Nessus: Network Vulnerability Scanner
Network Vulnerability
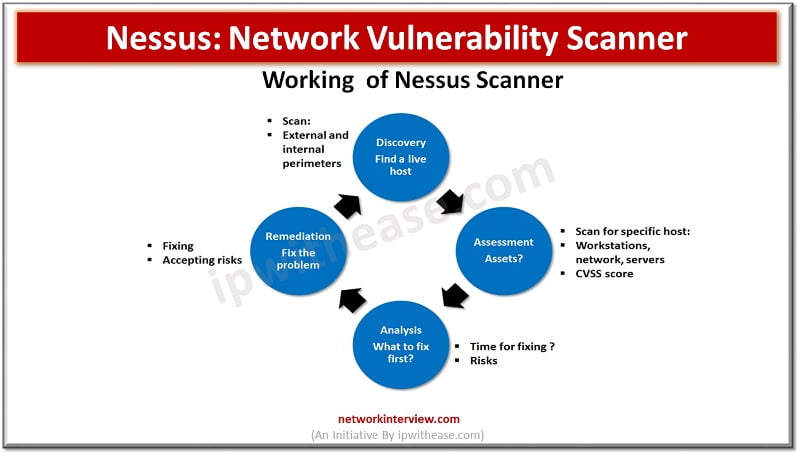
Vulnerability management is all about identifying, evaluating, treating, and reporting security vulnerabilities in systems and software and it is vital for organizations to prioritize potential threats and reduce the ‘attack surface’. There are many vulnerability management scanners / tools available in the market which help to identify and fix potential vulnerabilities , identify inventory / asset , automated patching to fix vulnerabilities etc.
Today we look at ‘Nessus’ Vulnerability scanner which is a very popular and widely used vulnerability scanner by small, medium, and large enterprises. We will explore more about its features, architecture, and use cases.
Nessus: The Network Vulnerability Scanner
Nessus was founded by Renuad Deraison in 1998 to provide the network community a free remote security scanner. In October 2005 Tenable network security changed Nessus 3 to a proprietary (closed source) license. It is free of cost for non-enterprises. It is one of the most widely used vulnerability assessment products. Over the last 15 years it had evolved from only vulnerability scanner to include assessment and auditing features such as auditing of configurations, compliance auditing, patch auditing, control systems auditing, and mobile devices auditing.
It is a remote security scanning tool which scans a system and raises alert when it discovers any vulnerabilities which malicious hackers can use to gain access to any system connected to networks.
Nessus vulnerability scanner includes scan capabilities for network devices (Juniper, Cisco, firewalls and printers), virtual hosts (Vmware) , operating systems (Windows, Mac, Linux, Solaris, BSD, Cisco iOS, and IBM iSeries), databases (Oracle, MS-SQL, MySQL, DB2, Informix/DRDA, PostgreSQL) , and web applications (Web servers, web services and OWASP vulnerabilities).
Nessus provides functionalities such as
- Basic network scans,
- Malware scans,
- Mobile device scans,
- Host discovery ,
- Policy auditing,
- Drown detection and
- PCI external Scans
Nessus stores and manages all its security vulnerabilities through a system of plugins which the security team can use to scan its network to prevent intrusions and denial of services.
The vulnerability scan performed by Nessus uses programs written in NASL – Nessus Attack Scripting Language – known as plugins (Currently it has 50,000 plugins).
Features of ‘Nessus’
- Client/server architecture
- Provides remote and local security checks
- Audit antivirus configurations
- Performs sensitive data searches to look for credit card, social security number etc.
- Can call hydra (external tool) to launch dictionary attacks
- Compatible across multiple platforms (Windows, Linux, Mac OS X)
- Supports port scanning (SYN Scan, TCP Connect etc.)
- High speed and deep scanning
- Customized reporting to sort vulnerabilities or hosts . creation of executive summary and compare scan results
- Monitoring with targeted email notifications of scan outcome, remediation recommendations and scan configuration improvements
- Scanning for IPV4 /IPV6/ hybrid networks
- Un-credential vulnerability discovery
- Credential based scanning for system hardening and missing patches
- Configuring audits
Pros and Cons of ‘Nessus’
PROS
- Highly accurate scanning with low false +ves (Per 1 million tests, the device has just .32 errors)
- Compressive and deep scanning capabilities
- Highly scalable to 100 to 1000 of systems
- Ease of deployment and maintenance
- Low cost to administer and operations
- Common vulnerabilities and exposure coverage of around 47,000
- Facilitates group testing
- Built in scan templates
CONS
- Highly priced for commercial use not viable for smaller organizations
- Does not allow to check local security policies of remote systems
- Network overload could be a potential drawback
- Does not offer asset tagging and risk management
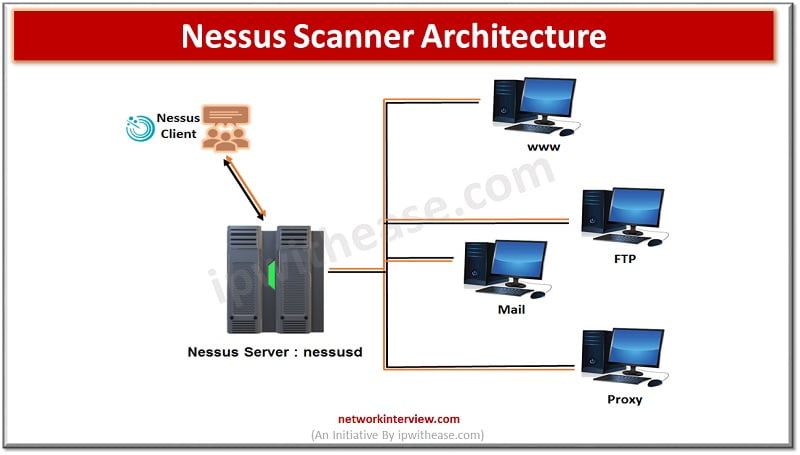
Nessus Architecture
Nessus is based on Client / Server model
The Nessus server : nessusd
- Responsible for doing vulnerability tests
- Listen to incoming connections from Nessus clients that end users use to configure or launch specific scanning
Nessus allows to perform scans to :
- Detect vulnerabilities that allow a malicious user or hacker to control and access sensitive data
- Misconfigurations : open mail relay and missing patches
- Denial of service against TCP/IP stack (mangled packets)
- Preparation for PCI DSS audit
Continue Reading:
Observium – Network Management & Monitoring
5 top Reasons your Organization needs an effective Network Monitoring Software Solution
Tag:services



