5 DNS Attack Types and How to Prevent Them
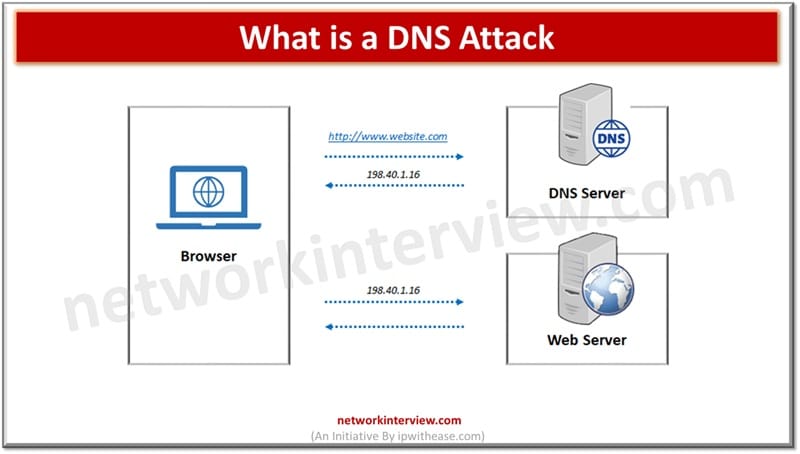
DNS (Domain name system) operates at the layer of OSI model in traditional networking. DNS is a very important protocol and backbone of the Internet, it translates human readable domain names to its corresponding numeric IP address which is used by computers worldwide to locate services and devices available. DNS usage and popularity also brought bad actors and hackers attention to it and it became a common target for attacks in cyber world.
In today’s topic we will learn about different types of DNS attacks and measures to mitigate them.
What are DNS Attacks?
DNS attacks have been on the rise for quite some time. In 2024 DNS Filter report showing phishing attacks went up to 106% and as these attacks are getting worse, enterprises and individuals need to take these DNS attacks more seriously as they lead to data loss, ransom demand, and damaged reputation. In DNS attack hackers exploit DNS weaknesses such as
- Traffic redirection to malicious websites changing DNS records
- Overwhelm DNS servers with too many requests in short span of time to cause service disruptions
- Tick users in visiting fake websites to steal credentials, passwords etc.
Types of DNS Attacks
DNS Cache Poisoning (DNS Spoofing)
Users are redirected to malicious websites by manipulating the DNS cache of the DNS resolver by the attacker. Attackers exploit vulnerabilities in DNS software or intercept DNS queries and inject false DNS records into the DNS cache database. The legitimate domain names are mapped with malicious IP addresses to redirect users to fictitious websites.
DNS spoofing leads users to unknown websites which result in phishing attacks, malware distribution or sensitive information theft. Implementation of DNSSEC (Domain name system security extensions) help in authenticating DNS data to prevent tampering. Configuring secure DNS resolver settings, regular monitoring and updated DNS cache contents, deploy intrusion detection systems to detect and block malicious spoof traffic.
DNS Amplification
DNS Amplification exploits open DNS servers which generate a large volume of traffic which is redirected to the target. Small DNS requests are sent by attackers to open DNS servers having spoofed source IP address which belong to the victim. DNS server responds with larger responses with amplified volume of traffic directed to the targeted network. Overwhelming of network bandwidth occurs in this case.
To mitigate these attacks ingress filtering is an effective option to mitigate IP address spoofing. Configuring DNS servers to put limits on query response, and traffic scrubbing solutions which filter malicious DNS traffic. Maintaining up to date DNS server configurations and monitoring of DNS traffic for anomalous patterns.
DNS Tunnelling
This technique is used by attackers to bypass network security controls using encapsulation of unauthorized data in DNS query and response. Attackers launch exploits to establish covert communication channels between external servers and victim systems, enable data exfiltration, control /command, propagation of malware which remain undetected.
Anomalous patterns are analyzed by DNS traffic monitoring. Enforce query size/response limits, intrusion detection and prevention systems implementation to detect and block suspicious traffic, DNS firewall solutions and DNS traffic inspection for any signs of tunnelling activity.
Distributed Denial of Service (DDoS) Attack
DDoS attacks overwhelm DNS servers with flooding malicious traffic making them inaccessible and disrupting DNS resolution services. Exploit vulnerabilities in DNS and abuse misconfigurations in DNS servers, botnets to generate DNS queries in high volumes which lead to service degradation leading to its unavailability.
Mitigation techniques involve deploying DDoS mitigation software to detect and mitigate volumetric attacks. Distribution of query loads using distributed DNS infrastructure absorbs DNS traffic attacks. Implement network traffic filtering in collaboration with internet service providers (ISPs) and rate limiting feature to maintain redundancy and failover for continued services availability during DNS attacks.
NXdomain Attack
NXdomain attack focus is DNS servers. Fake requests for websites which do not exist are sent by hackers to flood servers. Server time is wasted and eventually resources are overwhelmed and stopped working as people can’t access actual websites. Implementing rate limiting technologies in collaboration with internet service providers, restricting number of requests to DNS resolvers for single IP address source reduces load on servers and prevents them from getting overwhelmed.
Comparison Table
Below table summarizes the difference between the 5 types of DNS attacks:
DNS Attack Types: Comparison | |||||
Parameter | DNS Spoofing | DNS Amplification | DNS Tunneling | DDoS | NXDomain Attack |
| Definition | Attacker corrupts DNS cache or responses to redirect users to malicious sites. | Exploits open DNS resolvers to amplify traffic and overload a target. | Encodes data within DNS queries to bypass security controls. | Overwhelms a server/service with traffic from multiple sources. | Floods a DNS server with queries for non-existent domains. |
| Objective | Redirect users, steal credentials, or distribute malware. | Generate massive traffic to a target using DNS resolvers. | Evade security measures to exfiltrate or infiltrate data. | Cause service disruption or take down a website/server. | Exhaust resources and slow down DNS resolution. |
| Attack Method | Alters DNS records (cache poisoning, MITM attack). | Uses recursive DNS servers to send amplified responses to a target. | Uses covert channels via DNS queries and responses. | Uses botnets to flood a target with traffic. | Overloads the DNS server with requests for invalid domains. |
| Impact | Users unknowingly visit fake/malicious websites. | Targeted service/server goes down due to high traffic. | Used for data exfiltration, command and control (C2) communication. | Website/server becomes slow or crashes. | Reduces DNS performance and availability. |
| Detection | Check DNS cache, validate responses with DNSSEC. | Monitor for abnormal DNS response sizes and traffic spikes. | Monitor unusual DNS query patterns. | Traffic analysis and anomaly detection. | Monitor for excessive failed queries. |
| Prevention | Use DNSSEC, avoid open resolvers, implement secure DNS. | Rate limit DNS responses, use BCP38 filtering. | Restrict outbound DNS traffic, use network monitoring tools. | Deploy firewalls, rate limiting, and botnet protection. | Implement rate-limiting and response-rate limiting (RRL). |
Download the comparison table: DNS Attack Types Compared



