Palo Alto Cloud NGFW for Azure: Cloud Security
Firewalls are a key component in perimeter security. Firewalls have come a long way starting from stateful inspection technique to Next Generation firewalls (NGFW) and now a firewall which is machine learning (ML) aware and delivered as cloud native service which means no need to worry about purchasing highly priced hardware-based firewalls which required ongoing maintenance and upkeep.
In today’s topic we will learn about the Palo Alto Cloud based Next Generation firewall for Azure, its features, and architecture and how it works?
About Palo Alto Cloud NGFW for Azure
Cloud NGFW is a machine learning (ML) aware cloud native service. Multiple applications can run securely with cloud NGFW in place matching cloud speed, agility and on demand scaling. It is an extension of Palo Alto threat prevention capabilities and native integration into cloud. It stops web-based attacks, vulnerabilities, exploits including sophisticated file-based attack with patented technology of App-ID traffic classification
Cloud NGFW provides:
- Reduction in infrastructure management overhead
- Web based and zero day-based threats can be stopped in real time
- Web applications securely connect to legitimate web-based services
- Simplified native cloud provider experience with consistent and simple firewall policy management across multi-tenants
- Automation of end to end workflows having support of APIs, ARM templates and Terraform tool
Palo Alto Cloud NGFW Architecture
The cloud NGFW is an native ISV service of Microsoft Azure. Palo Alto develops and manages FWaaS (Firewall as a Service) using hooks provided by Azure service to leverage FWaaS (Firewall as a Service) via Azure APIs and UI. The cloud NGFW is available in the Azure marketplace. The components of cloud NGFW for Azure includes:
- Cloud NGFW – is managed Azure regional service made available in selected Azure regions
- Next generation firewall (NGFW) is offered as a resource associated with customer VNet or vWAN hub. It is scalable, resilient and manifests itself as a private IP address in the NGFW subnet specified by the user. VNet UDRs need to be updated to send traffic through these IP addresses.
- NGFW Rulestack – resource includes security rules set along with associated objects and security profiles for advanced access control using App-ID and URL filtering capability, threat prevention etc. local rulestack can be associated with multiple NGFWs.
Using cloud NGFW you can secure inbound, outbound traffic and East-West traffic.
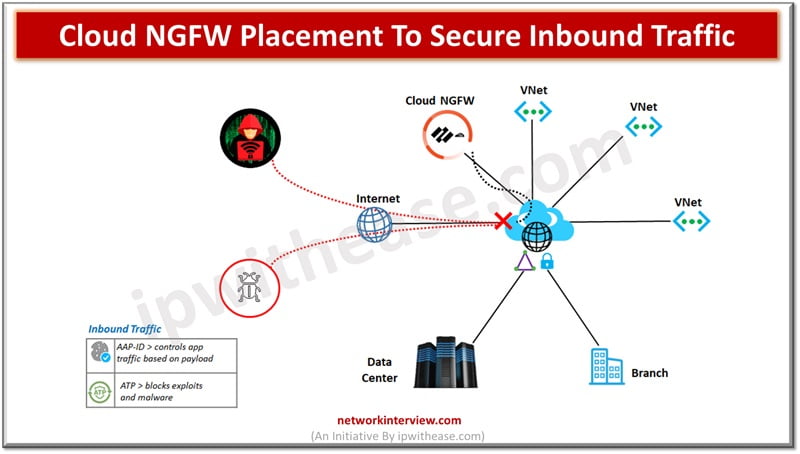
Inbound traffic is controlled by App-ID for application based on payload. Cloud NGFW prevents vulnerabilities and exploits entering the VNet in inbound traffic allowed by Azure security groups. (ASGs)
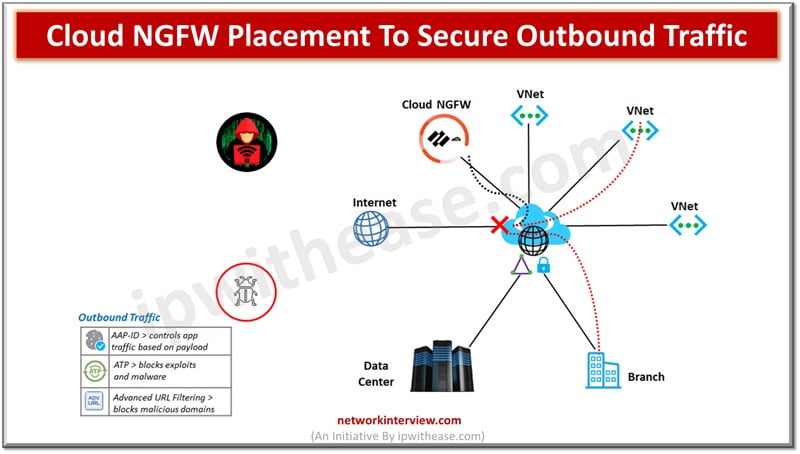
Outbound traffic is the traffic originate within the application is protected by ensuring resources in the application VNet connect to only allowed services and URLs and prevents exfiltration of sensitive data.
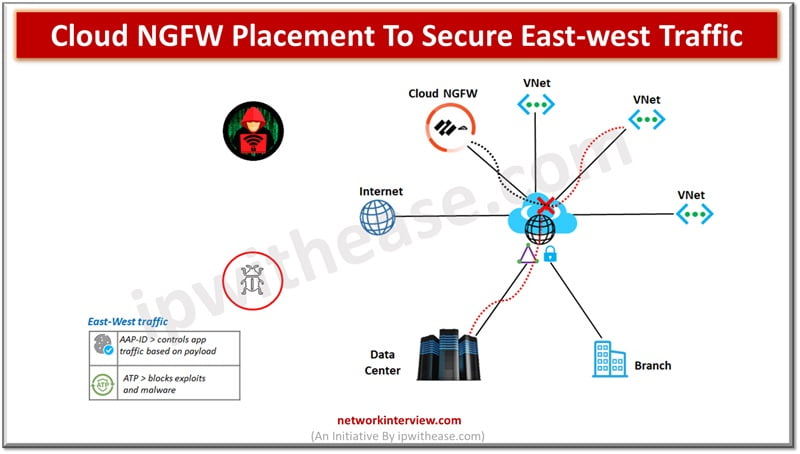
East-West traffic is the traffic inside Azure region. Traffic between source and destination is deployed in two different VNet s or in two different subnets under the same VNet. Cloud NGFW stops malware propagation within Azure hence blocking lateral movement of hackers within the environment.
Capabilities of Cloud NGFW for Azure
The cloud NGFW for Azure includes capabilities in various fields as depicted below:
- Administration and cloud deployments – Enablement of NGFW capabilities in Azure environments with ease of management of 0 day and day N operations on NGFW resources in cloud similar to any other Azure service
- Complete control and visibility into applications – App-ID and URL filtering provides application awareness and control
- Next generation threat prevention includes secure cloud delivery and prevention signatures across physical and software base
- Securing network traffic across VNets and vWANs.
- Gateway Load balancing (GWLB) provides high availability and scalability with an automated cloud firewall approach which scales up as traffic grows and handles increased throughput demands.
- Integration of security with cloud provider processes. Cloud provider security architecture could be used while onboarding, monitoring and logging.
Tag:PaloAlto



