTTPS. By default, firewall have default profile that is configured to block URL like malware, phishing and adult content. New action can be added in default URL profile that will have all categories set to allow for visibility into the traffic in network. Customization of newly added URL profiles and add lists of specific websites that should always be blocked or allowed, which provides more granular control over URL categories.
Data Filtering Profiles
Data filtering profiles protect sensitive information like credit card details or social security numbers when leaving a protected network. Data filtering profile filter on keywords, like sensitive project name or the word confidential. Custom data pattern can be created and then attached to a Data Filtering profile. Create data pattern objects based on following:

File Blocking Profiles
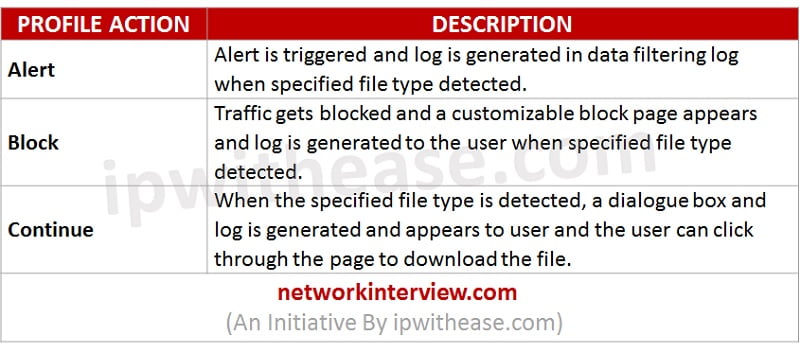
File blocking profiles are used to block particular file types over particular applications and in the defined session flow direction (inbound/outbound/both). Alerts can be set on upload and/or download on an application. In file blocking profile, custom block pages can be configured that will appear when a user attempts to download the specified file type. File blocking profiles allow the user to take a moment to consider they want to download a file. Custom File Blocking profile can be defined or we may choose one of the following:
- Basic File Blocking: Security policy allows traffic less sensitive. It blocks traffic that are malware. In this profile, files are blocked while uploading and downloading like executable .scr, .cpl, .dll, .ocx, .pif, and Java files like .class, .jar, and .chm, .hlp and other critical malicious file types having .vbe, .hta, .wsf, .torrent, .7z, .rar, .bat. Prompts appears on user’s screen to acknowledge when they attempt to download encrypted .rar or encrypted .zip files.
- Strict File Blocking: This allows access to your most sensitive applications. Add on to basic file blocking, it blocks additionally .tar, multi-level encoding, .cab, .msi, encrypted .rar, and encrypted .zip files.
Wildfire Analysis Profiles
Wildfire analysis profile is used to forward unknown files or email links. Analysis are based upon application file type and transmission direction ie whether for upload or download. Files or email links matching the profile rule are forwarded either to the Wildfire public cloud or the Wildfire private cloud, depending on the analysis location defined for the rule.
DoS Protection Profiles
DoS (Denial of Service) protection policies allow to control the number of sessions between interfaces, zones, addresses, and countries based on aggregate sessions or source and/or destination IP addresses. Following are two DoS protection mechanisms in Palo Alto Networks firewalls.
Flood Protection: In this method, packet is flooded in the network and as a results many sessions are half-open with service being unable to serve each request. This method protects user from this kind of attack.
Resource Protection: This method is used to prevent session exhaustion attacks. Large number of hosts are used to establish as many fully established sessions and henceforth they consume system’s resources. This method is used to protect from resource usage.
Zone Protection Profiles
Zone Protection Profiles protect the network zone from attack and are applied to the entire zone. In this profile, packets per second (pps) thresholds limits defined for zone, the threshold is based on the packets per second that do not match a previously established session.
Conclusion on palo alto security profiles and security policies:
Security policy rules allow or block traffic in network, while security profiles scans the applications for threats, such as viruses, malware, spyware, and DDOS attacks.
Continue Reading:
FortiGate Firewall Policy: Rules, Types & Configuration
Checkpoint Firewall Policy: Rules & Configuration



