High Availability Palo Alto
High availability (HA) refers to a system or component that is operational without interruption for long periods of time. High availability (HA) is measured as a percentage, with a 100% percent system indicating a service that experiences zero downtime.
High Availability (HA) Overview
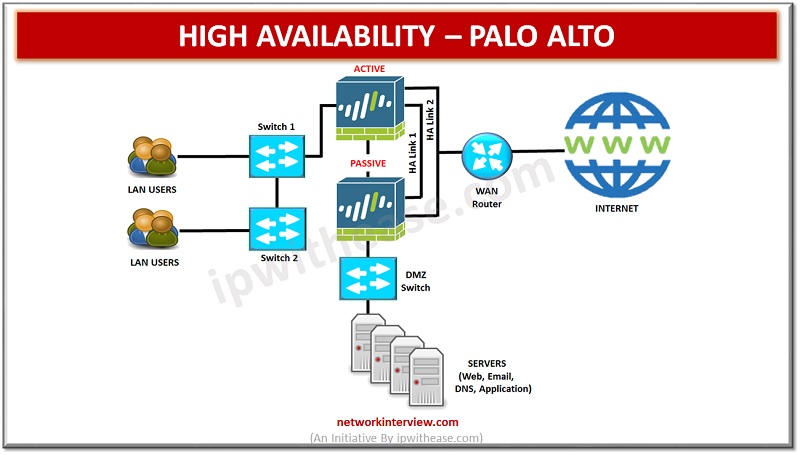
While setting up two Palo Alto firewalls as an HA pair, it is essential that HA peers same have same version of PAN-OS device. High availability (HA) minimizes downtime and makes sure that a secondary firewall is available in the event when the active firewall fails. Dedicated HA ports in the firewalls are used to synchronize data, object and policy configurations and maintain state information with passive firewall. There are some Firewall specific configuration which are not synchronized between peers such as management interface IP address and administrator profiles and log data and Application Command Center (ACC).
High Availability Modes:
There are two modes of firewall deployment in HA pair.
Active/Passive: In this mode, one firewall actively manages traffic while the other is synchronized and ready to transition to the active state if a failure occurs in network. Both firewalls in a HA mode share the same configuration settings and one firewall actively manages traffic. When the active firewall fails, the passive firewall transitions to the active state and takes over role as active node. A/P (Active/passive) HA is supported in the virtual wire, Layer 2 and Layer 3 deployments.
Active/Active: In this HA mode, both firewalls in the A/A mode process the traffic and work synchronously to organize session setup and session ownership. Both firewalls individually maintain routing tables and synchronize to each other. A/A (Active/ Active) HA is supported in virtual wire and Layer 3 deployments.
Failover
When a failure occurs in network where one firewall goes down and the other peer takes over the role, the event is called a failover. A failover is triggered when heartbeat and hello messages fail to respond, physical link goes down or ICMP response fails. Below is the explanation of each parameter: –
- Heartbeat Polling and Hello messages: Hello message and heartbeat polling is used to verify the status of peer firewall, i.e. whether it is alive and operational. Hello messages are sent from one peer to the other at the configured parameter.
- Link Monitoring: Physical interfaces to be monitored are grouped into a channel group and their state (link up or link down) is monitored.
- Path Monitoring: Path monitoring uses ICMP to verify reachability of the IP address. The default interval for ping is 200ms.
Device Priority and Preemption
Firewalls in a High Availability (HA) pair can be configured with a device priority value to highlight a preference for which firewall should consider as the active. Enable the preemptive behavior on both the firewalls and configure the device priority value for each firewall. Firewall with the lower numerical value, and therefore higher priority, is designated as an active and the other firewall is the act as a passive firewall.
Floating IP Address and Virtual MAC Address
In a HA deployment of A/A mode, floating IP addresses moves from one HA firewall to the other if a link or firewall goes down. Firewall responds to ARP requests with a virtual MAC address. Floating IP addresses are recommended when layer 3 redundancy functionality such as Virtual Router Redundancy Protocol (VRRP) is configured on firewall. It can also be used to implement VPNs and source NAT.
ARP Load-Sharing
In a HA deployment active/active configuration, ARP load-sharing allows the firewalls to share an IP address and provide gateway services. Use ARP load-sharing, when there is no Layer 3 device between the firewall and end hosts.
Route-Based Redundancy
In an active/active HA deployment, firewalls use dynamic routing protocols to determine the best path. In such a scenario, no floating IP addresses is necessary. If link failure or any topology changes occurs, routing protocol (RIP, OSPF, or BGP) handles the rerouting of traffic.
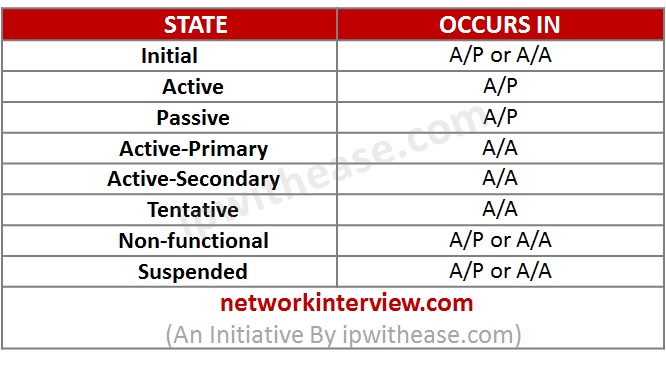
HA Firewall States
Configure Active/Passive HA
Step 1. Connect the HA ports physically and configure these port between the firewalls.
Step 2. Configure the ICMP or ping on the management port.
Step 3. If HA ports are not available in firewall, data ports can be configured to function as HA ports.
Step 4. Configure the HA mode and group ID.
Step 5. Configure the control link connection.
Step 6. (Optional) Enable the encryption for the control link connection.
Step 7. Configure the backup control link connection.
Step 8. Configure the data link connection (HA2) and the backup HA2 connection between the firewalls.
Step 9. Configure heartbeat as a backup if control link uses a dedicated HA port or an in-band port.
Step 10. Configure the device priority and enable preemption.
Step 11. (Optional) Configure the HA Timers.
Step 12. (Optional) Configure the link status of the HA ports on the passive firewall.
Step 13. Enable HA.
Step 14. (Optional) Configure LACP and LLDP Pre-Negotiation for A/P HA mode for quick failover if network uses LACP or LLDP parameters.
Step 15. Commit the configuration changes.
Step 16. Verify the firewalls are paired in active/passive HA.
Configure Active/Active HA
Step 1. Connect the HA ports physically and configure these port between the firewalls.
Step 2. Configure the ICMP or ping on the management port.
Step 3. If HA ports are not available in firewall, data ports can be configured to function as HA ports.
Step 4. Configure the active/active HA and set the group ID.
Step 5. Configure the Device ID, enable synchronization, and identify the control link on the peer firewall.
Step 6. Verify firewall device ID preempt value.
Step 7. Configure heartbeat backup if your control link uses a dedicated HA port or an in-band port.
Step 8. (Optional) Configure the HA Timers.
Step 9. Configure the control link connection.
Step 10. (Optional) Configure the encryption for the control link connection.
Step 11. Configure the backup control link connection.
Step 12. Configure the data link connection (HA2) and the backup HA2 connection between the firewalls.
Step 13. Configure the HA3 link for packet forwarding.
Step 14. (Optional) Configure the Tentative Hold time.
Step 15. Configure Session Owner and Session Setup.
Step 16. Configure an HA virtual address.
Step 17. Configure the floating IP address.
Step 18. Configure ARP Load-Sharing.
Step 19. Define HA Failover Conditions.
Step 20. Commit the configuration changes.
Verify Failover
Step 1. Suspend the active firewall.
Step 2. Verify that the passive firewall has taken over as active firewall role.
Step 3. Restore the suspended firewall to a functional state. Verify the preemption has occurred, if Preemptive is enabled.
Conclusion
In High availability (HA), two firewalls are combined together in a group and their configuration is synchronized to prevent a single point of failure in a network. A heartbeat connection between the firewall peers keeps sending keep alive signal to ensure entire failover in the event that a peer goes down. Deploy two firewalls in an HA pair provides redundancy and allows you to ensure business continuity with 99.99% uptime.
Continue Reading:
NAT Configuration & NAT Types – Palo Alto