Securing the 3 States of Data: At Rest, In Transit, In Use
Data is the lifeline of organizations and they rely on a variety of data to run their businesses. Since data is critical to run businesses, it is important to safeguard it from unauthorized access, improper usage. Different approaches are adopted by organizations to produce data which lies in different states and on a variety of devices be it cloud, mobile devices, individual systems, IoT devices etc.
Today we look more in detail about states of data – data at Rest / still, data in transit / motion and data in Use, techniques used in protection, challenges of protecting data in different states.
The three States of Data
Data or information could reside in 3 states. Data at Rest/still, Data in transit/motion and Data in Use.
Data at Rest –
Data Rest means data is not in moving state and neither being accessed and it is either stored physically or logically somewhere. Data at Rest could be on disks, tapes, CDs/DVDs, USB drives. Could be stored physically on systems, servers, databases or on cloud such as Microsoft Azure, Google GCP, Amazon AWS cloud providers etc.
Data in Transit –
Data in motion or travelling over the network such as email, web, collaborative business applications such as Microsoft Teams, Slack, instant messaging, or any other private or public communication channels.
Data in Use –
When data is in use it means it is actively used by applications, files, folders and consumed or accessed by end users.
Securing the 3 States of Data
It is vital to protect the three states of data to ensure it does not fall into wrong hands and be misused. The most widely adopted technique to secure data is encryption. The encryption keys are not stored on the same storage where data resides. Strong key mechanisms such as AES 256 are used to secure data and make it difficult to intercept.
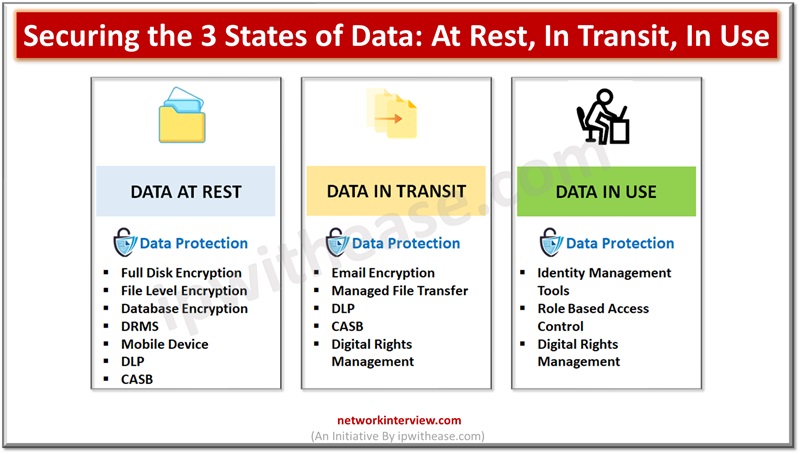
Data Protection at REST
- Full disk encryption – or hard disk encryption ensures that even if a device is lost or compromised by simply mounting the disk on another system, it does not grant access to data.
- File level encryption – Here the entire disk is not encrypted but individual files and folders are encrypted. Public key or symmetric key allows encryption of files.
- Database encryption – databases such as MS-SQL, Oracle etc. use TDE – Transparent Data Encryption for protection of data stored in tables. TDE allows data and logs encryption and decryption in real time.
- Data protection with Digital Rights Management system (DRMS) – DRMS technologies such as SealPath, Forcepoint, IBM , Netskope etc. allow documentation encryption with persistent protection. The documentation is only accessible to users having access right to it and it is stored in encrypted form.
- Mobile device management – MDM applications allow blocking of access to device or encrypt data on mobile devices largely used by large corporations.
- Data leakage prevention (DLP) – block data access to certain users in the event of violation of data policy and store data in encrypted form.
- Cloud Access Security broker (CASB) – Applications allow applying security policies in cloud systems such as office 365, box, etc. it is a cloud based DLP solution as such.
Related: CASB vs SASE: Which One Is Better?
Challenges of data protection at REST
- Data stored on diverse types of media
- Data stored / scattered across mobile devices
- In cloud encryption keys are owned by provider for storage
- Need to comply with different data protection regulations
Data Protection in Transit
There are different technologies to protect data in transit.
- Email encryption – end to end protection of email messages, attachments.
- Managed file transfer (MFT) – This is an alternative to FTP where a file is uploaded on a platform and a link gets created to have it downloaded. You can set expiry date for the link , password to access etc.
- Data leakage prevention (DLP) – DLP technologies also provide protection of data in transit and not just data at Rest. USB data copy etc. policies can be implemented.
- Cloud Access Security Broker (CASB) – CASB can detect if a user tries to upload sensitive data and does not comply with security policy related to data security.
- Digital Rights management (DRM) – In transit protection is provided by DRM such as restricting email forwarding etc.
Challenges of data protection at TRANSIT
- Infinite means of communication
- Infinite cloud applications
- Not possible to maintain control at receiving end
Data Protection in Use
To protect data in use, the majority of controls are put before content access.
- Identity management tools – checks that the user trying to access data is a legitimate user.
- Role based Access control (RBAC) – access to data is controlled based on user role, location, IP etc
- Digital Rights Management (DRM) – Set digital rights control to view, download, print data or information.
Challenges of data protection at USE
- Most of the tools control access to data before allowing access
Continue Reading:
4 Types of Data: Nominal, Ordinal, Discrete, Continuous
What Is Data Masking? Types & 8 Techniques
Tag:Security



