What is CRC (Cyclic Redundancy Check)?
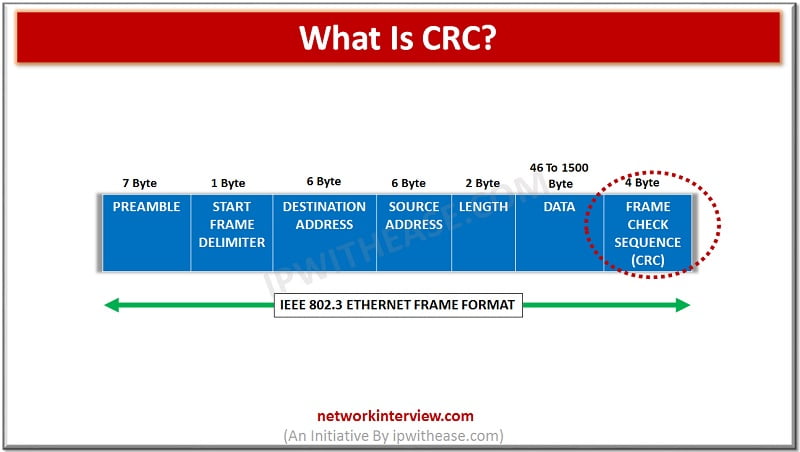
To detect the error in any type of digital data, CRC is used. CRC stands for Cyclic Redundancy check. It is a type of has function that will automatically detect even the minor changes in the raw data of the computer. CRC is generally used for Network communication. Infact, Ethernet frames have a section specifically defined for CRC (4 byte long), considering how important transmission of correct data is. Moreover, it is also used in storage devices such as hard disk as well as other storage devices. When there are some errors in the data or there is slight unusual change, the CRC will automatically detect it and warn the user.
Working and detection
CRC works with a simple technique. Whenever the data is to be transmitted, a computed amount of check bits are appended to the data. These bits are also called checksum. Once it is assigned to the data, the data is then transited to the destination. The checksum is also maintained at the destination side.
Upon receiving the data in the destination, it is checked for all the errors using those checksum. The goal is to ensure that checksum of the received data is same as the checksum received. If there are any mathematical data changes, a negative acknowledgment is sent. Hence, the data is re transmitted and hence the user receives the correct data.
If we see the technical side, the data receivers, first of all, will check the value of the data. It is done by looking for the remainder of the content’s polynomial division. Using this procedure, it is confirmed whether the data is transmitted as it was, or there is error occurred in between the data transmission.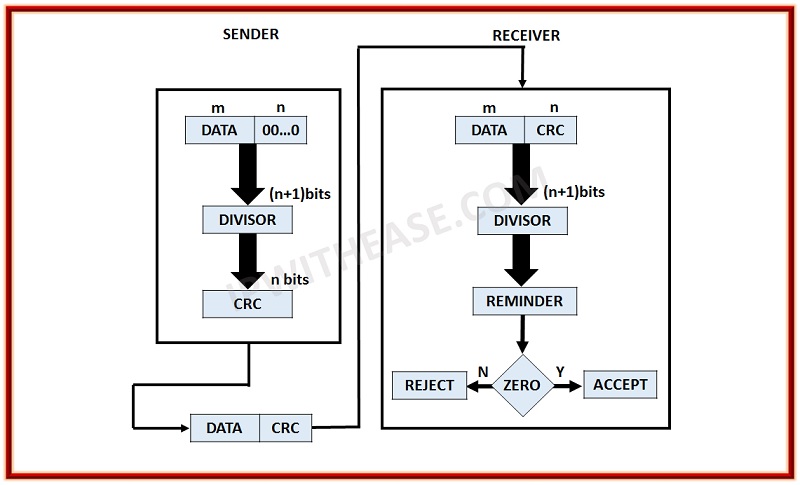
Real-life example
Let’s talk about the real-time example of the CRC working. As we have seen above, CRC is also used in hard drive. There is a checksum allocated to each and every block in the hard drive. Whenever a hard drive is connected with the computer, the computer will first check the checksum of each of these blocks. If there are any issues with these blocks and checksum is not matched, a negative acknowledgment is sent and the CRC is reported.
In such cases, a computer can identify if the whole block is corrupted or any particular file is corrupt. This generally happens when the system crashes or files we are transferring are incomplete or corrupted. Also, if there are more amount of bugs in the file, it will show an error while computing the checksum and hence you will not be able to check the files.
The CRC design will totally depend on the length of the block. If the hard disk has more space, the blocks are also of a bigger size. Hence, the CRC design is made accordingly. In the same way, the protection features and resources will depend on the block. Moreover, the performance and the speed of the CRC detection will totally depend on the model. Therefore, if the standard model is used, the performance will also increase. Generally, a small-size storage device won’t need more speed as it can easily be completed in less amount of time.
Related – MD5 vs CRC
More about CRC
The CRC technique is not new and is being implemented from last many years. It was first invented in 1961 by a W. Wesley Peterson. It was developed by Comité Consultatif International Telegraphique et Telephoniquealso known as CCITT. First of all, it was a simple technique which was implemented in the hardware unit to check if there are any errors. Wesley came to know that errors can easily be analyzed mathematically and hence the technique was introduced.
The whole technique works on mathematics and more precisely on Binary division. Therefore, it is also known as Polynomial code checksum. First of all, the binary division is done of the polynomial function and once it is found, the remainder is taken into consideration to check it further.
Since then the technique is implemented wherever possible. Later on, the same technique was also implemented in the re-writable CD/DVD to ensure the copied materials and files are error-free. Now, it is used in almost every storage device and also on many other devices where there are chances of errors. The model of the CRC is different depending on the device it is implemented.



