What is a DNS Rebinding Attack?
A DNS rebinding attack tricks a browser into bypassing same-origin policy, thereby allowing attackers to access internal networks or devices through malicious DNS responses.
In networking systems are addressed with a unique numerical value which is known as IP address. IP address is used to locate a system in the networks and basis of communication between systems. However, IP address alone is not enough as it is difficult to remember, each IP address has an associated host name. DNS or domain name systems map this host name to its corresponding IP address. DNS server or service is prone to a variety of cyber attacks DNS rebinding is one such mechanism.
In today’s topic we will learn about DNS rebinding attack, how rebinding attacks works, Mitigation and preventive measures against DNS rebinding attacks.
DNS Rebinding Attack
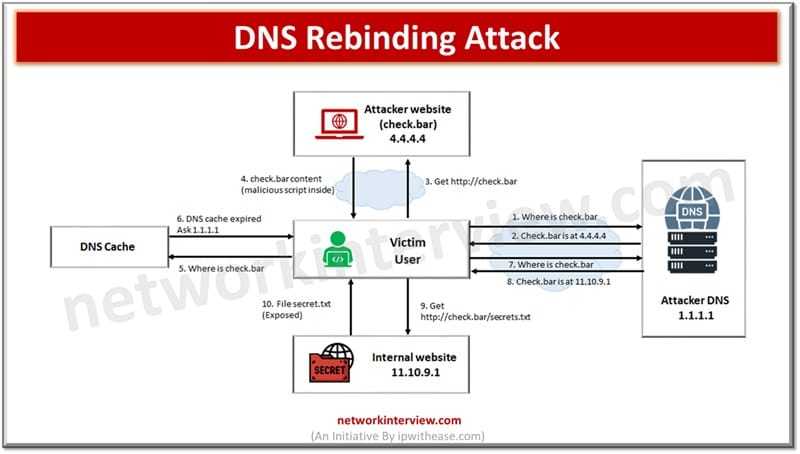
DNS rebinding attack leverages the fact that when an exploit such as cross site scripting – XSS happens to compromise the domain the domain name server is also hijacked. In DNS binding attacks the DNS requests go to a specially crafted website by sending requests to name servers of compromised domains rather than the requesting address of a legitimate website. All traffic sent to different IP addresses is relayed back to the web server even if it is not a malicious URL or anything else used commonly during phishing scams and other kinds of attacks which occur online.
When a DNS rebinding attack happens then there is no control over the nameserver and all requests to resolve hostname are redirected to an alternate nameserver which is under attacker control. Sometimes end users are tricked into creating phishing websites using these websites and all traffic that is redirected to the hijacked URL is sent back to the original server, which forces users to install phishing pages as a result.
DNS rebinding attacks let attackers access sensitive information such as credentials and confidential emails.
How DNS Rebinding Attack works
The DNS rebinding attack happens to bypass security controls and policies which restrict someone from accessing a network device to which they have no authorization to access over a network.
- The attacker creates an A record in DNS for his hostname to point to his internet facing web server. The TTL (time to live) record is set for a very limited time such as a few seconds.
- The user visits malicious host name
- The attacker changes DNS A record of that hostname to point to its target IP address
- The JavaScript component in a malicious website tries to connect to a malicious hostname but since TTL is set with low value, the user system will again make a DNS request to the malicious hostname. This time the IP address is resolved as set by the attacker in step 2.
The attacker can also create a CNAME record to an internal hostname to rebind their hostname to the internal hostname. DNS rebinding can be used to circumvent the same original policy. Internal websites are more prone to such attacks due to hosting sensitive information. Internal websites usually do not use HTTPS and there won’t be SSL mismatch errors which could hamper the attack.
DNS rebinding can be used to target web servers or any other network devices.
Mitigation & Prevention of DNS Rebinding Attacks
DNS pinning is one common technique to prevent these attacks. This makes the browser ignore TTL or DNS records and set itself TTL. This however can be bypassed as well if the attacker implements a firewall in front of the web server.
Another way to protect web servers from rebinding attacks is configuring the webserver to check HTTP host header in the incoming request. If the host header does not match, the request will be dropped. The firewall can be configured to prevent external host names for resolution of internal IP addresses.
Tag:Security



