Endpoint Detection and Response (EDR) vs. Network Detection and Response (NDR): Which is Right for Your Organization?
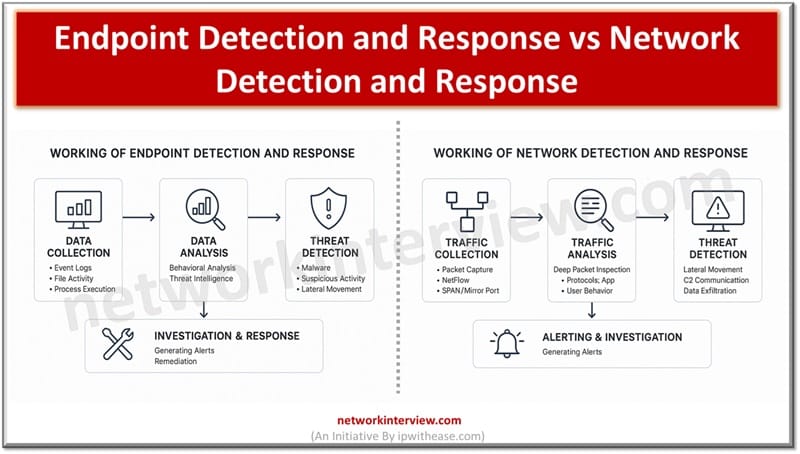
Endpoint Detection and Response focuses on monitoring and responding to threats on individual devices like laptops and servers. Whereas, Network Detection and Response monitors network traffic to detect and respond to threats across the entire network infrastructure.
Constant threats and vulnerabilities are permanent companions in the IT landscape. Various security solutions have emerged to protect perimeter, digital assets. As the cyber threat landscape is very vast and complex and requires specialized tools and technologies to effectively handle cyber threats and which are constantly evolving to reduce the threat landscape.
In today’s article we understand the difference between endpoint detection and response (EDR) and Network detection and response (NDR) tools and technologies, their key features, key differences and use cases.
What is Endpoint Detection and Response (EDR)
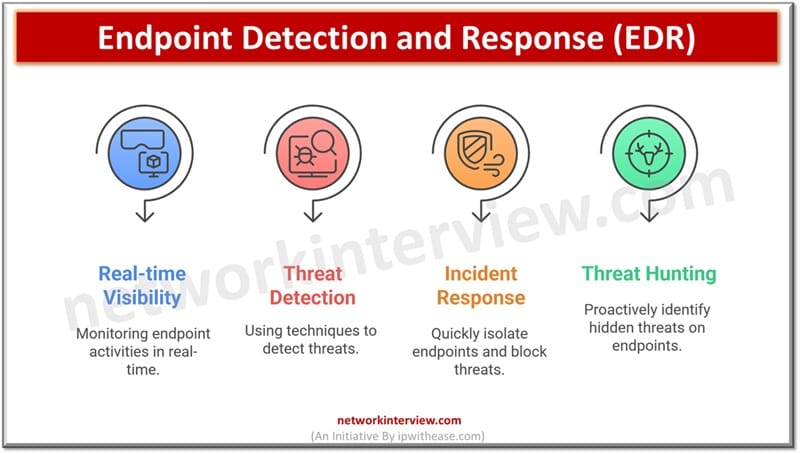
Endpoint detection and response tools focus on endpoints as the name suggests. They work on endpoints such as workstations, servers, mobiles, laptops and other mobile assets. They provide real time monitoring, detection and blocking of threats with advanced threat detection capabilities. It can identify malware and other malicious activities on devices and provide rapid incident response. EDR solutions provide threat hunting, malicious activity discovery and its containment to prevent incidents and reduce the attack surface.
Features of EDR
- Real time visibility into activities happening on endpoints
- Wide range of threat detection techniques being used such as anomaly detection, heuristics and scans based on threat signatures
- Rapid incident response to isolate suspected endpoints , malicious content blocking and threat remediation with minimal or no impact on operations
- Proactive threat hunting is supported to identify hidden threats and potential vulnerabilities on endpoints
What is Network Detection and Response (NDR)
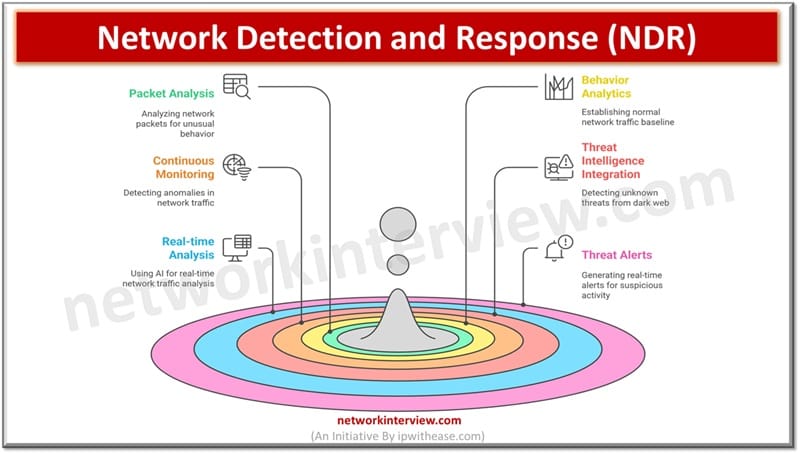
Network detection and response or NDR as the name suggests focus is network perimeter / network traffic. Continuous monitoring of network traffic is performed to create a baseline for normal network behaviour patterns. When any pattern outside the baseline is detected then potential threat presence is recorded and notified. NDR tools collect and analyze network data using machine learning techniques to detect potential threats. It detects unusual traffic based on baseline derived by network analysts which might get missed out due to unknown or new signatures.
Features of NDR
- Capturing network packets and analyzing them for their content for unusual behaviour detection, threat identification with deep packet inspections
- Behaviour analytics to establish normal network traffic baseline
- Continuous monitoring of network traffic for anomaly detection such as unusual high data transfers, multiple login attempts and suspected breach indicated with data flows
- It is integrated with threat intelligence feeds to detect unknown threats from dark web
- Network traffic analysis in real time using machine learning and AI algorithms
- On detection of suspicious activity real time threat alerts are generated
Comparison: EDR vs NDR
Below table summarizes the differences between the two:
Features | EDR(Endpoint Detection and Response) | NDR(Network Detection and Response) |
| Scope | Primarily meant for endpoints such as workstations, laptops. Mobile devices etc. | Primarily meant for networks |
| Function | Threat detection and response for endpoints | Monitoring of network traffic for detecting threats and anomalies |
| Features | • Data collection at endpoints continuously • Threat detection and real time alerting • Behaviour analytics and remediation (auto) • Integration with threat databases enrich the identification of threat landscape which allows recognition of malware, suspicious IP addresses etc. | • Deep packet inspections • Anomaly detection and protocol decoding • Traffic analysis and alert on threats • ML and AI based insights help in identification of new threat actors |
| Use cases | • Ideal for organizations seeking granular security and incident response handling capabilities on endpoints • Meant for malware, ransomware and vulnerabilities detection | • Visibility, threat detection and response capabilities for organizations focusing on network security • Meant for protection from insider threat, and lateral movement |
| Benefits | • Focused approach towards endpoint security • Threat detection and auto remediation | • Focused approach towards network security • Real time response and threat detection |
| Response mechanism | Isolation of compromised endpoints | Malicious network activity blocking |
| Data sources | Agents deployed on endpoints have activity logs | Network sensors deployed to analyze network traffic |
| Identity and access management | Identity integration at basic level supported | No direct involvement |
Download the comparison table: Endpoint Detection and Response vs Network Detection and Response
Tag:comparison, Security



