
10 Best Dark Web Monitoring Tools for Threat Intelligence 2025
What is Dark Web?
The dark web, a concealed part of the internet, serves as a shield for users’ online privacy against traffic analysis attacks. Accessible only through specialized dark web browsers or technologies, it remains intentionally hidden.
How is it different from the Deep Web?
It’s important to differentiate between the deep web and the dark web.
- The “Deep Web” comprises internet content that search engines don’t index due to technical reasons. Accessing resources behind login credentials constitutes the deep web, including email, social media, online banking, and messaging app accounts, as well as legal documents, scientific research, and academic databases.
- Dark Web houses content within private overlay networks that require specific software, configurations, or authorization to access. This anonymity makes it a hub for cybercriminal activity, including coordinating attacks and trading stolen data.

Significance of Dark Web Monitoring
The Dark Web holds valuable threat intelligence, revealing insights into cyberattacks, stolen data, available attack tools, and success rates. However, harnessing this intelligence requires a deep understanding of the dark web and effective investigative techniques.
Threat information available on the Dark Web includes
- exposed leaks,
- vulnerabilities for sale,
- data related to new cyber attack campaigns, and
- access to digital assets.
Dark web monitoring helps anticipate future attacks and informs pre-emptive cybersecurity measures. Due to its rich content and significance, the dark web is a vital resource for open-source intelligence (OSINT). It allows organizations and governments to detect data breaches and illegal activities, enabling them to take appropriate measures.
This article explores how data can be extracted from the dark web using OSINT techniques, analyzed, and correlated with sample tools.
Best Dark Web Monitoring Tools
1. NexVision Dark Web Threat Intel
NexVision Dark Web Threat Intel is an advanced and fully automated solution for detecting threats on the dark web. It sets a new standard in terms of coverage and uses cutting-edge technology. While many other platforms only provide basic information from the surface of websites, NexVision stands out by delving deep into sources and web servers, enabling comprehensive content exploration. Its unique strength lies in the ability to gather data from complex sources that require different types of access, such as authentication, marketplace access, or special permissions.
A significant portion of the data comes from these intricate sources, giving NexVision’s search engine unparalleled access to the complex landscape of the darknet. NexVision has the capability to archive every Tor web page and provide instant translation. It uses 144 advanced techniques to extract important metadata, including geolocation, creator information, paths, system logs, and more. NexVision offers a pioneering approach that provides access to the hidden insights of the dark web’s complexities.
Key Considerations
NexVision offers a range of cutting-edge solutions aimed at enhancing online security and intelligence.
- Their Dark Web Search Engine stands out for its ability to comprehensively scan the dark web and gather data from intricate sources that require various forms of access.
- This deep-level access is invaluable for security, intelligence, and research applications, enabling users to gain a comprehensive understanding of the dark web’s landscape, identify potential risks, and extract crucial intelligence.
- The Data Breach Engine focuses on proactively protecting individuals’ sensitive information from potential security breaches.
- It scans online sources, including the dark web and hacking forums, to detect compromised personal data such as login credentials, credit card details, email addresses, usernames, and cryptocurrency wallets.
- Credential monitoring, credit card monitoring, email monitoring, and username monitoring are key features of this module, ensuring constant surveillance and alerts when sensitive data is detected in unauthorized contexts.
- NexVision’s MarketPlace Intelligence solution meticulously monitors covert online marketplaces on the dark web, providing insights into illicit activities. It categorizes and analyzes listings, tracks interactions, and offers threat intelligence valuable for security researchers and law enforcement. The tool also helps businesses mitigate data breach risks.
- For encrypted chat content monitoring, NexVision offers specialized solutions designed to scrutinize and track communications within encrypted messaging platforms like Telegram.
- These solutions employ advanced data collection techniques, keyword detection, and anomaly detection to identify suspicious content and potential threats.
- This monitoring assists investigations and compliance efforts, equipping law enforcement agencies, security professionals, and organizations with tools to combat criminal intent or harm proactively.
2. DarkOwl VISION UI
Vision UI, developed by DarkOwl, is a specialized tool designed for scanning the Dark Web. It operates by systematically cataloguing the content of potentially malicious websites across the entirety of the World Wide Web. Its primary purpose is to meticulously search and identify any data that may have been stolen from DarkOwl’s clients.
Key Considerations
This product is primarily recommended due to its versatile array of key features:
- Its Professional Threat Intelligence capabilities empower organizations to stay ahead of evolving threats, identify vulnerabilities, and proactively fortify their cybersecurity posture.
- The product excels in Third-Party Risk Assessment, providing a robust framework for evaluating and managing risks associated with external partnerships and vendors, thereby safeguarding critical business interests.
- Cyber Security Underwriting is another crucial facet, enabling insurers to make informed decisions by comprehensively assessing cyber risks and exposures.
- Digital ID Protection ensures the security of sensitive digital identities and personal information, a critical requirement in today’s interconnected world where data breaches are rampant.
- The product offers robust Fraud Protection measures, guarding against fraudulent activities, unauthorized access, and financial losses.
- Its capacity to bolster Critical Infrastructure Security is invaluable in protecting vital systems and assets from cyber threats, and it plays an essential role in enhancing National Security by contributing to the resilience and safeguarding of key national interests.
3. DeepdarkCTI
DeepdarkCTI is a project dedicated to sourcing valuable Cyber Threat Intelligence (CTI) from the depths of the Deep and Dark Web. Its primary objective is to collect and present sources that are instrumental in enhancing cybersecurity and threat intelligence efforts.
Key Considerations
DeepdarkCTI analysts assess threats through the lens of intent, capability, and opportunity, enabling them to make strategic, operational, and tactical decisions regarding both current and emerging threats. These threat intelligence categories comprise:
- Within the DeepdarkCTI project, DeepdarkCTI concentrates on Open Source Intelligence (OSINT) sources within the Deep and Dark Web sphere.
- It systematically monitor intelligence from a variety of sources, including Telegram channels, groups, and chats, Discord channels, ransomware groups’ websites, forums related to cybercriminal activities and data breaches, underground markets, exploits databases, Twitter accounts, and Ransomware-as-a-Service (RaaS) platforms.
- It offers a comprehensive description of diverse techniques for sourcing and analyzing these data streams in our methods file, equipping analysts with the tools for effective CTI research.
4. OWASP TorBot
OWASP TorBot is a web crawling tool with various features designed to explore and collect data from websites on the Tor network, .onion domains, and custom domains. These features, once completed, will provide valuable capabilities for researchers and analysts interested in examining hidden websites and their content.
Key Considerations
- This tool enables users to crawl .onion websites, retrieve page titles, addresses, and short descriptions (partially completed), and save discovered links to a database.
- TorBot can extract email addresses from the websites it visits and store crawl information in JSON files for convenient analysis.
- It extends its crawling capabilities to custom domains, allowing users to explore websites beyond the Tor network.
- To ensure efficient web crawling, TorBot can check the availability of links, focusing on live and accessible websites.
- It comes equipped with a built-in updater, ensuring that the tool remains current with the latest features and improvements.
- A significant development in progress is the creation of a TorBot graphical user interface (GUI), which will enhance user-friendliness. While social media integration is planned (not yet initiated), it hints at the potential to integrate TorBot with social platforms for expanded functionality or data collection.
5.Lastpass
LastPass conducts ongoing monitoring of your email addresses in a database of compromised credentials. It promptly notifies you via email if any of your email addresses have been compromised, providing you with peace of mind that LastPass is safeguarding your security, even when you’re not logged in.
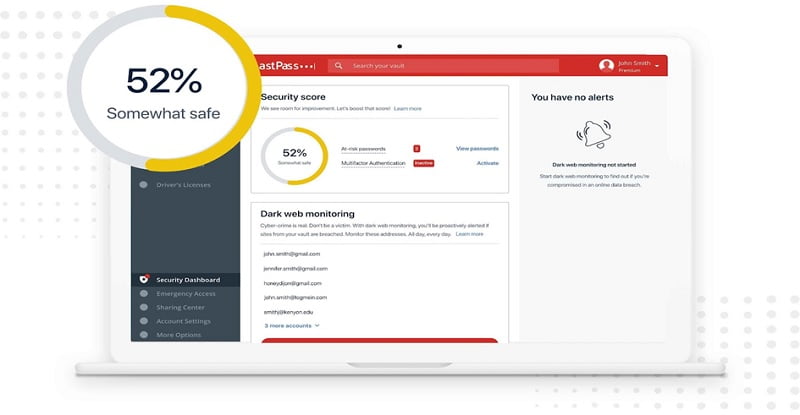
Key Considerations
- LastPass plays a critical role in addressing the risks associated with the dark web, an elusive part of the internet that eludes search engines and is known for both anonymity and criminal activities.
- LastPass aids in safeguarding your data by offering robust security measures and promoting vigilant online practices, helping you steer clear of the pitfalls of the shadowy corners of the internet.
6.Cyble Vision
Cyble Vision provides organizations with a comprehensive overview of their external threat landscape by aggregating intelligence from three key sources: the dark web, deep web, and surface web. This unified view allows businesses to understand better and manage the various threats they face in the digital realm, enhancing their overall cybersecurity posture.
By monitoring and analysing data from these different sources, Cyble Vision helps organisations proactively identify and mitigate potential risks, ultimately bolstering their security defences and safeguarding their digital assets.
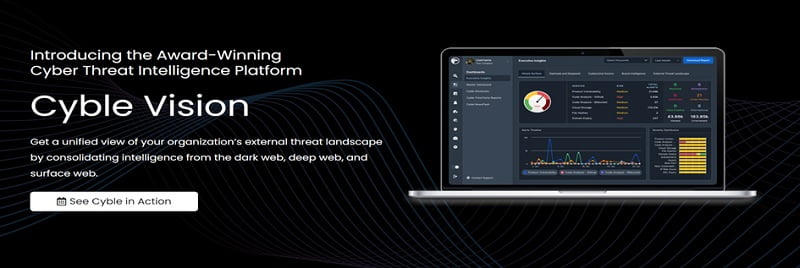
Key Considerations
- It enables swift incident response, identifying and addressing cyber threats promptly to minimize potential harm and expedite recovery.
- By integrating actionable threat intelligence into business processes, it enhances security team efficiency without impeding business operations.
- It provides real-time visibility into exploitable vulnerabilities when integrated with your vulnerability management solution.
- With Cyble Vision, you can analyze threat actor Tactics, Techniques, and Procedures (TTPs), allowing you to adapt your security infrastructure effectively.
- It helps track third-party threats and security risks, employing a security scoring mechanism for comprehensive risk management throughout your ecosystem.
7.Webz.io
Webz aids in preventing cyberattacks by offering Dark Web Data Feeds, bolstering your cybersecurity intelligence capabilities. Webz Dark Web Data API encompasses an extensive range of sources, including millions of deep, dark, and open web sites, forums, marketplaces, paste sites, and more. This comprehensive coverage empowers your cybersecurity solution to stay vigilant, monitor potential threats, and proactively defend against malicious activities originating from the depths of the internet.
Key Considerations
- Webz.io Enhance cybersecurity strategy with comprehensive coverage that extends to the deep, dark, and open web, ensuring no potential threats go unnoticed.
- Stay alert with real-time data, detecting emerging risks across various web sources.
- Enriched cyber data allows you to track the development of ransomware and malware by monitoring critical categories and entities, such as IPs, domains, keywords, crypto addresses, email addresses, and credit cards.
8.Spycloud
SpyCloud offers Dark Web monitoring services tailored for both consumers and enterprises, providing unparalleled protection against threats originating from the dark web. Their approach combines recaptured data with automated remediation, resulting in robust security measures.
By actively monitoring the dark web, SpyCloud ensures that compromised information is promptly identified and mitigated, reducing the risks associated with data breaches and cyber threats. Whether you are an individual or part of an organization, SpyCloud’s services empower you to proactively safeguard your digital identity and sensitive data from malicious actors on the dark web.
Key Considerations
- SpyCloud excels in early threat detection by accessing stolen dark web data long before other providers, offering proactive protection.
- Their data is actionable, ensuring you receive true compromise evidence, reducing false positives.
- SpyCloud goes beyond mere alerts, actively notifying users about their dark web exposures. Depending on your needs, they assist users in taking remedial actions or deploy automated remediation measures.
- This comprehensive approach empowers organizations and individuals to stay ahead of threats, mitigate risks, and safeguard their digital identities and sensitive data effectively.
9. ShadowDragon OIMonitor
ShadowDragon offers a robust suite of investigative tools tailored to streamline the complexities of modern investigations. Their product lineup comprises OIMonitor, MalNet, and SocialNet, each serving a distinct investigative purpose.
Key Considerations
- OIMonitor is a gateway to the world’s open data and excels in dark web monitoring and online investigations.
- With the capacity to collect data from a staggering 90,000 TOR sites daily, OIMonitor equips investigators to spot emerging trends and correlate potential threats, helping them maintain an edge in the ever-evolving digital landscape.
10.Have I Been Pwned
Have I Been Pwned” (HIBP) is a widely recognized online service and database created by security expert Troy Hunt. Its primary purpose is to help individuals check if their personal information, such as email addresses and passwords, has been compromised in data breaches or leaks.
Key Considerations
- Users can check if their email addresses appear in these breaches by using HIBP’s search function on its website. If a match is found, HIBP notifies the user of their compromised email address, often providing additional breach details.
- HIBP offers a password-checking feature to identify exposed or weak passwords. This service aims to raise awareness about data breaches and promote better online security practices, enabling users to secure their accounts, change passwords, and mitigate the risks associated with data breaches.
Continue Reading:
Top 10 Cyber Security Monitoring Tools



