What is a Port?
In networking, a port is defined as the endpoint of any data communication. This applies to a kind of data transfer whether they are using a wireless connection or these re physical connections. In the same way, when it comes to the software level, a port is nothing but the logical construct that is used to identify the process or the network service that is being used.
There are different ports for each of the protocols and the addresses out there, these can contain up to 16-bit of space. These are basically just the unsigned numbers and the number is called a port number .The port number range from values of 0 to 65535.
Different kind of protocols use a port number, the two most popular protocol that is using port number are
- TCP (Transmission Control Protocol)
- UDP (User Datagram Protocol)
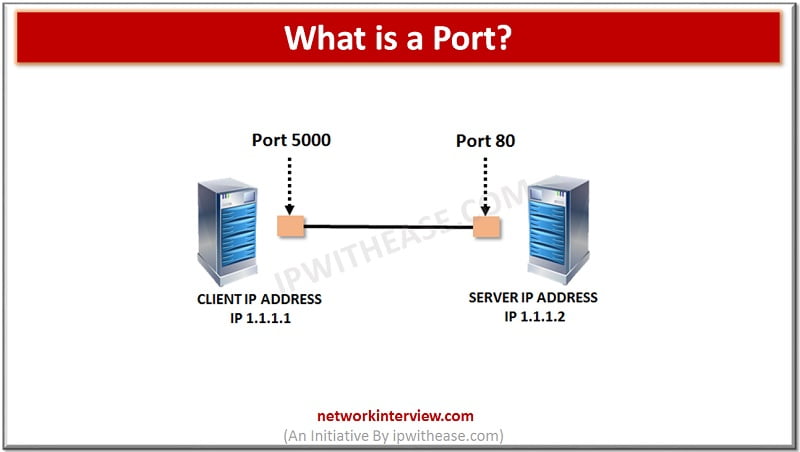
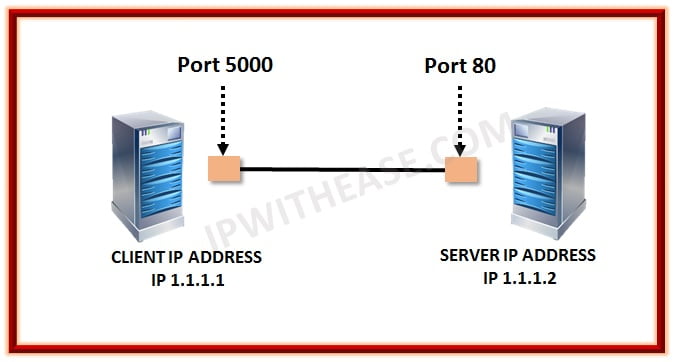
All port numbers are directly associated with one of the IP addresses of the host as well as there is one or more protocol that it follows for the data transmissions. A port number is used to get the final destination or the origin of the network for any particular message received. In this way, the message or the packet that is arrived is forwarded to their own destination using the port number. Therefore, for all these usages, it is necessary to have a port number when transferring data using any of the networks. Below is an example scenario where Client with IP address 1.1.1.1 and port number 5000 needs to communicate with Web server, which has IP address 1.1.1.2 and port number 80. Generally communication with Web server is on HTTP with TCP protocol.
Handling and Managing the port numbers
As we have seen above, the port number is managed by the operating system or the network itself. The point is who controls the global DNS route and the port number. These are controlled by IANA (Internet signed Numbers Authority). IANA also controls all the other things such as IP Address, DNS, port number, etc for mostly all internet services.
There are three kinds of the port number
- Well known ports
- Registered Ports
- Dynamic or commonly known as private ports
Well, known ports are already defined for specific purposes and already defined by the system. Therefore, it is also called System port. One can use these ports but the rules to use these ports are different and it is hard implementing these for different usage. The range includes from 0 t 1023.
In other words, one might not be able to define the port number in these series. Most of the people who are working with any kind of network will know most of these port number and the usage. In this way, they can use any port number easily for the given purpose.
Well known common port number
These are some of the common port numbers that are sued for specific services. These can be different but in most of the cases, these are the port number used.
- 20: File Transfer Protocol (FTP) used in Data Transfer
- 21: File Transfer Protocol (FTP) used in Command Control
- 22: Secure Shell (SSH) to make sure login in secure
- 23: Telnet remote login service that is used for decrypting text messages
- 25: Simple Mail Transfer Protocol (SMTP) used for E-mail routing
- 53: Domain Name System (DNS) service
- 80: Hypertext Transfer Protocol (HTTP) mostly used in the World Wide Web
- 110: Post Office Protocol (POP3)
- 119: Network News Transfer Protocol (NNTP)
- 123: Network Time Protocol (NTP)
- 143: Internet Message Access Protocol (IMAP) Management of digital mail
- 161: Simple Network Management Protocol (SNMP)
- 194: Internet Relay Chat (IRC)
- 443: HTTP Secure (HTTPS) HTTP over TLS/SSL
Port scanning
Port scanning is the procedure to scan all the ports available in the system or any network. There are various tools available that will give me information for any specific ports. Port scanning is done in order to ensure that the network is working properly without any issues. If there is a port that is not catching enough signals, there are chances that something might be wrong with the network or the system.
Moreover, port scanning has much other uses such as it is used for security purpose when there is an attack. Sometimes, there might be more than one service that uses the same port number, one can use the port scanning technique to make sure that the port number they want to use is free or one can know which process or service is using that particular port number.
Tag:protocol



