Intrusion Prevention System: Network Security
Network security is designed to protect organization information by protecting the integrity of the network from unauthorized access and threats. The system networks are linked to daily transactions and communication within the organizations private or government which need security. The most common and straightway strategy of protecting networks comprises three principles – Protection, detection and reaction.
Network security works at multiple layers of protection at the perimeter and in between the network. All security layers are required to follow specific policies so only authorized users will gain access to the network resources, and unauthorized users shall be blocked from executing exploit vulnerabilities and performing malicious activities.
We will learn more in detail about Intrusion prevention systems (IPS) which operate at Layer 3 (network layer) of OSI model, its features, functionality and use cases.
Intrusion Prevention System
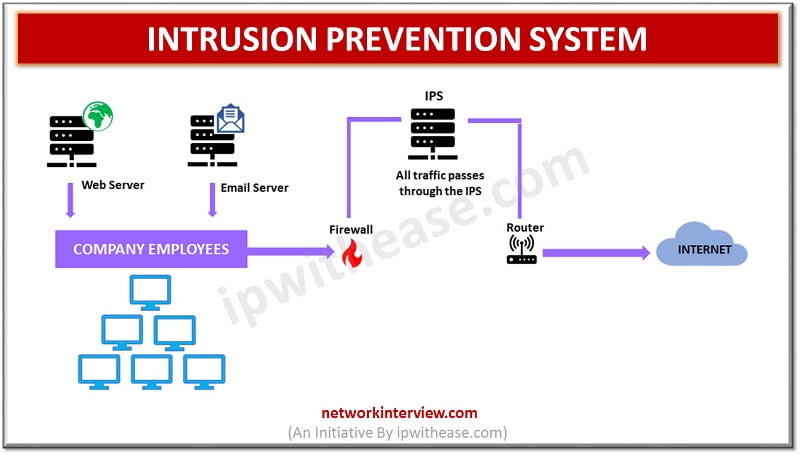
An Intrusion Prevention System is a network security technology which monitors network traffic to detect anomalies in network traffic flow. They intercept the network traffic and quickly prevent malicious activity by dropping packets or resetting the connections. They are a preventive measure as part of the incident response plan and overall incident management process.
Intrusion Prevention System is an online control system which can stop packets from being delivered based on security events as detected. Intrusion prevention systems often sit directly behind the firewall and placed inline (in direct communication path between source and destination) actively analysing and taking automated actions on all traffic which flows into the network.
How Intrusion Prevention System work?
Intrusion Prevention Systems work by scanning all network traffic coming in. There are a variety of threats which the Intrusion Prevention System is designed to prevent, including but not limited to the following – Denial of service (DoS) attacks, Various types of exploits, Trojans/ Worms / Viruses etc.
Intrusion Prevention Systems perform real time packet inspection and deeply inspect each packet which travels in the network. It can carry out variety of actions out of the one such as: –
- Termination of TCP session
- Blocking the offending source IP address or user account from application access efforts
- Reprogramming or reconfiguring firewall to prevent similar attack from happening again in future
- Remove or replace any malicious content which remains on the network post an attack which may involve repackaging payloads, removal of header information and removal of any infected attachments from files or email servers.
Intrusion prevention systems can be configured to use in a number of different ways to protect the network from unauthorized access which includes:
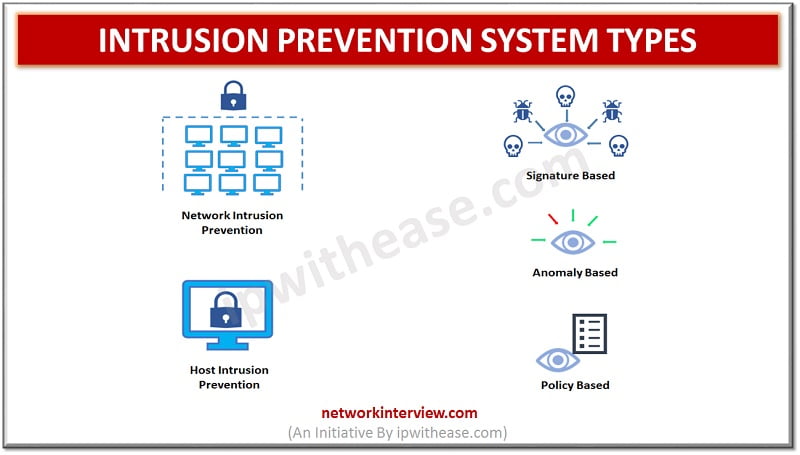
Signature based – there are predefined signatures of well-known network threats. When an attack happens, which matches with one of the stored signature patterns, the system initiates required action like blocking, repackaging etc.
Anomaly based – This approach monitors any abnormal or unexpected behaviour on the network. And if an anomaly is detected the system blocks the target host immediately which is responsible for unexpected behaviour.
Policy based – This approach requires administrators to set and configure security policies as per organizational security policies and network infrastructure. When an activity occurs, which violates organizational security policy an alert is triggered which is sent to system administrators to take corrective/ preventive action.
Types of Intrusion Prevention System
Intrusion prevention systems are basically of four types: –
Network based – monitors network traffic by analysing protocols activity. It prevents malicious activity by analysing protocol packets. Post installation it will gather information from a host console and network to identify permitted hosts, applications and operating systems which are used commonly within the network. It uses signature-based detection to identify threats.
Host based – as the name suggests used to analyse activity of a single host to detect and prevent malicious activity. They analyse code behaviour using both signature and anomaly-based detection methodology. It can prevent access to sensitive information located on a host
Wireless Intrusion prevention system – it operates on layer 2 (data link layer) of OSI model. It can detect presence of rouge or misconfigured devices and can prevent from operating on wireless enterprise networks by performing scan of network RFs for denial of service or any other forms of attacks.
Network behaviour IPS – it comprises anomaly-based detection mechanism, which looks for deviations from known ‘normal’ behaviour. anomaly based detection requires a training period in which a profile which is normal is constructed over a period of time and any inconsistencies with the profile are tagged as malicious.
While evaluating security solutions for your network we need to keep in mind the corporate infrastructure, internet threats which are becoming more and more.
Continue Reading:
Types of Firewall: Network Security
Common Types of Attacks on Routers
Tag:Security



