Checkpoint Firewall Policy: Rules & Configuration
A firewall policy outlines the way an organization’s firewalls should handle the traffic that comes into and out of the specified IP addresses and address ranges, protocols, applications and content types governed by the organization’s security policies. Organizations should carry out a risk assessment to come up with a list of the types of traffic they need and how to secure them, such as which types of traffic can be allowed to pass through the firewall under certain conditions.
Checkpoint has multiple types of security policy to allow or Deny traffic from source to destination.
Types of Rules in a Firewall
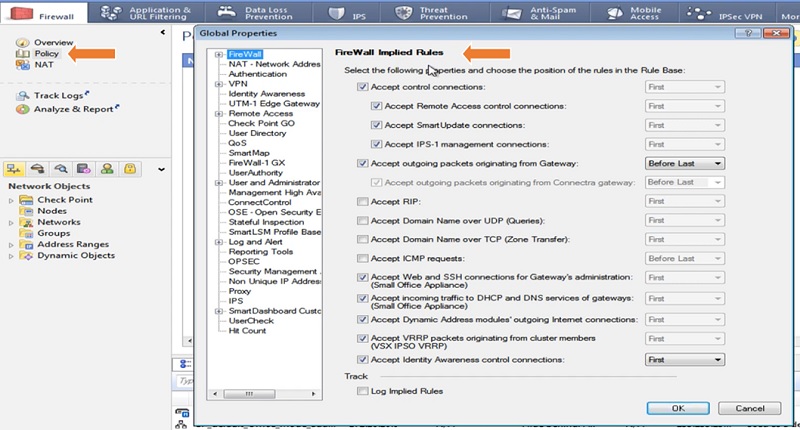
- Implicit Rules – Default rules allowed/deny by firewall. For example, any-any traffic is by default dropped by all firewalls. It’s a general behaviour of a firewall. These rules are not visible in the security policy dashboard.
- Explicit Rule – The rule which are created/configured by admin in firewall.
- Stealth Rule – It stops or denied access of any user to connect with Security Gateway
- Cleanup Rule – Rules which are created to deal with unmatched traffic.
Moreover, make sure you understand the order of the rule enforcement to maximise the security of the firewall.
The firewall always enforces the first rule that matches a connection. It cannot enforce the last rule that can be more applicable.
The Order of Policy is:
- First Implied Rule – You cannot delete or edit rule and no explicit rules can be replaced before it. Implied Rule means which are already available in firewall by-default.

- Explicit Rule – These are rules that you create
- Before Last Implied Rule – These implied Rules are applied before the last explicit rule.
- Last Explicit Rule – We recommend that you use the Cleanup rule as the last explicit rule.
Let’s discuss the best practices to create Security Policy in Checkpoint Firewall.
Checkpoint Firewall Policy: Management Rule
Management Rule means policy allows access to specific IP addresses to take SSH/HTTPs access to Checkpoint Gateway.
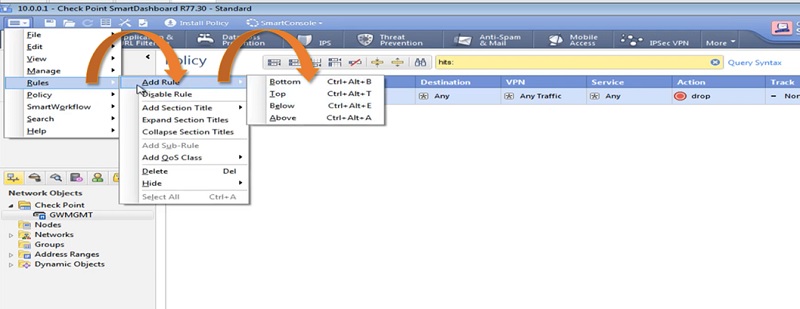
1 Go to Left Most Tab -> Select Rule -> Add Rule ->Select Top
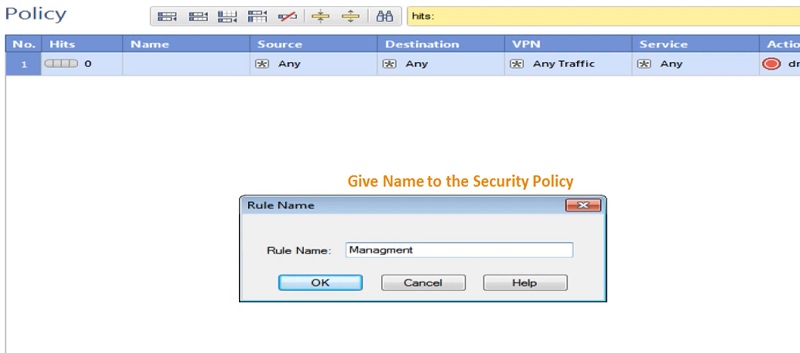
2 Give Name to the Security Policy -> Management_Rule ( As policy Created for Management Access )
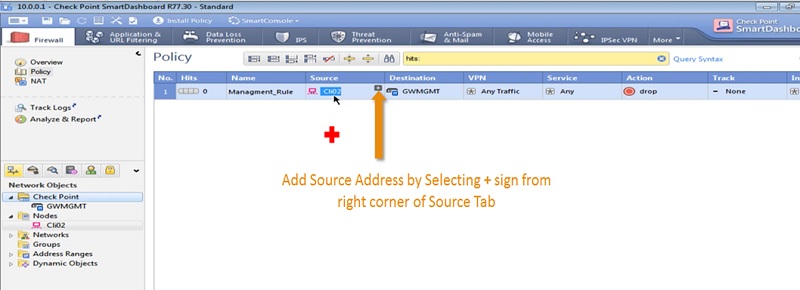
3 Now Add Source Address by Clicking + sign in Source Address Tab and similarly add Destination address in Policy.
Here, we have selected Source Address -> 10.0.0.99 (Any Client Machine)
Destination Address -> Gateway IP address of the Firewall
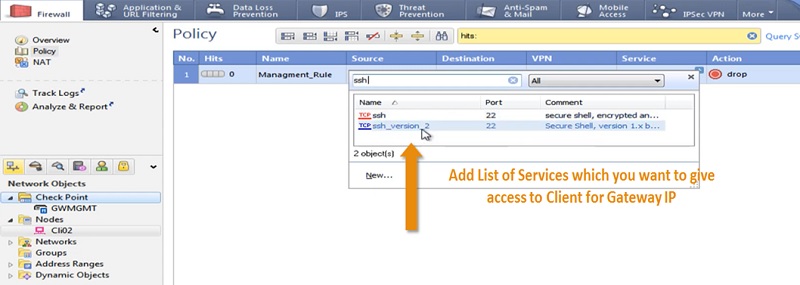
4 Add List of Services like SSH, HTTPS & HTTP in the Security Policy by clicking + sign on right most corner of the Service Tab.
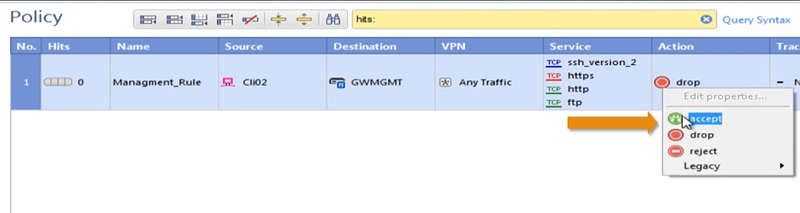
5 Add Action -> Accept from the + of Action tab
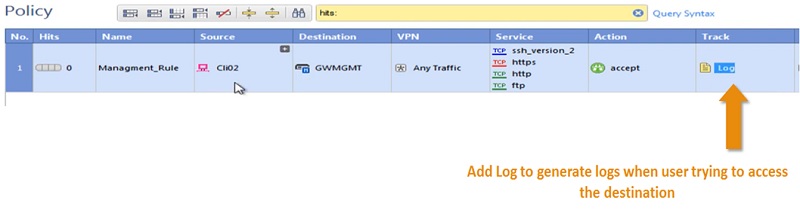
6 Add Track -> Log, every traffic generated by Client access will be logged
7 Install the Policy.
Checkpoint Firewall Policy: Deny Rule | Stealth Rule
Here we will deny access to unauthorised users for Management Gateway.
1 Add new Rule below Management_Rule
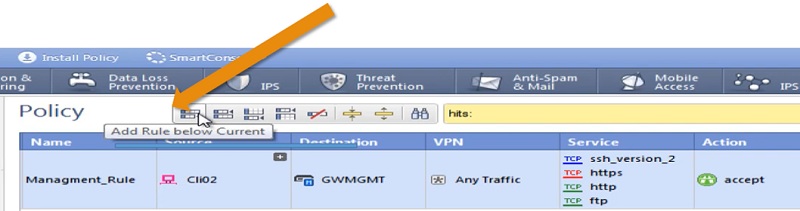
2 In this rule we will use below values to stop access to unauthorised access
Rule name -> Stealth Rule
Source Address -> Any
Destination Address -> GWMGMT
Service -> Any
Action -> Drop
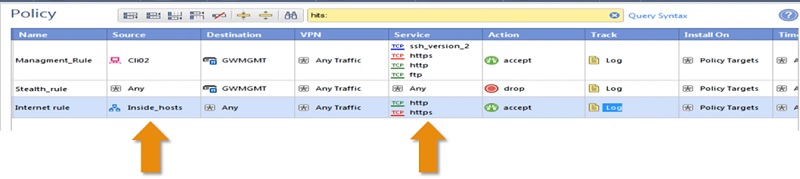
Checkpoint Firewall Policy: Internet Access
In this policy we will allow users to access Internet from Inside network
- Add Policy Name-> Internet Rule
- Add Source Address/Network -> Inside_hosts-> 192.168.1.0/24
- Destination Address -> Any (Internet)
- Service -> Internet Ports which are HTTP (port 80) and HTTPs (port 443)
- Action -> Accept
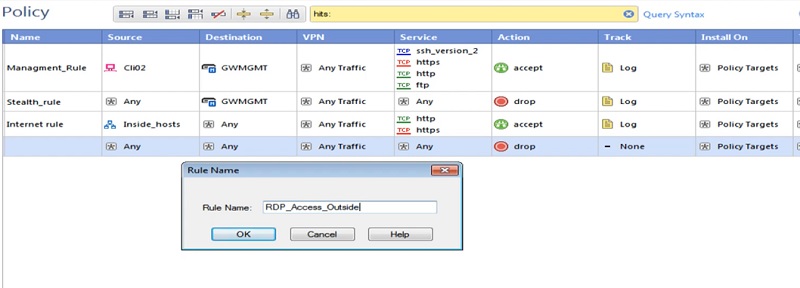
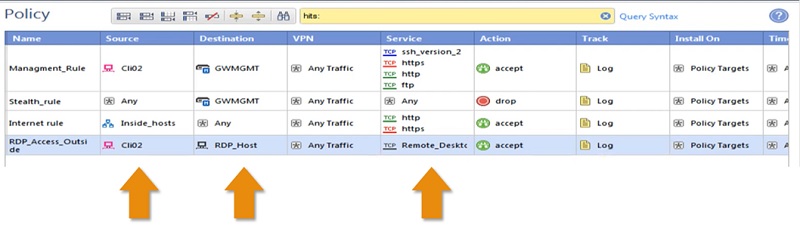
Checkpoint Firewall Policy: Allow Specific Port
Here we will allow access to specific ports.
- Source Address is any user machine-> Cli02
- Destination Address -> RDP_Host-> Server
- Service -> RDP
- Action->Accept
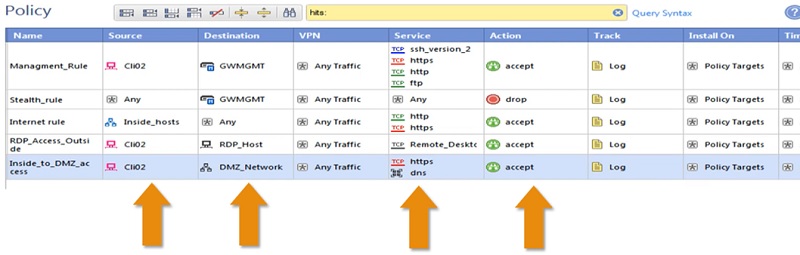
Checkpoint Firewall Policy: Inside to DMZ
To allow access from Inside network to DMZ network below policy will be used.
- Policy Name ->Inside_to_DMZ_Access
- Source -> Any source IP which needs to be access DMZ network
- Destination Address -> DMZ_Network
- Service -> DNS and Https
- Action -> Accept
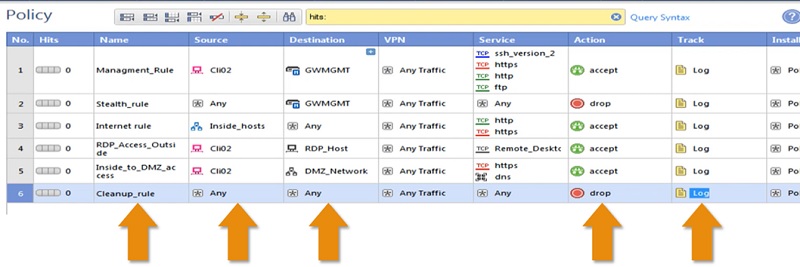
Checkpoint Firewall Policy: Cleanup Rule
Last Rule is a cleanup rule in which we deny all other traffic and apply it at the BOTTOM of all the firewall rules.
- Rule Location -> Bottom
- Rule Name -> Cleanup_Rule
- Source -> Any
- Destination -> Any
- Service -> Any
- Action -> Drop
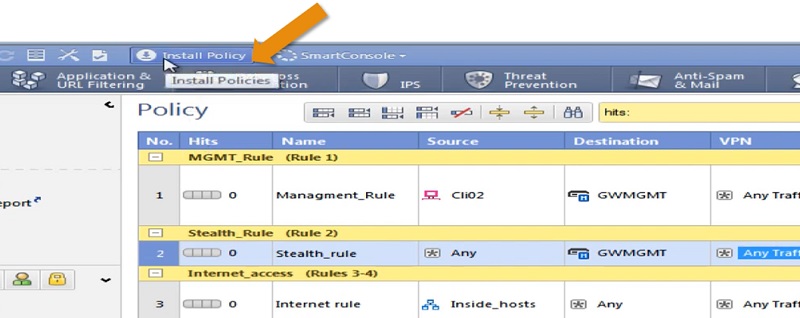
Checkpoint Firewall Policy: Install Policy
Once all rules are configured, it’s time to install policy on the Gateways.
Select -> Install Policy
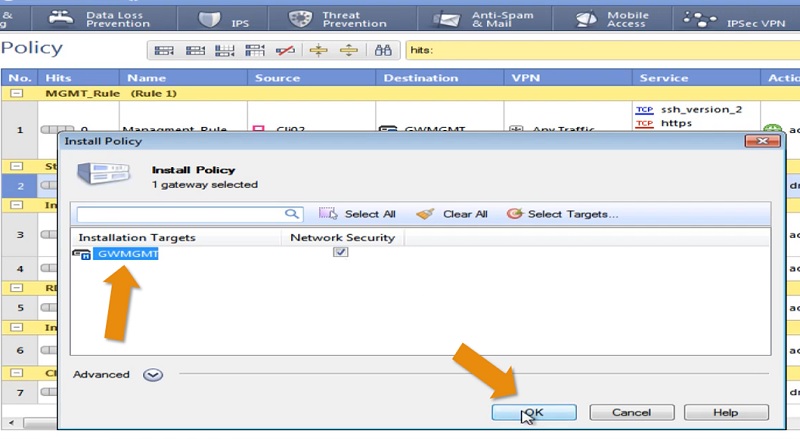
Once you select Install Policy it will prompt Gateway options
Select Firewall Gateway -> Click OK
Installation done
Continue Reading:
FortiGate Firewall Policy: Rules, Types & Configuration
Checkpoint NAT Policy: Types & Configuration
Tag:Checkpoint, Security