Checkpoint SD WAN: Concept, Architecture & Configuration
Note: This document is for those seekers who have prior knowledge of SD WAN and want to enhance SD WAN concept in Checkpoint perspective.
This blog covers below topics of Checkpoint SD WAN:
- Quantum CheckpointSD-WAN concept
- Architecture
- Application basic traffic steering
- Demo-> how to configure Checkpoint SD WAN
- Monitoring Checkpoint SD WAN logs
Checkpoint SD WAN Concept
Main purpose of SD-WAN is the cost saving.
Checkpoint always focus on Threat Prevention policy and here we are using Checkpoint R80.10. Components we use during the configuration of SD-WAN and firewall policy are:
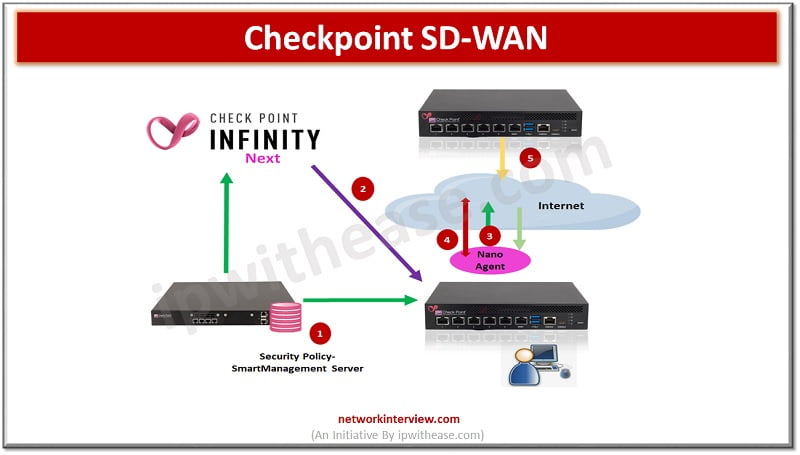
- SmartManagement Server: which installs security policy and shares objects with infinity next portal (Infinity Next Portal will discuss later)
- Infinity Next: it holds the SD-WAN traffic steering policy and object synchronisations. Traffic steering for applications provides feature of Jitter, Packet Loss, Latency and link failovers. Active probing is also the part of traffic steering which helps to monitor the multiple ISP links.
- Nano Agent: it holds the steering policy from the Infinity Next
- Active Probing: measuring the link quality
Checkpoint SD WAN Architecture
Here we will discuss the Architecture of the Checkpoint SD WAN topology.
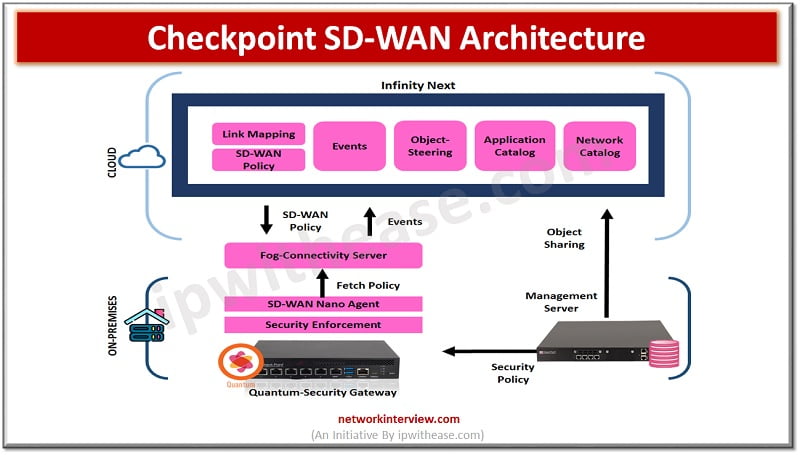
- Security Management Server -> installing the policy on the gateways and it also synchronizes its network objects with infinity next portal which is under Infinity Next Portal
- Link Mapping -> where we define which interface goes to which link
- Nano Agent -> which fetches policy from Infinity Next portal. It helps us to perform smooth deployment.
- Infinity Next ->Helps to sync the objects with Management Server
WAN Links and Steering Policy
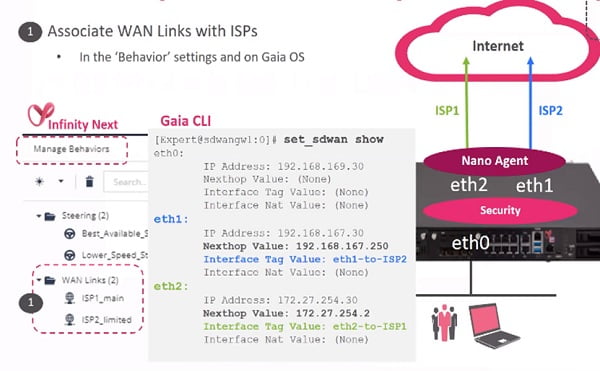
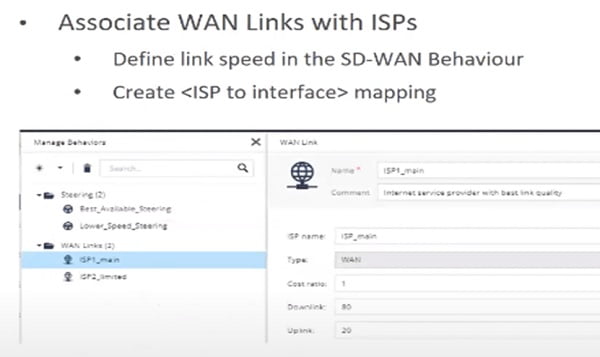
- Wan links are associated with ISPs. Configure WAN links with name and IP addresses
- Define steering policy which allows you to differentiate the link.
- Define Steering policy which is based on the Jitter latency and packet loss
When we completed the association, we know that which link is associated with which steering policy and Ethernet
Routing
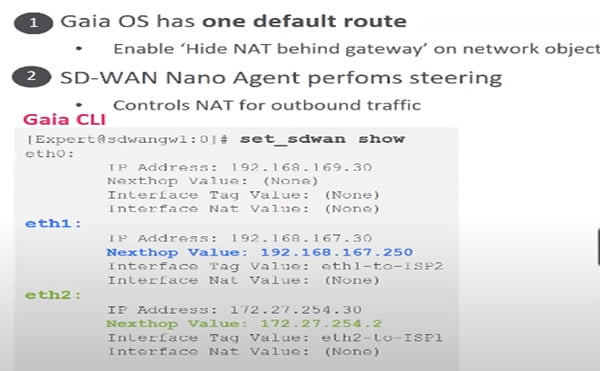
In Gaia you will define one default route for all which will be further managed by Nano Agent.
NAT
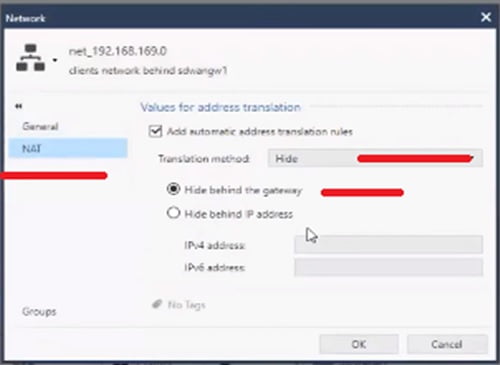
Also enable Hide NAT behind the Gateway.
Nano Agent fetches the policy from infinity portal
Run command
#fw sdwan stat
# cpsdwan stat
Understand the Link Monitoring in SD WAN
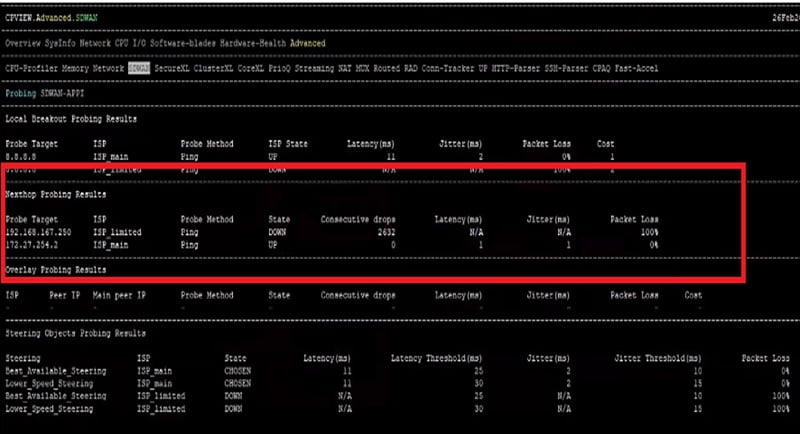
We can run the #cpview command to check the traffic pattern in the firewall.
We can see the Probe Targets which mention default IP 8.8.8.8 and also the next hop segment where ISP details and traffic are defined by firewall.
Final option is ISP selected means which ISP is carrying the traffic to the destination.
Next step is to define the Steering policy -> which application can use which link and for which behaviour and apply thresholds to the WAN links.
Note: before deploying the Steering and Security policy consider below points
- Choose best available WAN link according to the application
- and choose bandwidth according to the utilisation
- Limit bandwidth for low level applications
- Categorise the quality of WAN link
How to configure SD-WAN in Checkpoint?
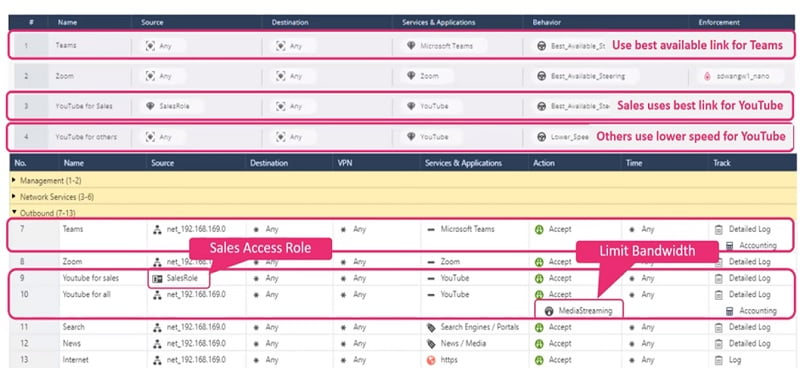
Scenario is
- Best Available link must assign for Teams application for high speed
- Sales Users can use high speed link for YouTube
- Other users can only use limited speed link for YouTube
Quantum SDWAN solution is managed by smart management server
where everything is related to the security and traffic steering is managed by the Infinity Next Portal
Allow policy for youtube and teams in the Security Gateway
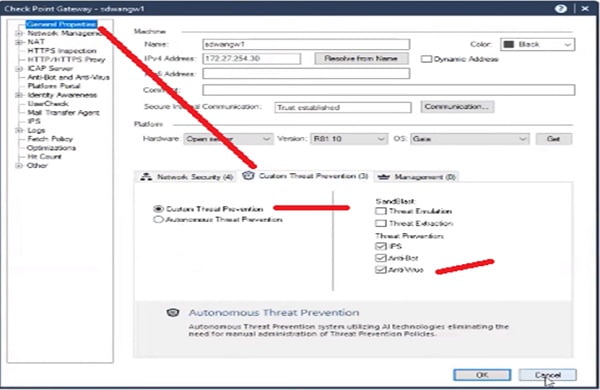
Step 1 Apply threat prevention policy in Security Manager Server
Step 2 Disable Hide NAT for every traffic
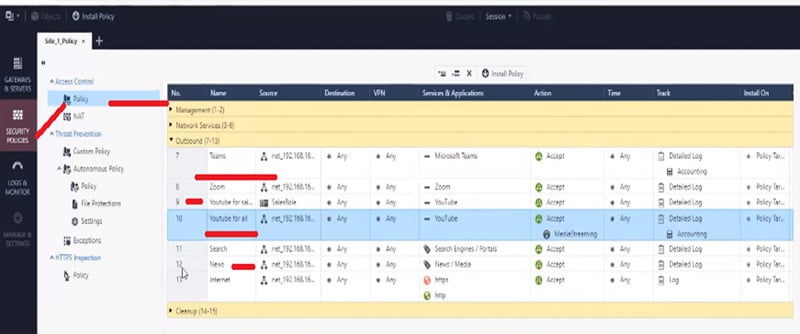
Step 3 Configure policy in the Firewall. Go to Security Policies -> Policy
- Teams : Access policy for Teams application Policy 7
- YouTube : Access policy for Sales user Policy 9
- YouTube for all : Access policy for all other user Policy 10
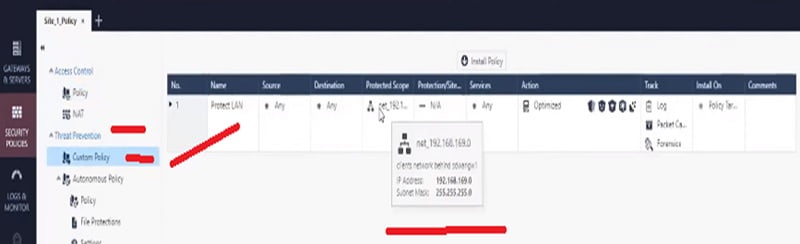
Step 4 Apply Basic default Threat Prevention Policy for subnet
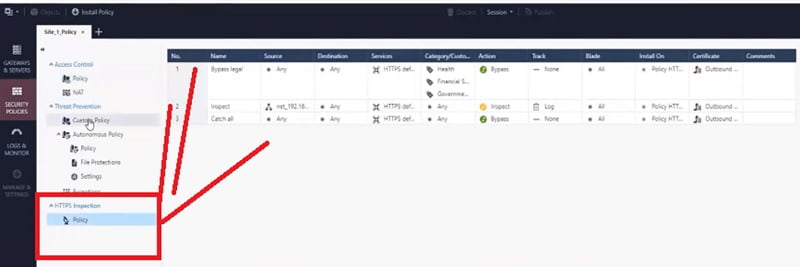
Step 5 Enable HTTPS Inspection for Youtube and Teams application in the Firewall
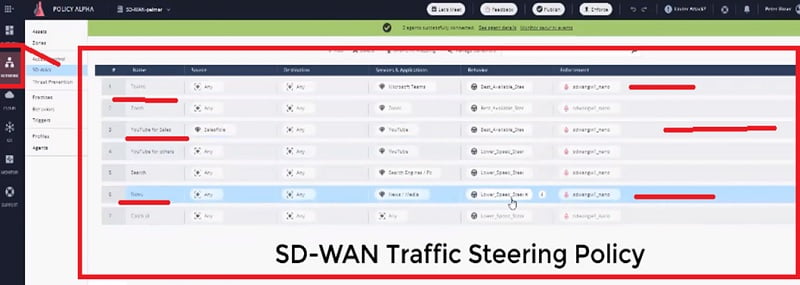
Step 6 Enable similar access in SD-WAN Steering Policy in Checkpoint Quantum.
Step 7 Wan Link mapping on the device. Next Hop is defined after enabling the Interface.
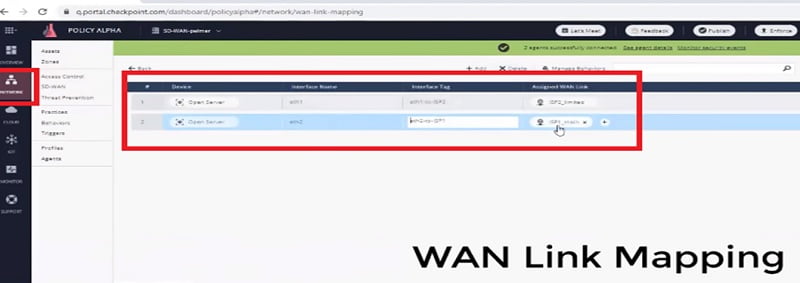
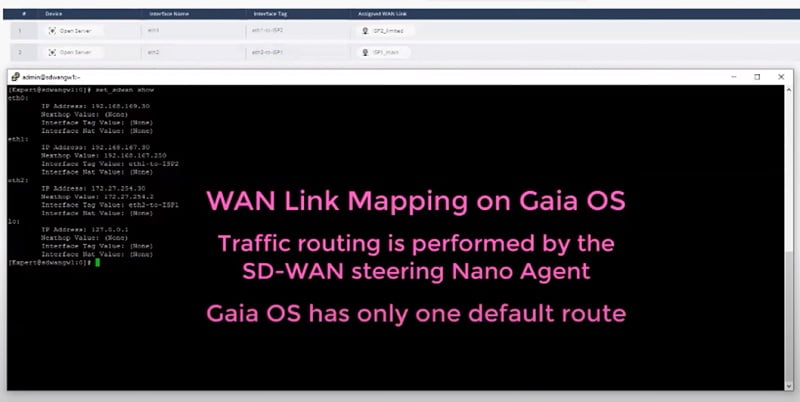
On the Security gateway we will map interface and WAN link mapping by using CLI command here, we manually define the interface WAN link mapping with active Steering Policy from CLI session.
We define Interface, Next-hop and keyword which enforces to make it active immediately.
Step 8 Check Network Address Translation (NAT) for whole subnet
Step 9 we can check the SD-WAN ISP, where interface are mapped with the characteristics. ISP has high speed bandwidth and ISP 2 has limited bandwidth.
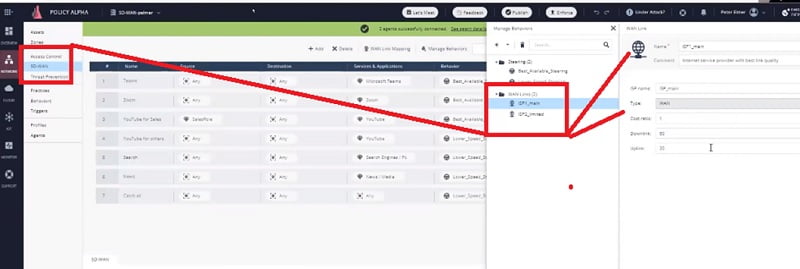
Step 10 Define the Steering objects. Steering objects are defined and the behaviours of Wide Area Network Interface will be used in the network. All the WAN criteria will be defined in the Steering Object. Please see bee screen-shot for better understanding.
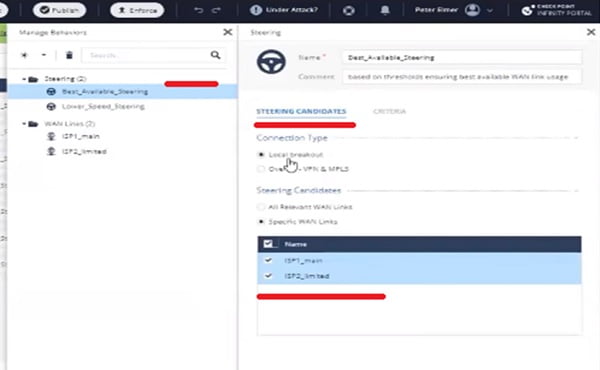
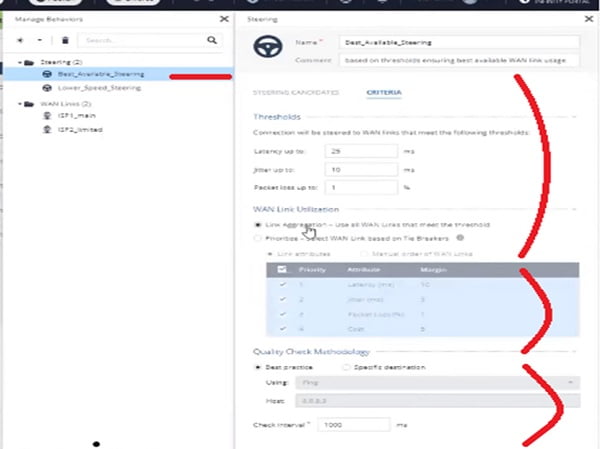
Step 11 Define Nano Agent as below
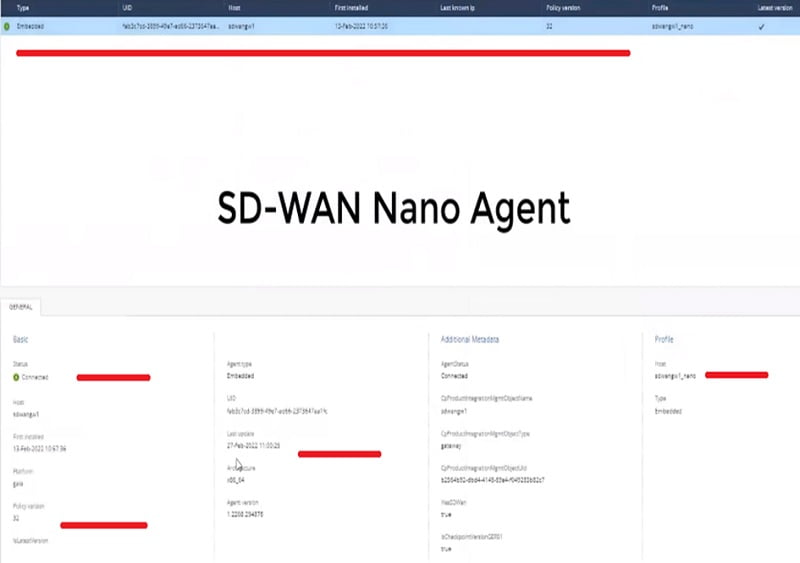
Step 12 here you can install Nano agent
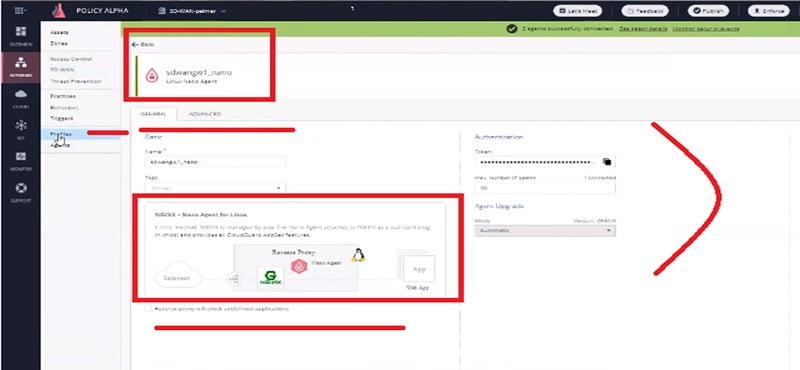
Now configuration is completed. Now we will access the application and check respective logs in the firewall.
Monitor SD-WAN Traffic Logs
Case 1 Access YouTube site as a normal user
- Check logs in Web Smart Console to see the logs
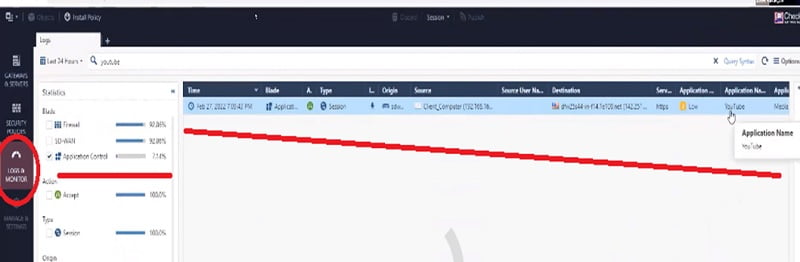
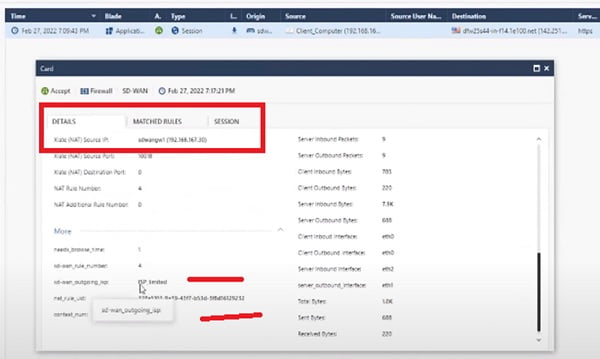
When we expand the log,
Case 2 Access YouTube site as a Sales User. We can see in below screen-shot that the traffic is going via Main ISP
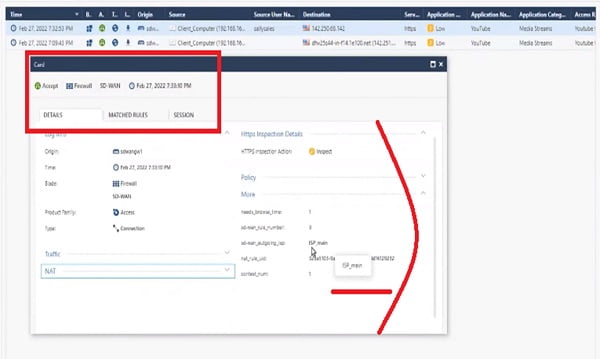
Everything works as per our configuration.
Continue Reading:
Understanding Checkpoint 3-Tier Architecture: Components & Deployment
Checkpoint NAT Policy: Types & Configuration
Tag:Checkpoint, Security



