How to configure SSL Forward Proxy on SRX?
Network protection is enabled from malware by utilizing the SSL proxy component. It is used to prevent malware which is hidden in encrypted traffic. It is used to perform SSL encryption and decryption between server and end client in a non-transparent manner. Server authentication is used to guard against malicious transmissions by validating the web server identity. SSL forward proxy has keys to encrypt and decrypt the payloads.
Today we look more in detail about how to configure the Secure socket layer, i.e. SSL forward proxy on SRX firewall.
Configure SSL Forward Proxy on SRX
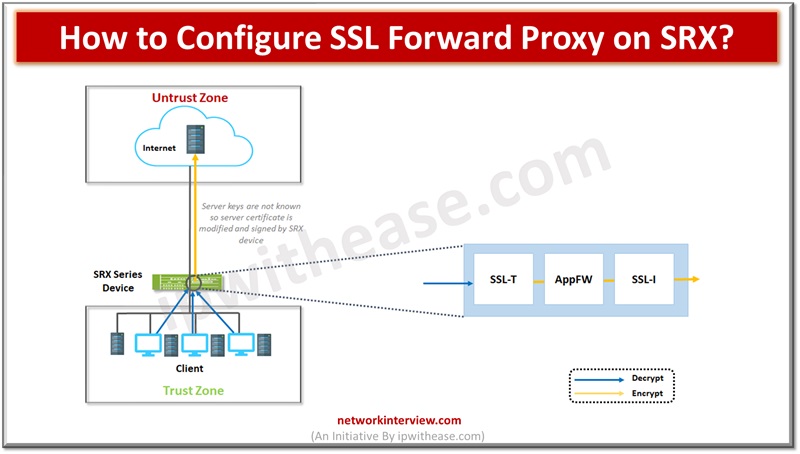
Below figure depicts how SSL forward proxy works on payload which is encrypted. With Application firewall (AppFW) is configured SSL forward proxy acts as SSL server to terminate SSL session from end client and start new SSL session.
To configure SSL forward proxy a list of steps to be taken:
- Root CA certificate configuration
- Load CA profile group
- Associate root CA certificate and CA profile group while configuring SSL proxy profile
- Security policy creation by defining input traffic match criteria
- Application of SSL proxy profile to security policy
- Creation of allowlists and SSL proxy logging (optional steps)
Root Certificate Configuration
Obtain root CA certificate using Junos OS CLI. Generation of a PKI public/private key pair (local digital certificate)
FW1@host1>request security pki generate-key-pair certificate-id certificate-id size size type type
Following combinations could be selected
1024 bits, 2048, 4096 (RSA / DSA only)
256 bits, 384, 521 (ECDSA only)
FW1@host1> request security pki generate-key-pair certificate-id SECURITY-cert size 4096 type rsa
FW1@host1> request security pki generate-key-pair certificate-id SECURITY-cert size 256 type ecdsa
Define self-certificate
FW1@host1> request security pki local-certificate generate-self-signed certificate-id certificate-id domain-name domain-name subject subject email email-id add-ca-constraint
Load CA profile group
In configuration mode apply loaded certificate to SSL proxy profile
FW1@host1> set services ssl proxy profile profile-name root-ca certificate-id
Import root CA as trusted CA for web servers.
Configure CA profile group
CA profile establishes the certificate information in authentication. Obtain a list of trusted CA certificates by loading group of CA profiles and attach the CA group to SSL proxy profile.
FW1@host1> request security pki ca-certificate ca-profile-group load ca-group-name group-name filename default
The dynamic updates of default trusted certificates are supported by SRX. To load a trusted list to the device used.
FW1@host1> request security pki ca-certificate ca-profile-group load ca-group-name group-name filename /var/tmp/IE-all.pem
Now attach trusted CA or trusted CA group with SSL proxy profile
FW1@host1> set services ssl proxy profile profile-name trusted-ca all
Import root CA into web browser
To import root CA certificate
Generate PEM format file
FW1@host1> request security pki local-certificate export certificate-id root-ca type pem filename path/filename.pem
Application of SSL proxy profile to security policy
SSL proxy is enabled within security policy as an application service. Create a security policy and mention match criteria for policy.
FW1@host1> set security policies from-zone trust to-zone untrust policy policy-name match source-address source-address
FW1@host1> set security policies from-zone trust to-zone untrust policy policy-name match destination-address destination-address
FW1@host1> set security policies from-zone trust to-zone untrust policy policy-name match application application
SSL proxy logging configuration
While configuring SSL proxy logging, you can configure partial or full options. SSL proxy logs contain logical system name, SSL proxy allow-lists, information about policy, information about SSL proxy to troubleshoot issues. All or specific events can be configured.
FW1@host1> set services ssl proxy profile profile-name actions log all
FW1/@host1> set services ssl proxy profile profile-name actions log errors
We can use enable-flow-tracing option for enablement of debug tracing
Continue Reading:
How to configure Juniper SRX Firewall? Step by Step Guide
How To Configure Juniper SRX Security Policy?
If you want to learn more about Juniper SRX Firewall, then please check our e-book on interview questions and answers related to Juniper SRX Firewall.
Tag:Juniper SRX, Security




