Introduction to NSX Intelligence
Data centres operations be it from cloud or on premises network is the backbone of these infrastructures which supports businesses starting from application delivery to security. As workloads are changed, migrate, evolve networking technologies too need to match the pace. Issues of ransomware, data loss and data theft are on rise and traditional approach to borderline security using traditional firewalls over the edge had shown some serious vulnerabilities once breached.
In this article we will learn more about NSX, VMware introduced zero trust security, its features, use cases and so on.
About NSX Intelligence
Many organizations use combination of security systems such as intrusion detection or prevention systems, or other traffic analysis engine to monitor data transfer at key points. As speed of network on rise so is the cost of intrusion detection and intrusion prevention systems and resources required to monitor the traffic is also grown up exponentially.
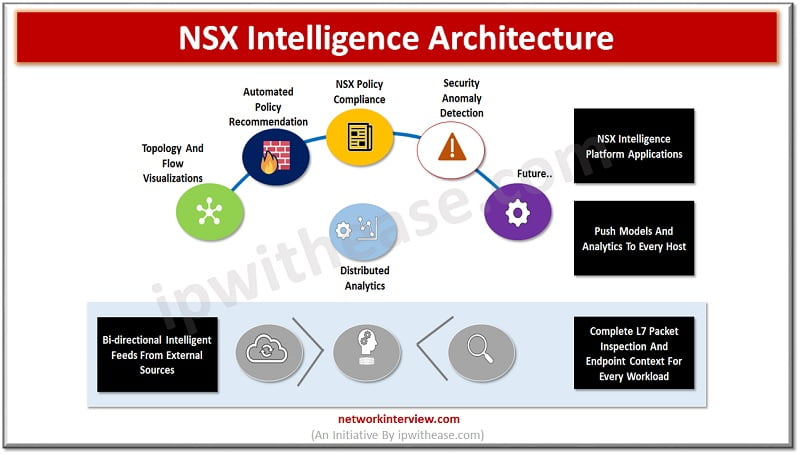
NSX offers an intelligent analytical security policy engine which applies policies all across hosts in a distributed manner rather than monolithic approach to intrusion detection. This eliminates choke points and enable all hosts to share the analytical load by ensuring all traffic is monitored without affecting any specific host or workload.
Microsegmentation in NSX
NSX intelligence takes Microsegmentation to next level. It examines what VMs talk to each other rather than just dictating rules regarding what they are talking. NSX intelligence scales horizontally rather than vertically so it can scale without limit or restricting production traffic.
Application delivery and Load balancing in NSX
NSX advanced load balancer is an acquisition from AVI networks in year 2019. It is a software defined platform which provides multi-cloud balancing, application acceleration and caching across bare metal servers, Virtual machines and containers.
Features of NSX Intelligence
- Provides a user interface via a single management plane with NSX manager
- Close to real time flow information for workloads
- Correlates live or historic flows, user configurations and workload inventory
- Ability to view past information on flows, user configurations and workload inventory
- Automated Micro segmentation planning by recommendation on firewall rules, groups and services
- Helps to visualize and gain insight into every flow across data center with stateful layer 7 inspection
- Reduction in tool sprawl and improved collaboration between infrastructure and security teams
- Single click deployment for virtual appliance
- Elimination of overhead of duplication of packets
- Inventories of all endpoints and traffic flows and consolidation of metadata and configuration data from NSX
- Auto generation of rules to micro segment applications
- Packet processing and workload analysis is distributed to each hypervisor
How NSX works?
The NSX intelligence data platform gets stream from NSX-T manager and from the ESXi hosts which are prepared as NSX-T transport nodes. Flow send to every 5 minute interval which means flow and guest information is distributed and optimized directly at source and agent is optional. The NSX intelligence appliance will deployed from NSX-T manager GUI and is managed and monitored from there.
Installation of NSX
NSX intelligence requires NSX-T version 2.5. The NSX intelligence comes as .tar file and contents required to be extracted and placed on a web server which can be accessed by NSX manager cluster.
The NSX intelligence appliance must be deployed on ESXI managed by vCenter.
In NSX manager navigate to Plan & troubleshoot > Discover & take Action:
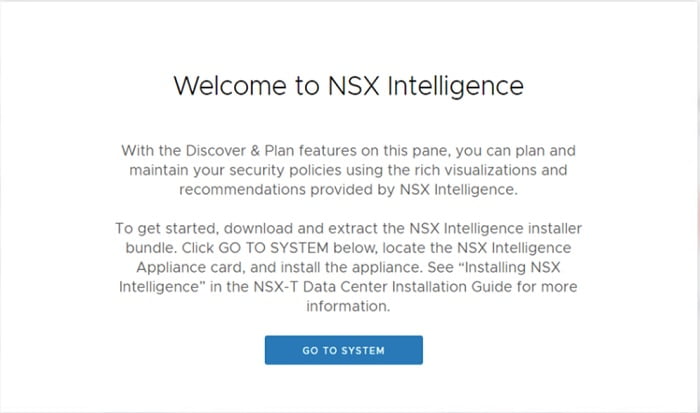
Click on Go To System scroll down on appliances page and click Add NSX intelligence appliance to start appliance deployment wizard:

Enter the URL for OVF file and appliance network configuration
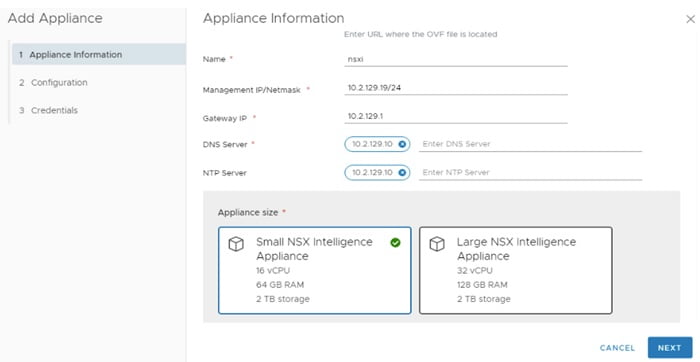
Configure vSphere details for the virtual appliance
Configure Appliance credentials at final step
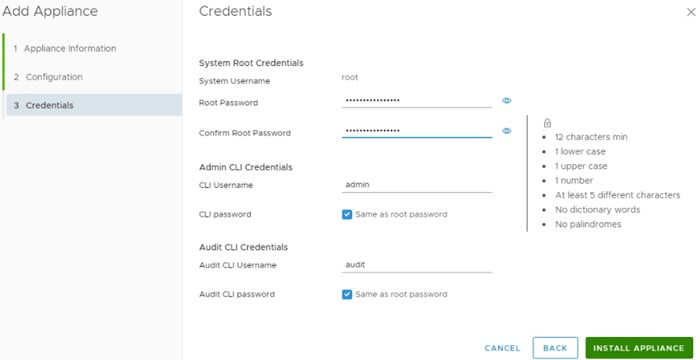
Click install appliance, deployment will take approximately 5-10 minutes
Continue Reading:
Hyper V vs VMware : Detailed Comparison
Tag:virtualization



