Palo Alto Prisma Access: SASE
What is Palo Alto Prisma Access?
Palo Alto Prisma Access is a Cloud service provided by Palo Alto Networks. This service provides secure access to Internet and business applications that may be hosted on SASE, a corporate headquarters, Data Centres, OR instances that you may have running inside of Public Cloud.
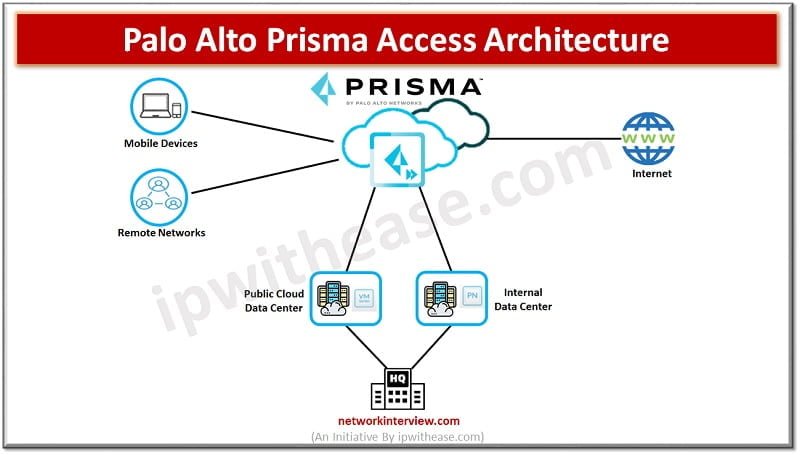
Let’s discuss the above given diagram to understand the Prisma Access :
Prisma Access deployed in the middle of a data centre or headquarters, your mobile users and remote networks and the Internet. This kind of set-up allows Prisma Access to inspect and analyse all traffic. To identify applications, threat, content, and it provides visibility into the use of SASE applications and ability to control which SASE applications are available to use by your users.
Being a Cloud service, Prisma also allows you to avoid the challenges of figuring out what type of Hardware to buy (It provides Scalability). It also minimises the coverage gaps or inconsistencies associated with distributer organisations.
In the past perhaps you have multiple point solutions for remote access that you had to deploy across your enterprise and the access was not the same, the user experience was also not the same.
All these scenarios create in-consistencies in how these point products were managed. Well, in Prisma Access you don’t need to worry about these because it all encompassed within the cloud services. We can shrink or expand our requirement based on the user’s load and avail cloud services accordingly. If the number of users connected decreases, we are able to decrease the amount of compute resources that are allocated to Prisma Access.
Let’s take a look of individual components of Prisma Access:
Palo Alto Prisma Access for Mobile Users
Palo Alto Prisma Access for Mobile Users provide security services that Palo Alto Networks is known for. For example, App-ID, User-id, Threat-Prevention, DNS-Security, Enterprise-DLP, all these services are available with Prisma Access.
Prisma Access also provides an alternative to the traditional on-premises deployment of Remote Access VPN. Instead of having multiple solutions at various locations, you can manage it as part of a Unified Service in a single pane of glass.
You are able to select locations that are suitable for users. Prisma Cloud Access has more than 100 locations available to choose from, it includes locations in regions like Africa, Asia, Australia, New Zealand, Europe, Japan, Middle East, North America, Central America, South America.
You can also enable Prisma access with Mobile users in Hybrid-network in which Mobile users combine with on-premises firewalls that can run Global Protect Gateways for areas where Palo Alto Networks don’t have coverage. If you are familiar with Global Protect, the functionalities are very similar,
- Users will connect to the portal,
- Then the portal will decide which is the best available location for that specific user,
- It will connect to that location; the user will build the IPSec tunnel to that location.
- Then traffic gets sent through that tunnel to the Prisma Access.
From Prisma Access, the traffic will split to the direct out to the Internet from the cloud service OR leverage the service connection to reach internal resources that you may have stored in Headquarters, DC, in your Cloud Instances. All of this is logged, and all the logs are sent to the Cortex Data Lake.
Palo Alto Prisma Access for Remote Networks
Palo Alto Prisma Access for remote networks provides security services just like it does for mobile users (App-ID, Threat-Prevention, User-id)
Enabling your remote network to safely use common applications and web access. Remote Access connects to Prisma Access via industry IPSec VPN cable devices (don’t need Palo Alto Firewall at both ends). Any firewall which supports IPSec VPN can connect with Prisma Access and we can send that remote site’s traffic to, so that traffic may be forwarded to the Prisma Access and provide internet access to internal DC or H.Q resources through a service connection.
See below image -> features of Remote Network Setup
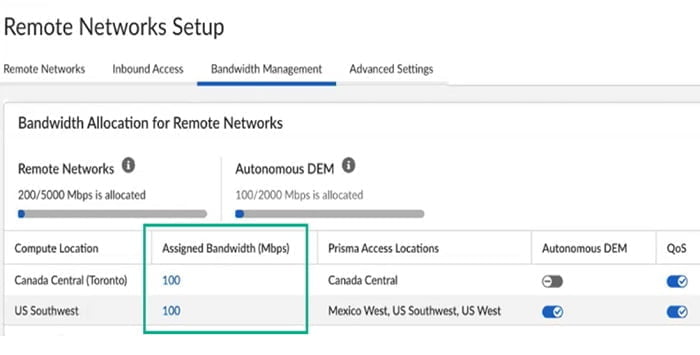
Prisma Access for remote networks are managed in the same manners as Mobile users so, you can use a single pane of glass to manage all of these remote sites.
Let’s take a look at Service Connections.
Service Connections
Service connections are glue that hold everything together, they connect Prisma Access to your H.Q or Data Centre resources. It also leverages IPSec tunnels for secure transport over the internet.
These are Layer 3 router connections which can accommodate static or dynamic routing and can terminate any IPSec capable firewall, router or SD-WAN device that may be sitting on your premises.
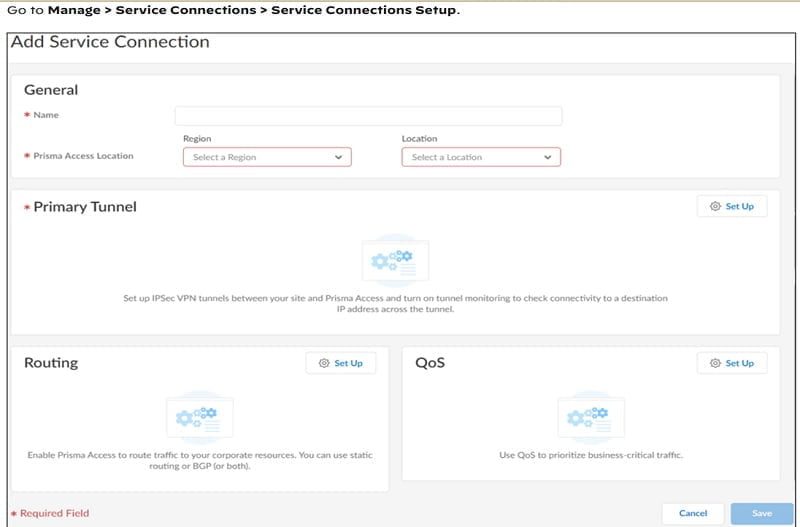
These terminate on a corporate access node on the Prisma Access end of the connection and the service connections are what provide the inbound connectivity to those centrally located resources that may be sitting in your Headquarters, DC. Below image can explain the set-up process to enable Service Connections in Prisma.
- It covers tunnel information
- Routing
- QoS (Bandwidth Allocation)
The difference between Remote Network and Service Connection is
- Remote Network can do outbound and inbound connectivity
- Whereas Service Connections are only for inbound connectivity
In Service Connection you can route traffic to Prisma Access to the internet.
Palo Alto Prisma Access Management Methods
There are two methods which are used to manage Prisma Access
- First method is via the Cloud Service plug-in on a Panorama managed device. If you are already a consumer of Palo Alto Network device, you can use same Panorama with a Cloud Services plug-in to manage your on-premises firewall and Prisma Access through Panorama.
- Second option is Cloud Manage; this is also a Cloud provider service. If you don’t have Panorama or are new to Palo Alto Networks, this will be the easiest way to get Prisma Access. It’s ability to deploy Prisma Access and use Prisma Access service without need to deploy another on-premises device OR VM (Virtual-Machine) on which you may have to run services.
Plao Alto Prisma Access uses Cortex Data Lake to store logs. Cortex Data Lake stores the logging that happens for any of the actions taken by Prisma Access. You can forward logs to any other device by redirecting the logs from Cortex Data Lake to on-prem device or log server.
Continue Reading:
Palo Alto vs Fortinet Firewall: Detailed Comparison



