What is Network Pruning? Common Network Pruning Techniques
Network pruning is a process of optimizing or simplifying a network by removing unnecessary or redundant elements to improve performance, efficiency, and manageability. Here are some common network pruning techniques:
Network Pruning Techniques
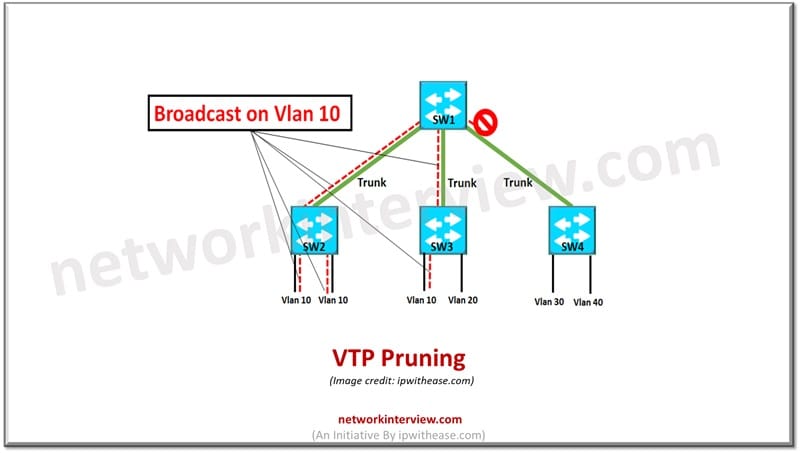
1. VTP Pruning
VTP (VLAN Trunking Protocol) pruning is used in Cisco networks to reduce unnecessary VLAN traffic over trunk links. It ensures that only the necessary VLAN information is propagated across the network.
How it works?
When VTP pruning is enabled, a switch prevents the broadcast, multicast, and unknown unicast traffic of VLANs from traversing trunk links if the downstream switches do not have any ports assigned to those VLANs.
Benefits:
Reduces unnecessary traffic and increases the available bandwidth on trunk links.
2. Route Summarization
Also known as route aggregation, this technique involves combining multiple IP routes into a single summary route to reduce the size of routing tables.
How it works?
Instead of advertising multiple specific routes, routers advertise a summarized route that represents multiple subnets. This reduces the complexity of routing tables and cuts down on routing updates.
Benefits:
Simplifies routing tables, reduces CPU load on routers, and optimizes memory usage.
3. Spanning Tree Protocol (STP) Pruning
STP pruning helps reduce the number of active links in a network while maintaining redundancy.
How it works?
STP identifies redundant links in a Layer 2 topology and puts certain ports into a blocking state to prevent loops. The active forwarding paths are pruned to create a loop-free network.
Benefits:
Reduces the chances of broadcast storms and optimizes the network topology.
4. Multicast Pruning
This involves limiting the distribution of multicast traffic to only those devices that are interested in receiving the traffic.
How it works?
Protocols like IGMP (Internet Group Management Protocol) and PIM (Protocol Independent Multicast) prune multicast traffic, ensuring it is only forwarded to the segments of the network where receivers are present.
Benefits:
Conserves bandwidth by limiting multicast traffic to relevant parts of the network.
5. Firewalls and ACL Pruning
Firewalls and Access Control Lists (ACLs) can be used to prune unnecessary traffic by blocking or restricting specific types of data.
How it works?
By applying strict firewall rules or ACLs, administrators can limit certain traffic (e.g., ICMP requests, unused protocols) from traversing the network, reducing load and security risks.
Benefits:
Enhances security, reduces unnecessary traffic, and lowers network congestion.
6. Link Aggregation Control Protocol (LACP) Pruning
LACP is used to bundle multiple physical links between switches into a single logical link to increase bandwidth and provide redundancy.
How it works?
By removing unnecessary or underused links in a bundle, LACP can optimize the network by pruning inactive links and maintaining only active ones.
Benefits:
Reduces the overhead of managing multiple individual links and ensures efficient use of available bandwidth.
7. Wireless Network Pruning
This involves removing underutilized or obsolete access points (APs) in a wireless network to optimize coverage and reduce interference.
How it works?
By conducting site surveys and monitoring network usage, administrators can remove or disable APs that contribute little to overall coverage or performance.
Benefits:
Reduces network interference, optimizes performance, and simplifies network management.
These network pruning techniques help optimize the efficiency of a network by eliminating redundant or unnecessary elements, leading to better performance and more streamlined management.
Related FAQs
Q.1 What is network pruning in VLANs, and why is it important?
Network pruning, particularly VLAN Trunking Protocol (VTP) pruning, is a method to prevent unnecessary broadcast, multicast, and unknown unicast traffic on trunk links for VLANs that are not actively used on those links. It optimizes bandwidth utilization, improves network performance, and reduces CPU load on devices.
Q.2 How does VTP pruning work in a network?
VTP pruning dynamically removes VLANs that do not have active hosts on downstream switches from the trunk ports. The pruning process uses VTP advertisements to identify the VLANs that are active on each switch. If a VLAN does not have an active member on a trunk, it is pruned, stopping the traffic for that VLAN from traversing the trunk.
Q.3 What are the limitations of VTP pruning?
- Only VLANs 2-1001 are affected: VTP pruning does not prune traffic for VLAN 1 or extended VLANs (1006-4094).
- Manual Configuration Required: VTP pruning must be explicitly enabled and does not work in VTP transparent mode.
- Limited to Cisco Devices: VTP pruning is a Cisco-specific feature and does not apply to devices from other vendors.
- Inter-VLAN Traffic: It does not affect inter-VLAN routing traffic, which still traverses routed links.
Q.4 How is VTP pruning enabled on a switch?
To enable VTP pruning:
- Ensure the switch is in VTP server or VTP client mode (not transparent).
- Use the command: Switch(config)# vtp pruning
- Verify pruning status with: Switch# show vtp status
Look for the “VTP pruning” field to confirm it is enabled.
Q.5 What are best practices for using VTP pruning?
- Enable only when necessary: Use VTP pruning in large networks with many VLANs and trunk links to avoid unnecessary traffic.
- Backup Configuration: Before enabling pruning, ensure that the VLAN database and switch configurations are backed up.
- Use Consistent VTP Versions: Ensure all participating switches use the same VTP version to avoid compatibility issues.
- Monitor Traffic: Use monitoring tools to confirm the impact of pruning and verify that legitimate traffic is not inadvertently pruned.



