Network Security Model and Cryptography
With the widespread use of Internet and cloud computing, social networking, e-commerce applications, a large amount of data gets generated daily. Data security is a very crucial aspect of network security as more and more people are using the Internet and society is moving towards the digital information age, cyber criminals are more active and using advanced techniques to gain access to organization’s life lines, their data. Network security and cryptography is used to protect network and data transmission over wireless networks.
In today’s topic we will look more in detail about the network security model which exhibits how security service is designed, its components, how it works and its features.
Network Security Model
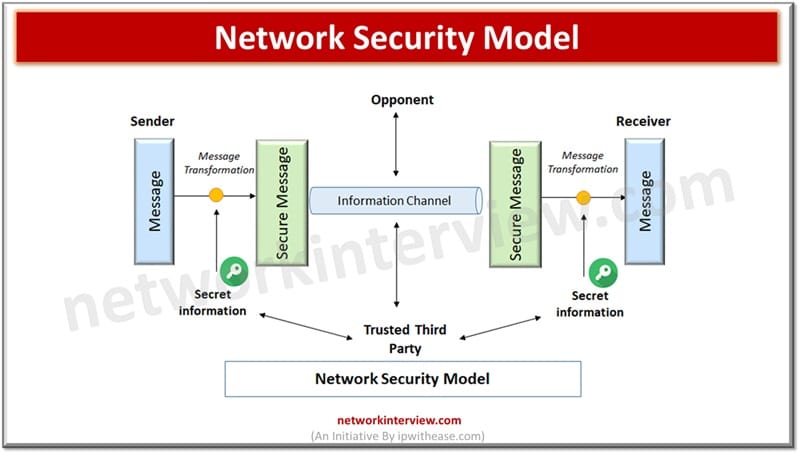
Network security model describes how a security service is designed to prevent cyber attackers from causing threat to confidentiality and authenticity of information transmitted or exchanged over the network. Exchange of messages happen between a sender and receiver and before transmission they need to mutually agree on sharing the message with this comes in picture is the communication channel or information channel which is an Internet service.
When message is transmitted over the network between sender and receiver, it involves three components from security service perspective namely:
- Transformation – of information which needs to be sent or received to be encrypted so that a cyber attacker is unable to intercept it. It may involve addition of code during the transmission of information which will be used to verify the identity of the receiver.
- Secret information / key sharing between sender and receiver is used to encrypt messages at sender end and decrypt at receiver end.
- Trusted third party is the one which should take the responsibility of distributing secret information / key to both sender and receiver involved in communication without the involvement of intruder or cyber attacker.
Network Security Model Architecture
The network security model above depicts two parties in communication where sender and receiver mutually agree to exchange information. Sender wants to send some messages to the receiver but cannot transmit them in clear text format as it would have risk of interception by intruder. So before sending a message to the receiver via an information channel, it should be transmitted in an unreadable format.
- Secret information / key is used to transmit a message to receiver along with key to make message readable to the receiver and thus a third party comes into the picture who would be responsible for distributing the secret information / key to both the parties involved in communication.
- An encryption key used in conjunction with transformation to scramble message before transmission and then unscramble it on receiving it.
- Encryption provides data protection while key management is required to enable access to data which require protection from unauthorized parties.
Cryptography
Cryptography is used to store / transmit data in a specific format so that only those from whom it is intended are able to process it. The cleartext is scrambled into ciphertext (known as encryption) and then back again, known as decryption. There are in general three types of cryptographic schemes commonly used: secret key (or symmetric) cryptography, public-key (or asymmetric) cryptography, and hash functions.
Types of Cryptography
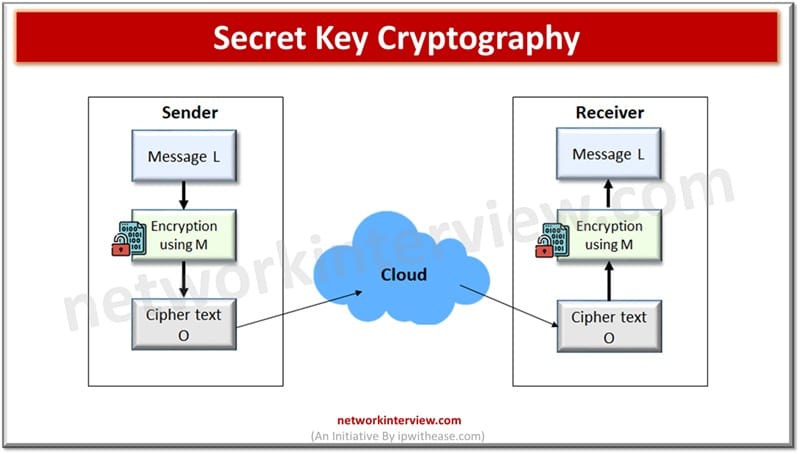
Secret Key (or symmetric) Cryptography
A single key is used for encryption and decryption both as depicted in figure below.
Sender A uses Key M to encrypt plaintext message L and sends the ciphertext O to the receiver. The receiver applies the Key M to decrypt the ciphertext O and recover plaintext L. Key must be known to both sender and receiver here.
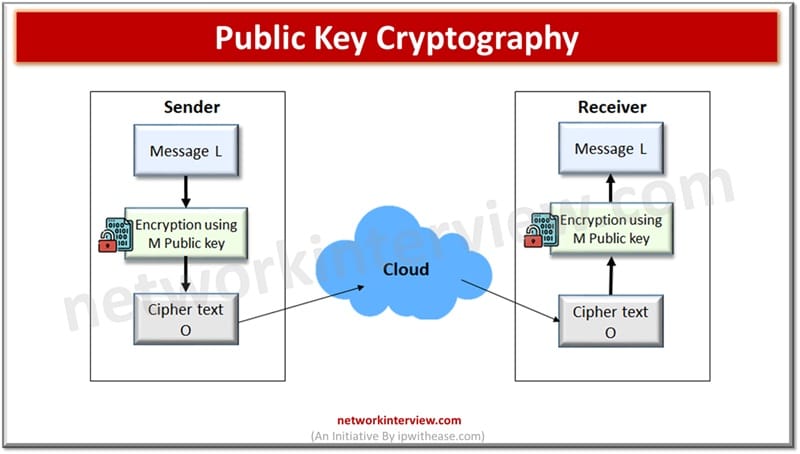
Public-key (or asymmetric) Cryptography
Encryption is performed using different keys – public and private key. Sender uses the public key of the receiver to encrypt plaintext message L and sends ciphertext O to the receiver. The receiver replies with its own private key to decrypt the ciphertext O and recover plaintext message L.
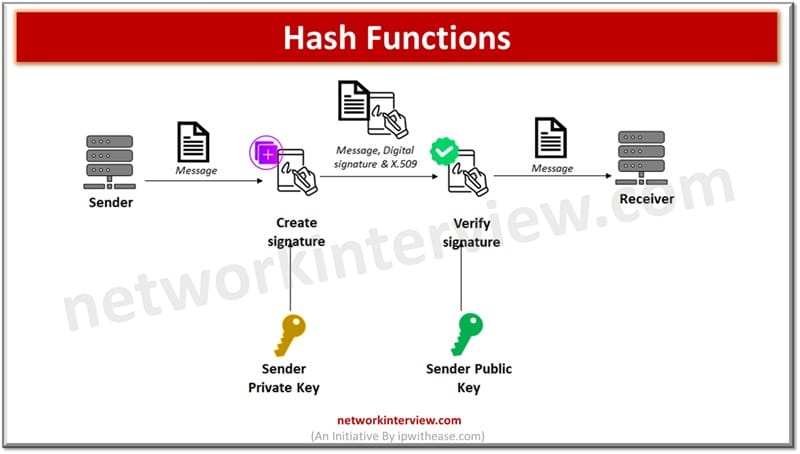
Hash functions
A digital signature is an authentication mechanism to enable the creator of a message to attach a code which acts as signature. Signature is formed by taking the hash of the message and encrypting the message with the creator’s private key. Signature is used to guarantee message source and its integrity.
Tag:Security



