Exploring the Role of Certificate Authorities (CA) in Cloud Security
In the rapidly evolving digital world, cloud security remains a pivotal concern for businesses and individuals. As we increasingly rely on cloud-based services for everything from data storage to application hosting, robust security measures become paramount. One key aspect of this security framework is the role played by Certificate Authorities (CAs) in the cloud environment. Understanding the integral function of CAs helps appreciate the complexities and necessities of cloud security.
The Fundamental Role of Certificate Authorities
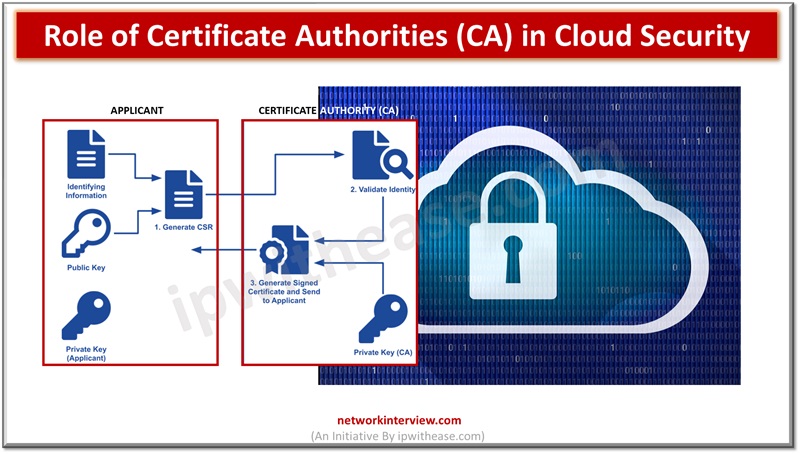
At its core, a Certificate Authority is an entity responsible for issuing digital certificates. These certificates serve as a digital passport or identification, ensuring that the entities or individuals involved in digital transactions are who they claim to be. CAs play a critical role in establishing a secure environment in cloud computing. They act as trusted third parties, verifying the identities of entities exchanging information and, thus, facilitating a secure communication channel. Exploring insightful resources can be incredibly enlightening for an in-depth understanding of these mechanisms.
Enhancing Trust in Cloud Environments
In a cloud setting, where data and services are often accessed over the internet, the assurance of identity and the integrity of transmitted information are essential. Certificate Authorities (CAs) play a vital role in this landscape. They contribute significantly by issuing SSL/TLS certificates, which are the backbone for online secure communication. These certificates encrypt data transferred between a user’s browser and the cloud service, forming a protective layer crucial in safeguarding sensitive information.
This encryption is not just a technical requirement; it’s a critical defense mechanism in preventing data breaches and interception by unauthorized parties. In an era where cyber threats are increasingly sophisticated, the role of SSL/TLS encryption in maintaining data confidentiality and integrity cannot be overstated. It acts as a first line of defense, ensuring that even if data is intercepted, it remains unintelligible and useless to the interceptor.
Moreover, CAs help build trust in cloud services by creating a secure and encrypted connection. This trust is twofold: it assures service providers that their data and services are secure and gives users confidence that their information is protected. In a digital ecosystem where trust is as valuable as the data itself, the assurance provided by CAs is indispensable.
Adapting to Cloud-Specific Needs
As cloud technology evolves, the role of CAs has also expanded. Beyond just providing traditional certificates, they now offer cloud-specific solutions. These include managing multiple certificates across various cloud services and ensuring seamless security in hybrid cloud environments. This adaptability is key in addressing the unique challenges posed by cloud infrastructures, where resources are often dynamic and distributed.
Challenges and Considerations
While Certificate Authorities (CAs) are essential, with their challenges, the centralized nature of traditional CAs can be a potential vulnerability. If a CA is compromised, it could lead to significant security breaches. Therefore, a more resilient approach in the cloud environment is necessary. This may involve using distributed ledger technologies, like blockchain, to decentralize trust or implementing automated systems to manage the lifecycle of certificates more efficiently.
Furthermore, choosing the correct CA and the appropriate type of certificate is critical for ensuring cloud security. Organizations must carefully evaluate the reputation, reliability, and variety of certificates a CA offers. It is also crucial to understand that while firms provide expert consultancy and advice in these areas, they may not be involved in directly implementing cloud technology solutions.
Wrap-Up
The role of Certificate Authorities in cloud security is multifaceted and indispensable. By ensuring the authenticity of entities and encrypting data, they build a foundation of trust in the cloud environment. However, with the dynamic nature of cloud computing, the role of CAs is continuously evolving, requiring innovative approaches to address new challenges.
Navigating these complexities often benefits from the support of resources and advisory services, which can provide valuable guidance and help organizations make informed decisions in their cloud security strategies. The future of cloud security is closely tied to the evolution and adaptation of Certificate Authorities, underscoring their ongoing importance and relevance.
Continue Reading:
Difference between Intermediate Certificate and Root Certificate
Network Security vs Cloud Security



