FortiGate Single Sign On: FSSO
Single Sign On & FortiGate Single Sign On
Single Sign On (SSO) is a process that allows users to automatically log into every application after being identified, regardless of platform, technology, and domain.
FortiGate Single Sign On (FSSO) is a software agent that enables FortiGate to identify network users to access security policies or provide VPN access. FSSO is a process which allows users to access multiple applications without having to re-authenticate.
Users who are already authenticated by the network can access applications without providing credentials multiple times.
- FSSO can identify the user’s user-id, IP address, group membership
- FortiGate allows access based on membership in FSSO group configured on Firewall
- Each FSSO method gathers login events differently
- FSSO method uses directory services, such as Windows Active Directory or Novell eDirectory
FSSO deployment depends on the server which provides Active Directory services.
Microsoft Active Directory (AD) – It uses a collector agent for FSSO, Domain Controller.
Working Modes
Two working modes for user sign-on activities on windows
- DC Agent Mode
- Polling Mode
FSSO DC Agent Mode-
This mode is the most recommended mode. DC agents monitor and forward user login events to monitor collector agents. A collector agent is another FSSO component. Collector agent is generally installed on Windows Server that is the member of the domain you are trying to monitor.
A consolidate of events received from a DC agent and then forwards them to FortiGate. Collector agents are responsible for group verification, workstation checks and FortiGate updates of login records.
FSSO collector agent can send domain security group, Organisational Units and Global security information to FortiGate Firewalls. It can also be customized for global DNS.
Ways to Configure FortiGate Single Sign On in the Network
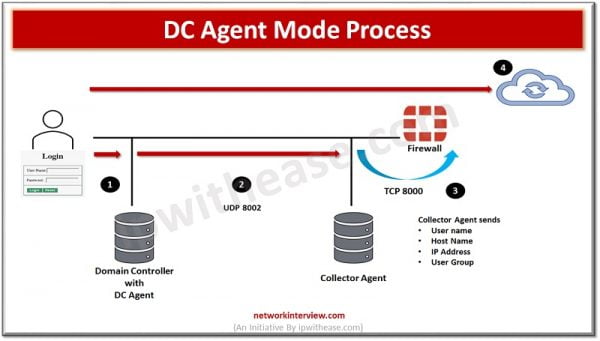
DC Agent mode- it is the most recommended mode in FSSO. One DC agent installed on each window DC. If any organisation has multiple DC which means multiple DC agents would require.
- User authentication done by Windows DC
- DC agents check the login event and forward the same to collector agent
- In a similar way collector agent forward the event log to FortiGate
- FortiGate knows the user based on IP address, so user doesn’t need authentication
Polling Mode – can be collector agent based or Agentless.
First lets check the feature of collector agent based-polling mode. Like DC Agent Mode collector agent based mode require a collector agent which is installed on Windows server.
- NO FSSO DC Agent is required
- The Collector Agent polls each DC for user login events in every few seconds. Collector Agent uses SMB -TCP-445 protocol to request the event logs and TCP-135, TCP-139 and UDP-137 as fallbacks
- Installation is less complex than other modes which reduces maintenance
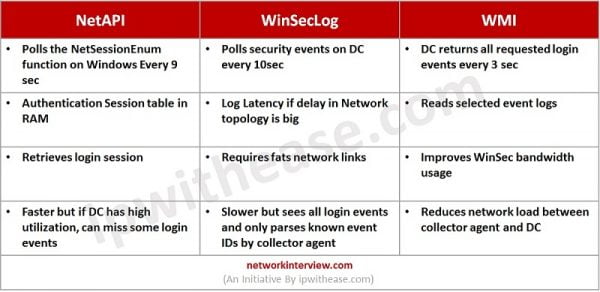
- Polling Mode methods commonly users are
- NetAPI
- WinSecLog
- WMI
Collector Agent-Based Polling Mode Process
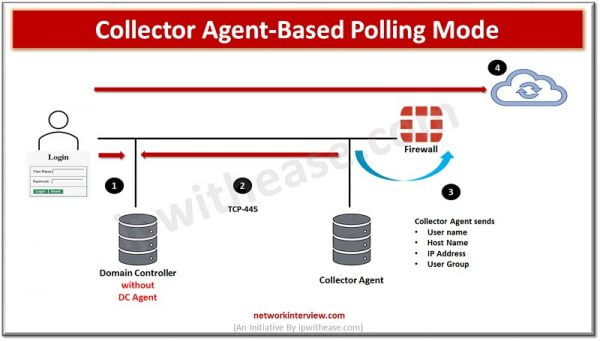
- User authenticates with DC
- Collector Agents polls DC to get the login events data
- Collector Agent forwards login data to FortiGate Firewall
- User doesn’t require to authenticate
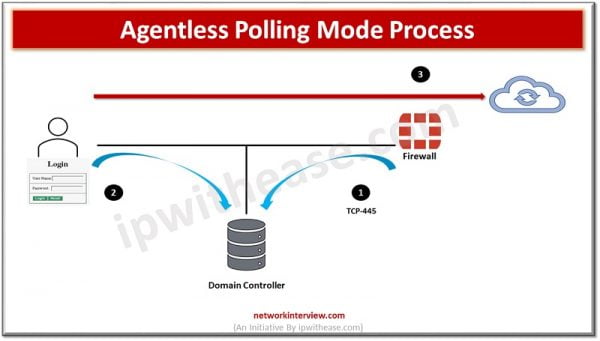
Agentless Polling Mode Process
Another Method for polling is Agentless and is called as Agentless Polling Mode Process
- FortiGate frequently polls Domain Controller to get user event logs
- User authenticates with the Domain Controller
- FortiGate discovers polling login event in next poll
- User doesn’t need to authenticate as FotiGate already aware whose traffic it is receiving
FSSO Configuration and Installation
Step -1 FSSO Agent Installation
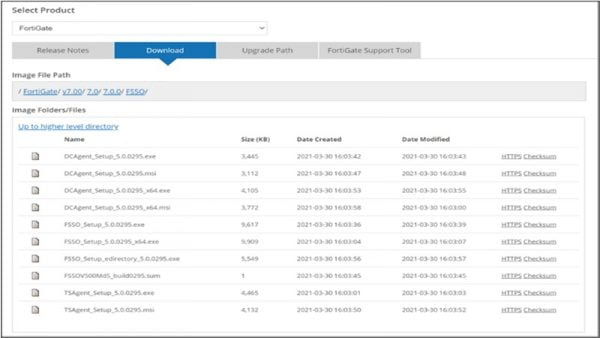
Download FSSO Agent on Window AD Server
1. Visit FortiGate support website https://support.fortinet.com
2. Download🡪 Firmware Images
3. Select FortiGate and the click Download
4. Click v7.00 > 7.0 > 7.0.0 > FSSO
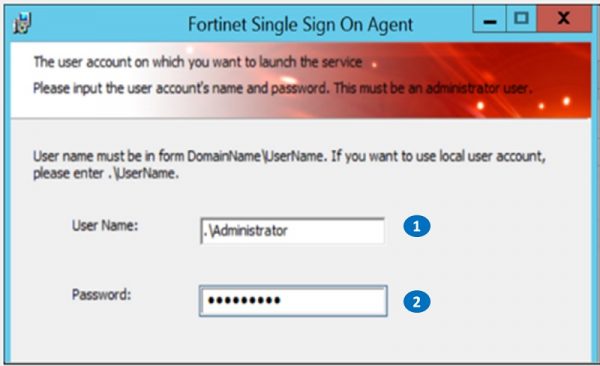
Install the Collector Agent on PC as Administrator
1. Set Username for FSSO Domain Admin
2. Set Password for Domain Admin
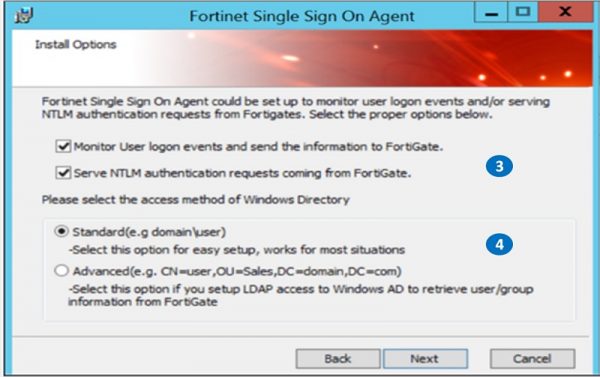
3. Monitor user login sessions
4. Set Standard features
Step- 2 After installing FSSO Agent , move ahead for DC Agent Installation Process
Please follow step 1 to step 5
1. Set Collector Agent IP address and Set Installation listening port
2. Select domain which will be monitored
3. Exempt any user which you don’t want to monitor or comes under exceptional list
4. Select domain controllers
5. Set working mode as DC Agent Mode
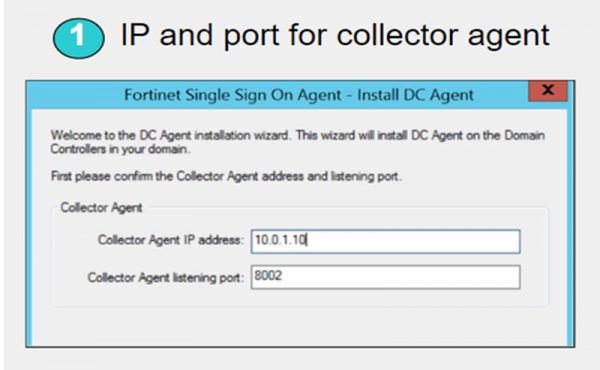
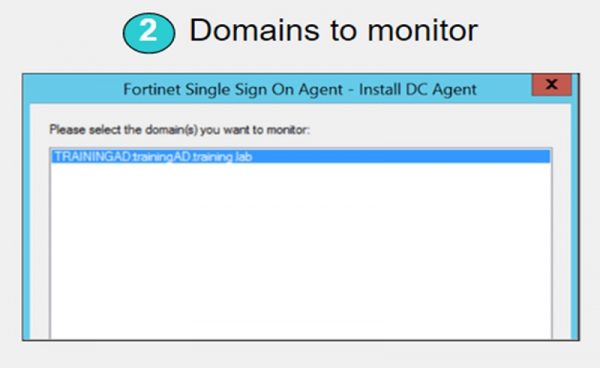
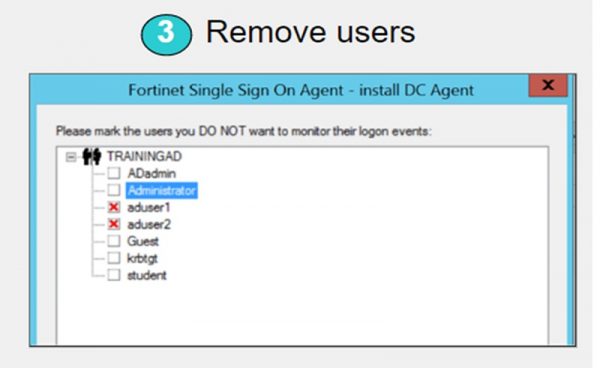
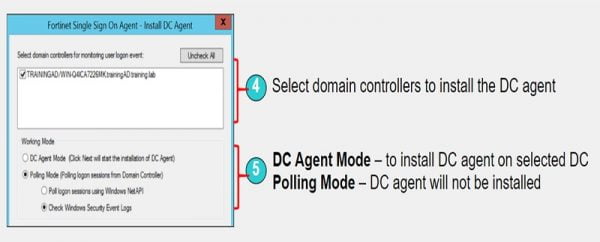
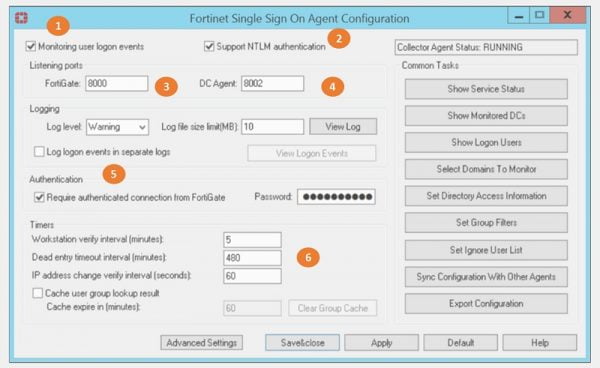
FSSO Collector Client Configuration
1. Enable 🡪 Monitor user login events
2. Enable/Disable NTLM authentication
3. Listening port for FortiGate firewall – 8000
4. Listening port for DC Agent – 8002
5. Enable authentication between FortiGate and Collector Agent and provide password for authentication validation
6. Set timer for polling
Group Filter
FSSO collector Agent manages FortiGate Group filters. Group filters can decide which information of a user should be sent to FortiGate. Group Filters are associated with FortiGate Serial numbers. FortiGate has capability to support 256 Windows AD user groups.
1. Set Group Filter
2. FortiGate Filter List TAB will open
3. Select ADD
4. Create NEW Group filter and associate the Serial number of FortiGate device to it.
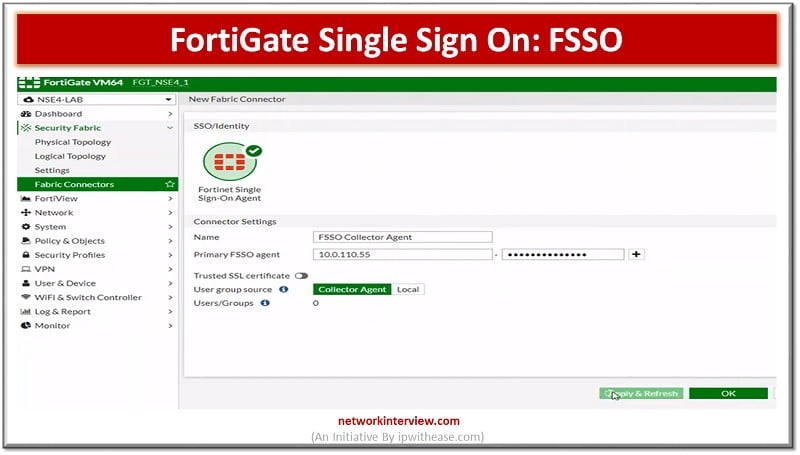
Configure FSSO in FortiGate Firewall
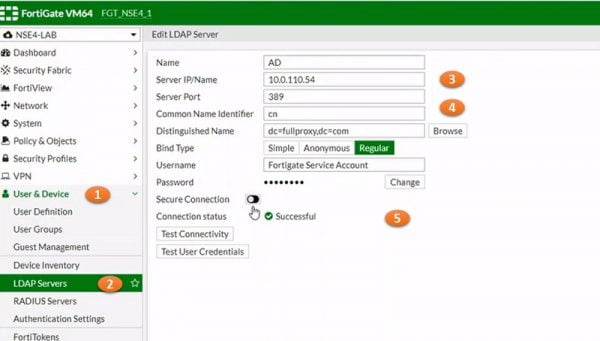
1. Configure LDAP ,
2. User & Device 🡪 LDAP Servers and Select Create NEW
3. Set AD server name and IP address
4.Set Common Name CN Identifier and its values
5. Provide Security Password and enable connection Successful
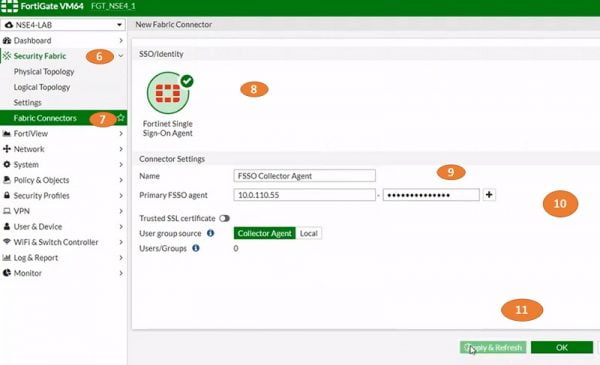
6. Go to Security Fabric
7. Select Fabric Connectors
8. Select SSO/Identity, select Fortinet Single Sign-On Agent.
9. Put Name for connector Setting
10.Add Primary FSSO Agent IP address and Password
11.Apply and Refresh configuration
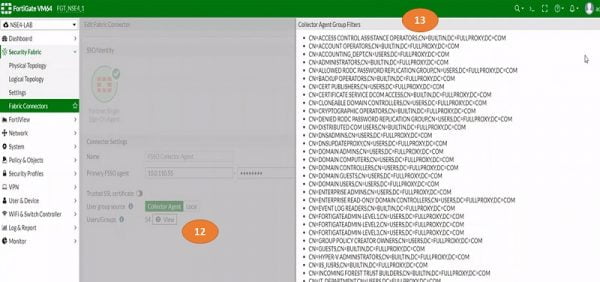
12.Select View tab to add FSSO Group Filters
13.Add Group filter to the FSSO and Click OK
14.Again go to Users & Device 🡪 Users Group
15.Add new User Group, Name it and select Type of FSSO
16.Also Add FSSO in user members
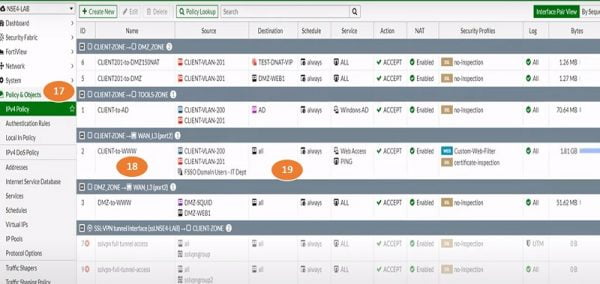
17.Create Policy for User Group, Go to Policy & Objectsand select IPV4 Policy
18.Name Security policy
19.Add Source Zone , source IP address which is FSSO Users-members
20.Select destination Web-Browser, fill other details
21.Select OK
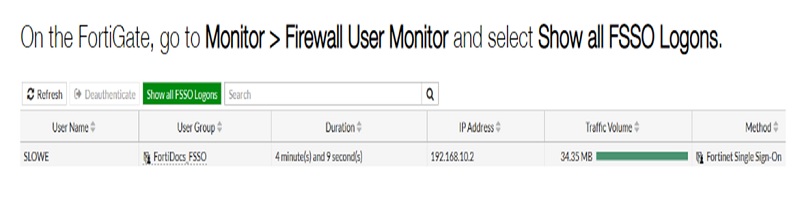
Monitor Connectivity and Login Details of Users
Continue Reading:
Fortinet FortiGate HA (High Availability)
IPSec VPN Configuration: Fortigate Firewall



