What is difference between Encryption and Hashing?
In the realm of data security, hashing and encryption are commonly employed to protect information from unauthorized access. While both methods have distinct processes and advantages, they are occasionally mistakenly used interchangeably. This blog will delve into the definitions of Encryption and Hashing, as well as highlight the key differences between the two.
What is Encryption?
Encryption is the process of converting plaintext (readable and understandable data) into ciphertext (encoded and unreadable data) using an encryption algorithm and a key. The purpose of encryption is to protect the confidentiality and integrity of data, ensuring that only authorized parties can access and understand the information.
Types of Encryption
- Symmetric Encryption: Also known as secret key encryption, symmetric encryption uses the same key for both encryption and decryption. The sender and the recipient must share this secret key in advance. Symmetric encryption is fast and efficient but requires a secure method of key exchange.
- Asymmetric Encryption: Also known as public key encryption, asymmetric encryption uses a pair of mathematically related keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, allowing anyone to encrypt data, while only the holder of the private key can decrypt it. Asymmetric encryption enables secure communication without the need for a shared secret key.
Applications of Encryption
- Secure communication: Encryption ensures that sensitive information sent over networks, such as financial transactions or personal messages, remains confidential and secure from eavesdroppers.
- Data protection: Encryption is used to safeguard stored data, such as files on a hard drive or data in a database, making it unreadable to unauthorized individuals who gain access to the storage medium.
- Authentication and Integrity: Encryption techniques like digital signatures use cryptographic algorithms to verify the authenticity and integrity of digital documents or messages, providing assurance that the data has not been tampered with.
Limitations of Encryption
- It does not guarantee protection against all forms of attacks.
- Key management
- Encryption strength
- Implementation flaws
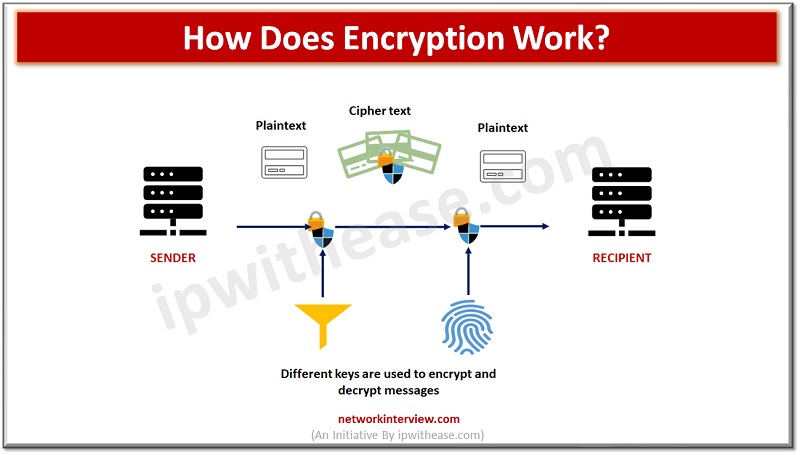
How Does Encryption Work
Encryption works by transforming plaintext (original data) into ciphertext (encrypted data) using an encryption algorithm and a key. The encryption process involves the following steps:
- PlainText: The original data that you want to protect, such as a message, a file, or any other form of digital information.
- Encryption Algorithm: An encryption algorithm is a set of mathematical operations or rules that transform the plaintext into ciphertext.
- Key Generation: A key is a parameter used by the encryption algorithm to control the encryption process. The key can be a sequence of bits, numbers, or characters. The length and complexity of the key can vary depending on the encryption algorithm and the desired level of security.
- Encryption Process: The encryption algorithm takes the plaintext and the encryption key as input. It performs a series of operations, such as substitution, permutation, bit shifting, or mathematical calculations, on the plaintext to produce the ciphertext. The specific operations depend on the encryption algorithm used.
- Ciphertext: The output of the encryption process is the ciphertext. It is the encrypted form of the original data and appears as a scrambled and unintelligible sequence of characters or bits.
- Secure Transmission or Storage: The ciphertext can be transmitted over a network or stored in a secure manner, as it is designed to be secure against unauthorized access. Even if an attacker intercepts the ciphertext, it should be computationally infeasible to derive the original plaintext without the correct key.
To decrypt the ciphertext and retrieve the original plaintext, the reverse process is followed:
- Ciphertext: The encrypted data (ciphertext) is received or accessed.
- Decryption Algorithm: The decryption algorithm is the inverse of the encryption algorithm. It takes the ciphertext and the decryption key as input and performs operations to reverse the encryption process.
- Decryption Process: The decryption algorithm applies the appropriate inverse operations to the ciphertext using the decryption key. This process reconstructs the original plaintext.
- Plaintext Recovery: After completing the decryption process, the original plaintext is recovered and becomes readable and understandable.
Few Encryption Algorithms
- Advanced Encryption Standard (AES): AES is a symmetric encryption algorithm adopted as the standard by the U.S. government. It supports key sizes of 128, 192, or 256 bits and operates on fixed-size blocks of data. AES is widely used for secure data encryption in various applications.
- RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm named after its inventors. It uses a pair of mathematically related keys: a public key for encryption and a private key for decryption. RSA is widely used for secure communication, digital signatures, and key exchange protocols.
- Triple Data Encryption Standard (3DES): 3DES is a symmetric encryption algorithm derived from the original Data Encryption Standard (DES). It applies the DES algorithm three times with different keys to increase security. 3DES is still used in some legacy systems and applications.
- Blowfish: Blowfish is a symmetric block cipher designed to be highly secure and efficient. It supports variable key sizes and operates on 64-bit blocks. Blowfish is often used in applications requiring secure and fast encryption, such as virtual private networks (VPNs) and secure file transfer.
- Twofish: Twofish is another symmetric block cipher designed as an alternative to AES. It supports key sizes up to 256 bits and operates on variable block sizes. Twofish is known for its strong security and has been extensively analyzed.
- ChaCha20: ChaCha20 is a symmetric stream cipher designed to be secure and efficient. It is often used in applications requiring fast encryption and is the default encryption algorithm for popular protocols like TLS 1.3. ChaCha20 is considered resistant to various cryptographic attacks.
- Elliptic Curve Cryptography (ECC): ECC is a family of asymmetric encryption algorithms based on elliptic curves over finite fields. ECC offers strong security with shorter key sizes compared to other asymmetric algorithms like RSA. It is widely used in secure communication protocols and systems with resource-constrained environments.
What is Hashing?
Hashing is a process used in computer science and cryptography to convert data of any size into a fixed-size value, typically a sequence of alphanumeric characters known as a hash code or hash value. The hash function takes the input data and applies a mathematical algorithm to generate the hash value.
Characteristics of Hashing
- Deterministic: The same input will always produce the same hash value. Even a small change in the input will result in a significantly different hash value.
- Fixed-size output: Regardless of the size of the input, the hash function will generate a hash value of fixed length. For example, the SHA-256 algorithm generates a 256-bit hash value.
- One-way function: It is computationally infeasible to derive the original input from the hash value. In other words, given a hash value, it is extremely difficult to determine the input that generated it.
- Avalanche effect: A small change in the input should produce a completely different hash value. This property ensures that even a slight modification in the input will lead to a significantly different hash value.
- Efficiency: Hash functions are designed to compute hash values quickly. Even for large inputs, the computation time remains relatively constant.
Applications of Hashing
- Data integrity: Hashing is commonly used to verify the integrity of data. By comparing the hash value of received data with the expected hash value, one can determine if the data has been modified or tampered with.
- Password storage: Instead of storing passwords in plain text, they are often hashed and stored. When a user enters their password, the system hashes the input and compares it to the stored hash value to authenticate the user.
- Data indexing: Hashing is used in data structures like hash tables to efficiently store and retrieve data. Hash functions distribute data across a fixed number of buckets, enabling fast lookup and retrieval of information.
- Digital signatures: Hash functions play a crucial role in digital signature algorithms. They are used to create a hash value of a message, which is then encrypted with the private key of the sender. The recipient can verify the signature by decrypting it with the sender’s public key and comparing the decrypted hash value with the hash of the received message.
Limitations of Hashing
- Hash collisions can occur when two different inputs produce the same hash value, although modern hash functions aim to minimize the likelihood of collisions.
- It is susceptible to brute-force attacks, where an attacker can systematically try different inputs to find a matching hash value.
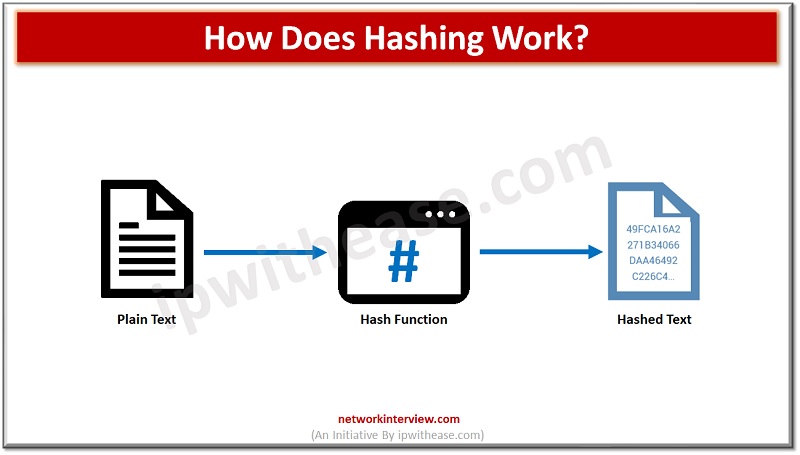
How Does Hashing Work?
Hashing works by taking an input, often referred to as the “message,” and applying a hash function to produce a fixed-size hash value. The hash function performs a series of mathematical operations on the input data, transforming it into the desired output.
Here’s a simplified explanation of how hashing works:
- Input data: You start with the data you want to hash, which can be any form of data, such as a text string, a file, or a binary sequence.
- Hash function: A hash function is a mathematical algorithm that takes the input data and processes it to produce a hash value. The algorithm applies various operations, such as bitwise operations, modular arithmetic, and logical functions, to transform the input data into a fixed-size output.
- Fixed-size hash value: The hash function generates a hash value of a predetermined length, regardless of the input size. Common hash functions, like MD5, SHA-1, and SHA-256, produce hash values of specific lengths, such as 128 bits, 160 bits, or 256 bits.
- Unique representation: The hash value serves as a unique representation of the input data. Even a small change in the input will result in a significantly different hash value due to the avalanche effect of the hash function.
- Deterministic nature: The same input will always produce the same hash value when processed by the same hash function. This property allows for verification and comparison of data using their hash values.
Hashing Algorithm Example
To illustrate, let’s take a simple example using the SHA-256 hash function:
Input: “Hello, world!”
- The SHA-256 hash function takes the input string “Hello, world!”.
- The hash function processes the input through a series of operations, manipulating the data at the binary level.
- After the calculations, the hash function produces a fixed-size hash value of 256 bits (32 bytes) in the case of SHA-256.
- The resulting hash value, for example, could be: “2ef7bde608ce5404e97d5f042f95f89f1c232871512d5944a5163c2fca1b0e3e”.
- If the input were to change even slightly, such as to “Hello, World!” (note the capital ‘W’), the resulting hash value would be completely different.
The generated hash value can then be used for various purposes, such as data integrity checks, password storage, or indexing, as mentioned in the previous response.
Difference between Encryption and Hashing
Hashing and encryption are both cryptographic techniques but serve different purposes and exhibit distinct characteristics. Here are the key differences between hashing and encryption:
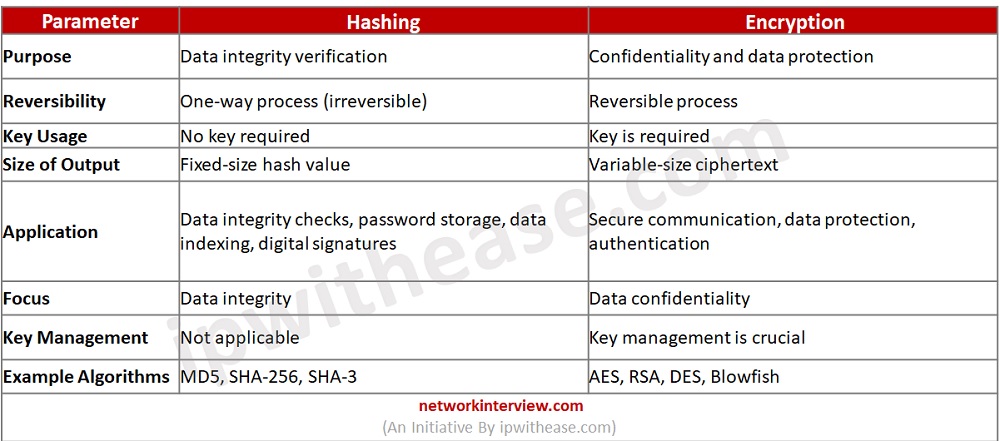
Purpose:
- Hashing: The primary purpose of hashing is to produce a fixed-size hash value or digest that represents the input data. It is used for data integrity checks, data indexing, password storage, and digital signatures. Hashing is typically a one-way process, and the original input cannot be derived from the hash value.
- Encryption: Encryption is used to protect the confidentiality and integrity of data. It transforms plaintext into ciphertext using an encryption algorithm and a key. The encrypted data can be decrypted back into its original form using the correct key.
Reversibility:
- Hashing: Hashing is a one-way process, meaning that it is computationally infeasible to derive the original input from the hash value. Hash functions are designed to be irreversible, making them suitable for tasks where the focus is on data verification rather than retrieval.
- Encryption: Encryption is a reversible process. The ciphertext can be decrypted back into plaintext using the correct decryption algorithm and key.
Key Usage:
- Hashing: Hashing does not require a key. The same input will always produce the same hash value regardless of any key. Hash functions operate solely on the input data.
- Encryption: Encryption relies on a key, which is an essential component of the encryption process. The key influences the encryption algorithm, and the same input will produce different ciphertexts with different keys. The correct key is needed for successful decryption.
Size of Output:
- Hashing: Hash functions generate a fixed-size hash value of a predetermined length, typically a few dozen to a few hundred bits. The size of the output remains constant regardless of the input size.
- Encryption: Encryption can produce ciphertext of varying sizes depending on the length of the plaintext and the encryption algorithm used. The size of the ciphertext may not be fixed and can be larger than the original plaintext.
Application:
- Hashing: Hashing is commonly used for tasks such as data integrity verification, password storage, data indexing, and digital signatures.
- Encryption: Encryption is widely used for secure communication, data protection, secure storage, and authentication. It ensures that sensitive information remains confidential and secure.
Security Focus:
- Hashing: The primary focus of hashing is data integrity. Hash functions are designed to detect any changes or tampering in the input data. They aim to produce unique hash values for different inputs and minimize the likelihood of hash collisions.
- Encryption: The primary focus of encryption is data confidentiality. Encryption algorithms scramble the data, making it unreadable to unauthorized individuals. The security of encryption relies on the strength of the algorithm and the secrecy and management of the encryption keys.
While hashing and encryption have different purposes, they can be used together in some scenarios. For example, a common practice is to hash passwords for storage and verification, while using encryption to secure the transmission of those passwords.
Below table summarizes the differences between the two types of cryptographic techniques:
Download the comparison table: Encryption vs Hashing
Continue Reading:
WEP vs TKIP vs CCMP: Understanding what each encryption technique offers
Static Hashing vs Dynamic Hashing
Tag:comparison, Security