Introduction to Sophos UTM Firewall
Firewalls have come a long way and have been there for decades to provide protection against malicious attacks and intrusions. In their infancy days firewalls were a simple filtering mechanism based on ports and IP addresses. But over time, firewalls become more and more sophisticated as the cyber-attacks are. The Next generation firewalls (NGFWs) changed the entire game and bought in not just simple inspection feature but bundle of multiple capabilities such as malware protection, intrusion detection etc.
In today’s article we will look at Unified threat management-based Sophos firewall, understand its features, capabilities and uses.
What is Sophos UTM Firewall?
In the year 2003, several vendors launched ‘all in one’ security products and IDC has coined a new term in the class of firewalls known as Unified threat management (UTM).
UTM firewalls have multiple security features bundled into one appliance to provide robust protection against network attacks along with a single management interface common for manufacturers to bring in a centralized platform to enable features, policies and rules. Organizations were no longer needed to deploy multiple devices each with its own management dashboard and individual login credentials to defend against threats.
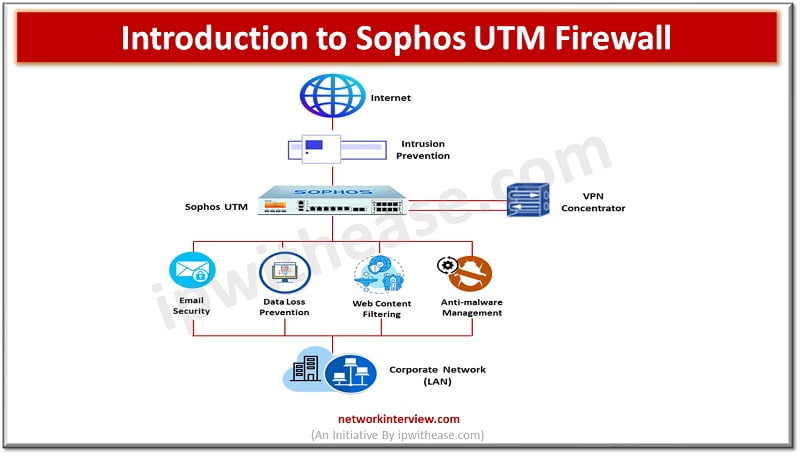
Sophos UTM gives complete security from network firewall to endpoint anti-virus protection with a single modular appliance.

Features of Sophos UTM
- Firewall with VPN, ATP, IPS, email, web filtering, and application control.
- It is software based or cloud-based appliance flavours.
- It has intuitive browser-based interface and complete control over all features.
- Remote office secure connectivity with VPN and Wi-Fi. UTM also works as wireless controller; access points are automatically set up and get complete UTM protection.
- Reverse proxy authentication for additional layer of security for enterprise applications.
- UTM sandbox provides advanced cloud-based sandbox protection such as targeted attack protection, visibility, and analysis, block evasive threats with granular incident-based reports.
How to setup Sophos UTM firewall?
Let us look at basic requirements before installing Sophos UTM firewall. The minimum hardware requirement for installation and usage of UTM is as follows
- Processor – Intel Atom Dual core with 1.46 GHz or compatible
- Memory – 2 GB RAM
- HDD – 40 GB SATA hard disk or SSD
- CD-ROM drive – Bootable IDE or SCSI CD-ROM drive
- NIC – two or more PCIe 2.0 Ethernet network interface cards
- USB (optional) – one USB port for communications with a UPS device and one USB port for connecting to Sophos UTM smart installer (SUSI)
- Switch (optional) – A network device which connects network segments
Sophos provides a list of hardware devices compatible with UTM software which is available on their website in knowledge base.
Client PC used for web admin require below configuration:
Processor: clock signal frequency 2 GHz or higher
Browser: Latest version of Firefox, Google Chrome, Safari, last two versions of Microsoft Internet explorer. JavaScript must be enabled and browser must be configured not to use a proxy for the IP address of Sophos internal network card (eth0).
Before starting installation make sure you have Sophos UTM CD-ROM and license key.
Step 1: Boot PC from CD-ROM or mount the downloadable ISO image on virtual drive.
Step 2: Installation screen will appear.
Step 3: Select start installation.
Step 4: Hardware detection will be performed and detected hardware screen is displayed.
Step 5: The select keyboard screen is displayed.
Step 6: Choose your keyboard layout e.g., English (UK) and press enter to continue.
Step 7: Select your area.
Step 8: Select your time zone.
Step 9: Set date and time.
Step 10: select an internal network card to use the Webadmin tool to configure the rest of UTM.
Step 11: Configure the administrative network interface.
Step 12: Install the 64-bit kernel.
Step 13: Accept installation of enterprise toolkit.
Step 14: Press enter to start installation.
Step 15: Remove CD-ROM from drive and connect the eth0 network card to internal network.
Continue Reading:
FortiGate UTM (Unified Threat Management)
6 Types of Firewall: Network Security
Tag:Security



