Palo Alto SSL Decryption
Before digging deep into Palo alto SSL Decryption, let’s first understand what is Decryption?
What is Decryption?
Palo Alto firewalls can be decrypt and inspect traffic to gain visibility of threats and to control protocols, certificate verification and failure handling. Decryption can apply policies on encrypted traffic so that the firewall handles encrypted traffic according to the customer’s configured security policies. Decryption is carried out for traffic content that entering into network and encryption is performed for content that leaving network. Below are different ways that Palo Alto can help decrypt traffic.
- SSH Proxy
- SSL Inbound Inspection
- SSL Forward Proxy (SSL Decryption)
SSH Proxy
SSH Proxy is a way that the firewall can decrypt and inspect tunneled SSH traffic passing through the firewall. It does not require certificates and the key used to decrypt SSH sessions is generated automatically on the firewall during boot up. With SSH decryption enabled, the firewall decrypts SSH traffic based on your decryption policy. Traffic is re-encrypted as it exits the firewall.
Configuration of SSH Proxy
Step 1. Configure interfaces as either virtual wire, Layer 2, or Layer 3 interfaces. Decryption can be performed on virtual wire, Layer 2, or Layer 3 interfaces of firewall.
Step 2. Create a decryption policy rule for SSH proxy to define traffic for the firewall.
Step3. Commit the configuration.
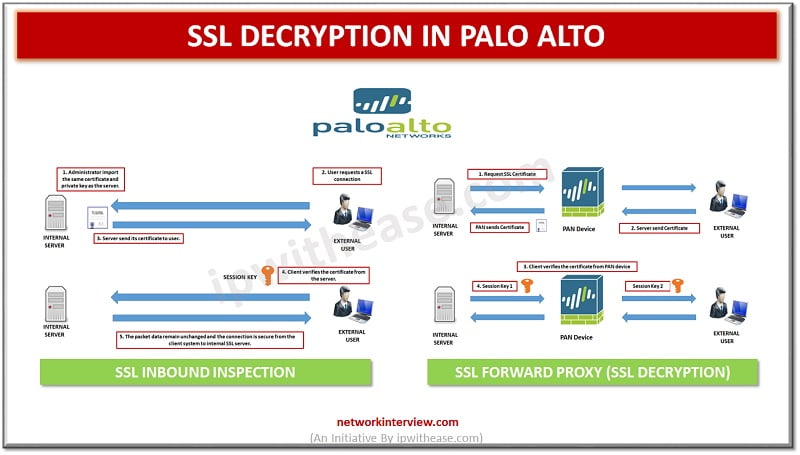
SSL Inbound Inspection
SSL Inbound Inspection is required to inspect the communication of a web server protected by the firewall, to decrypt the traffic using the internal web servers SSL Certificate. With an SSL Inbound Inspection decryption policy configured, the firewall decrypts all SSL traffic. Firewall blocks, restricts, or allows the traffic based on the decryption profile applied to the traffic, including any configured Antivirus, Vulnerability Protection, Anti-Spyware, URL-Filtering, and File Blocking profiles.
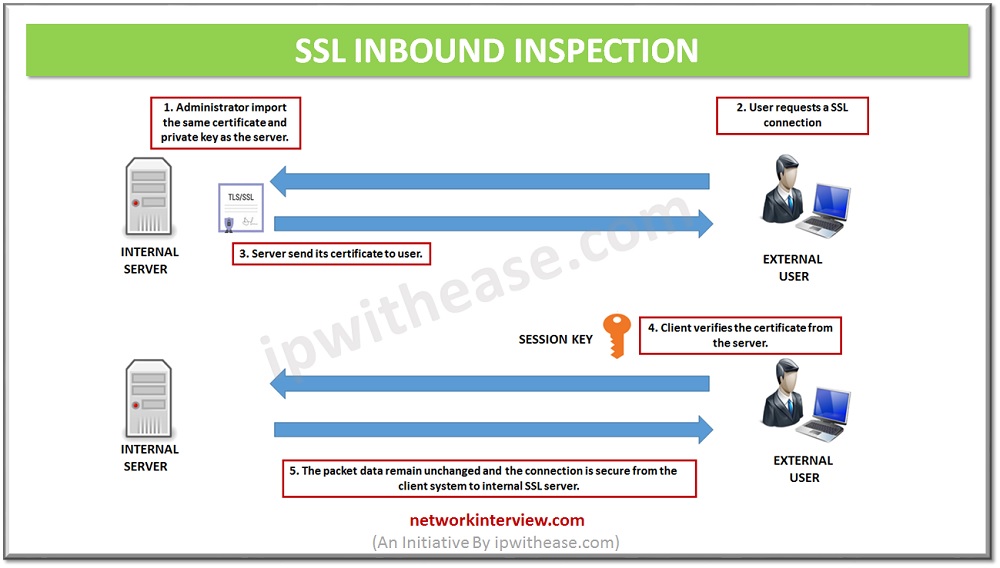
Configuration of SSL Inbound Inspection
Step 1. Configure interfaces as either virtual wire, Layer 2, or Layer 3 interfaces.
Step 2. Make sure certificate is installed on the firewall.
Step 3. Create a decryption policy rule SSL Inbound Inspection to define traffic for the firewall.
Step 4. Configure the firewall to forward decrypted SSL traffic for WildFire analysis.
Step 5. Commit the configuration.
Related – Palo Alto Firewall Architecture
SSL Forward Proxy (Palo Alto SSL Decryption)
SSL Forward Proxy (SSL Decryption) is an advance feature of firewall to inspect traffic inside the SSL encrypted packet. SSL Decryption is the ability to view inside of Secure HTTP traffic (SSL) as it passes via the Palo Alto Networks firewall:
- Without SSL Decryption: Firewall has no access to the information inside of an encrypted SSL packet.
- With SSL Decryption: Traffic generated from source own network, there will be visibility into the SSL packet to find hidden applications and threats inside SSL traffic.
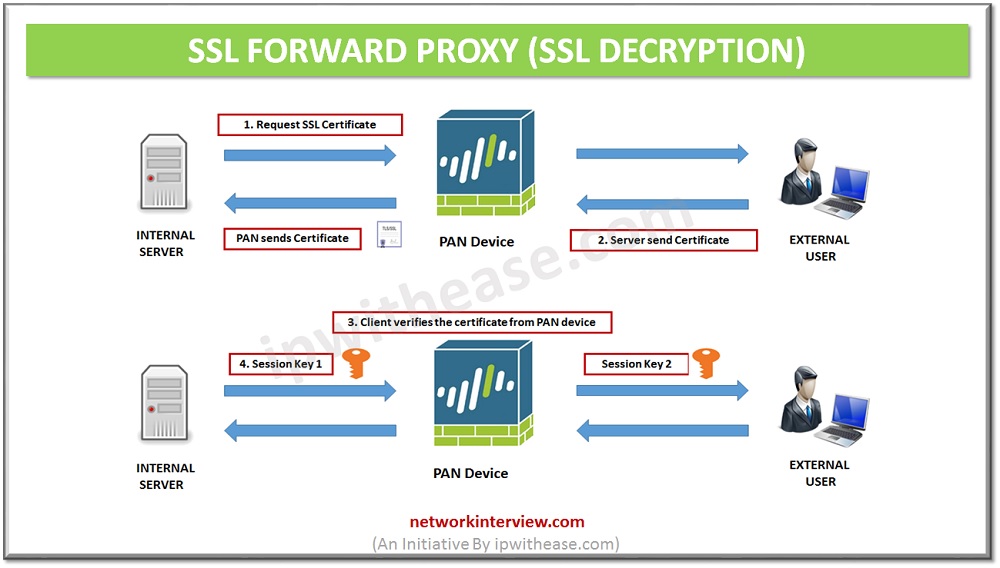
Configuration of SSL Forward Proxy
Step 1. Configure interfaces as either virtual wire, Layer 2, or Layer 3 interfaces.
Step 2. Configure the SSL Forward Trust certificate for the firewall to clients when a trusted CA has signed the server certificate.
Step 3. Distribute the SSL forward trust certificate to client system certificate.
Step 4. Configure the Forward Untrust certificate.
Step 5. Configure the Key for SSL Forward Proxy Server Certificates. SSL forward proxy server’s default key size based on the key size of the destination server certificate.
Step 6. Create a Decryption Policy Rule for SSL Inbound Inspection to define traffic for the firewall to decrypt.
Step 7. Configure the firewall to forward decrypted SSL traffic for WildFire analysis.
Step 8. Commit the configuration.
TLSv1.3
TLSv1.3 is the latest version of the TLS (Transport Layer Security) protocol, which is the improved version of SSL.
Verify Decryption
- View decrypted traffic sessions.
- View SSL Traffic sessions that are not decrypted in session logs.
- View the log for a particular session in the decryption log by applying filter on the Session ID.
- View all TLS and SSH traffic, filter the traffic logs to view both decrypted and undecrypted TLS and SSH traffic.
Conclusion
SSL Decryption refers to view inside of Secure HTTP traffic (SSL) as it passes via the Palo Alto Networks firewall. Before SSL Decryption, Palo Alto firewall would have no access to the information inside an encrypted SSL packet. Palo Alto firewall decrypts the SSL traffic to allow Application Control features such as the URL Filter, Virus Scanner, or File Content policy to scan the traffic. It dynamically creates a certificate and signs it with the SSL Inspection root certificate.
Continue Reading:
SSL Certificate types : Intermediate Certificate and Root Certificate