DLL Hijacking in 8 Steps
There are various types of Cyber Attacks on rise. As physical boundaries are diminishing rapidly and majority of enterprises rely on Internet and other emerging technologies such as cloud computing, GenAI etc. to run their businesses bad vectors are taking the advantage of these emerging technologies to launch more sophisticated cyber-attacks. Vulnerabilities and deficiencies systems are often exploited by hackers to gain advantage.
In today’s topic we will learn about DLL (Dynamic link library) DLL hijacking cyber-attacks, we will understand about DLL files, how DLL hijacking works and how we can identify and prevent DLL hijacking attack?
About DLL files
DLL file is a dynamic link library having reusable code and data which multiple programs can use at the same time to perform different functions to improve efficiency and bring in modularity in software programming. They are more like a set of resources which can be used by software applications. When software requires some specific functionality, it can search in the DLL. It is a Microsoft concept of shared library in Windows operating system.
DLLs are created by programmers by writing custom code to perform a specific function such as draw image, compute, connect to Internet etc. DLLs can be written in any programming language such as C++, C# and then compiled into a special file having both code and data.
How DLL hijacking works
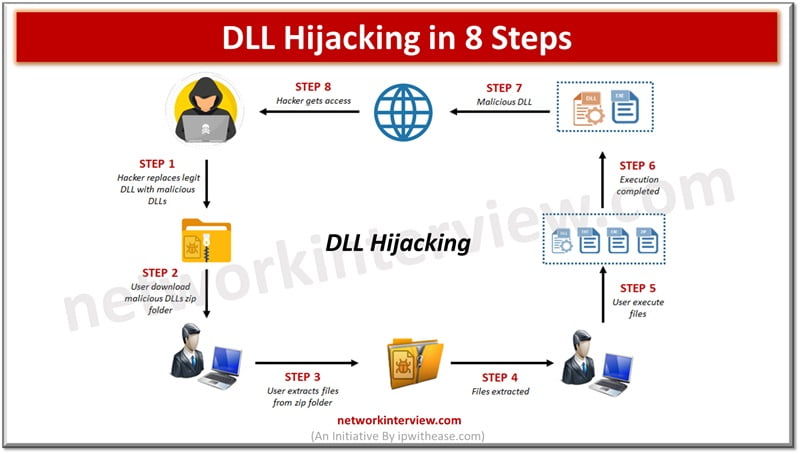
DLL hijacking works when hackers replace legit dynamic link libraries (DLL) files with their own files having malicious contents.
A hacker can mislead software to load harmful code instead of legit DLL by insertion of malicious DLLs at the spot where the program looks for DLLs. The attacker can perform escalation of privileges and gain access to the system. At times missing DLLs provide a great opportunity to hackers to insert their own malicious DLLs.
Types of DLL Attacks
DLL attacks can be of several types as under:
- DLL search order attack looks for a definite pattern for DLL in Windows operating system
- DLL side loading attack targets WinSxS directory
- Phantom DLL hijacking attack uses old DLL to gain access to system. DLL names used in search to execute new harmful and malicious code on systems
DLL hijacking involves dynamic link libraries with injecting malicious code into the software application.
- The user unknowingly loads malicious file in system while application loads
- The malicious file in dynamic link library (DLL) places attack within application boundary
- Users are unaware of launching malicious file while loading the application
- Malicious and infected file is directly injected into the system
- Cyber hacker gets unauthorised access to system and perform undesirable activities such as stealing, destroying, deleting user / organization information
Related: Spear Phishing vs Whaling: Cyber Attacks
Techniques to Prevent DLL Hijacking
DLL hijacking can be prevented by a variety of preventive measures such as:
- Use of third-party advanced tools – special advanced tools are available which are designed to prevent cyber attacks where attackers can inject malicious content into the system via DLLs.
- Keep your antivirus updated – maintain your anti-virus software and update it with latest virus signatures at regular intervals
- Regular scan of system vulnerabilities – A well-established process of systems scan for vulnerabilities help to prevent them in timely manner
- Enable MFA – MFA or multi factor authentication is a powerful technique and help in reduction of DLL cyber attacks
- Phishing mails handling – phishing mails need to be handled carefully as they can contribute to DLL attacks. Users must be careful not to open mails or click on links coming from unknown / suspicious sources.
- Maintaining system patches – Regular Updation of system, application and security patches help fix vulnerabilities
- Whitelisting applications – whitelisting technique helps in lowering the threat of malicious DLLs being gaining system access
Tag:Security



