Firewall vs NGFW vs UTM: Detailed Comparison
In today’s article we will understand the difference between traditional firewalls, Network generation firewalls (NGFW) and Unified threat management (UTM), their key features.
Firewalls sit on the boundary of the network entry point and provide protection against malicious threats originating from the public net or Internet. A traditional or simple firewall is a stateful filter security device which simply scans incoming packets and rejects or accepts data packets.
Next generation firewalls (NGFW) are advanced cousins of traditional firewalls, which not just scan data entering into the network but also provide additional features which a traditional firewall will not have. They integrate with other security features such as malware protection, intrusion prevention, URL filtering etc. due to their capability to operate at application layer.
Unified threat management (UTM) is a well-advanced security system having the capability to unify security features of a traditional firewall, instruction prevention, Anti-malware protection, content filtering and VPN – all delivered from a single platform.
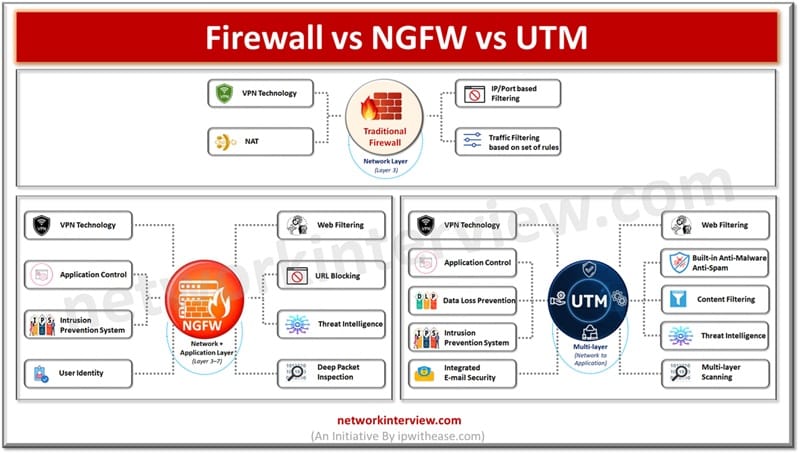
What is a Firewall
Traditional firewalls operate at layer 3 (network layer) of OSI model and provide IP address, protocol and port number-based filtering services. Firewall is a basic network security device which sits at the network perimeter and provides protection against malicious traffic trying to enter an organization network. It has a basic functionality where a set of rules on firewall determine whether traffic will be accepted, rejected or dropped.
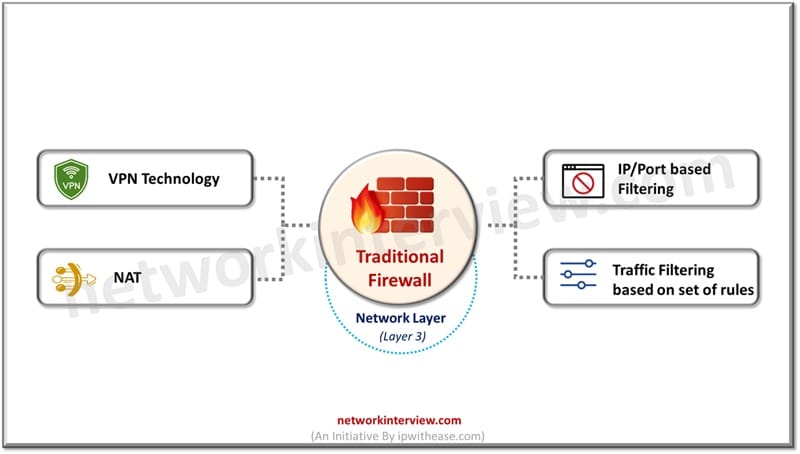
What is a NGFW
NGFW are the successor of traditional firewalls and designed to handle advanced security threats in addition to features of a traditional firewall by operating at network + application layer (layer 3-7) of OSI model. Stateful inspection and packet filtering is something it borrowed and carried forwarded along with enhanced capability to filter traffic based on applications and perform deep inspection of packets.
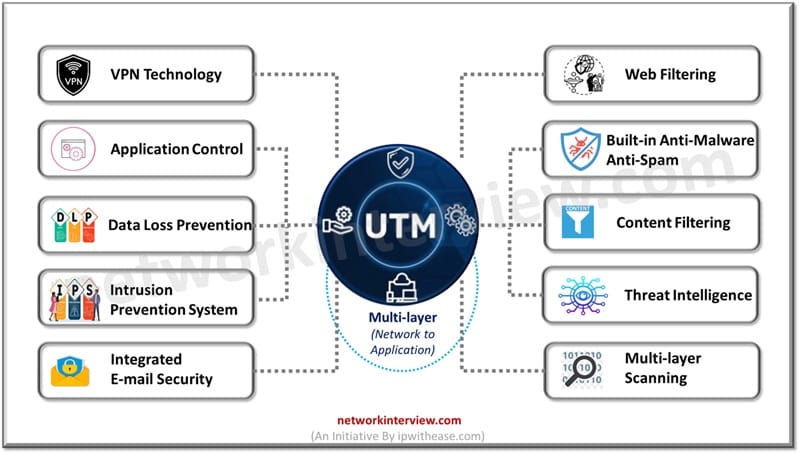
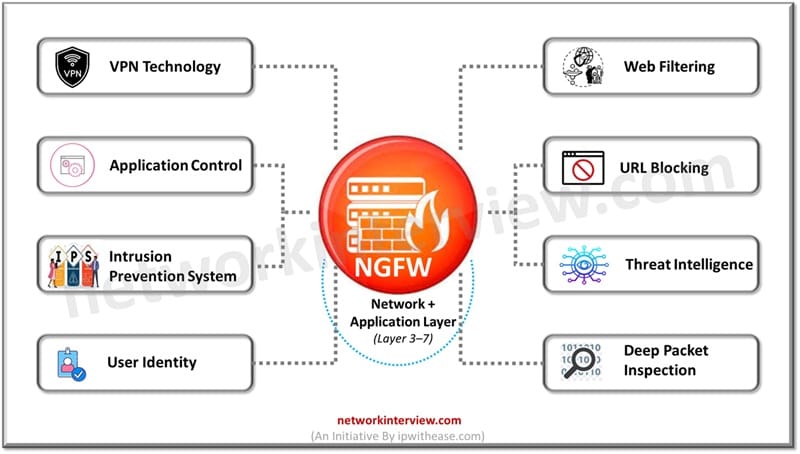
What is UTM
Unified threat management (UTM) is a comprehensive threat management solution and its need arose due to the expanding threat landscape over the years. As the severity of cyber threats increased the need was felt for a single defense system which under its umbrella manages complete network security including hardware, virtual and cloud devices and services. UTM devices are placed at key positions in the network to monitor, manage and nullify threats. UTM devices have capabilities of anti-malware, instruction detection and prevention, spam filtering, VPN and URL filtering.
Comparison: Firewall vs NGFW vs UTM
| Features | Firewall | NGFW | UTM |
| Inspection | Stateful inspection based on IP address, port and protocol | Stateful inspection with support to analyse application layer traffic | UTM as hardware appliance , software or cloud base service provides multiple security features under one platform |
| OSI layer | Operates on layer 3 (network layer) of OSI model | Operates on Network + Application layer of OSI model | Operates on Multi-layer (network to application) layer of OSI model |
| Threat intelligence | No threat intelligence filters packets based on rule set | Centralized database of threats is constantly updated | UTM uses threat intelligence feeds and databases to keep updated on latest threats |
| Packet filtering | Incoming and outgoing packets are evaluated before entering / leaving the network | Deep inspection of each packet is performed along with its source and not just the packet header in case of traditional firewalls | UTM provides basic packet filtering with other advanced security features such as Web filtering |
| Application awareness | Traditional firewalls are not aware of application as they operate at lower layers | Application specific rules can be setup as it is application aware | It is application aware security appliance |
| Intrusion prevention systems | It does not support intrusion prevention | Actively blocks and filters intrusion traffic from malicious source | Actively blocks and filters intrusion traffic from malicious source |
| Reporting | Basic reporting only | Comprehensive reporting is available | Medium capability on reporting front |
| Ideal for | Network perimeter protection and internal network segmentation | Well suited for complex and large enterprises | Ideal for small and medium business looking for a simple and comprehensive security capabilities under a single bundle |
| Examples |
|
|
|
Download the comparison table: Firewall vs NGFW vs UTM
Tag:comparison, Security



