How to Configure Cisco FTD High Availability (HA)?
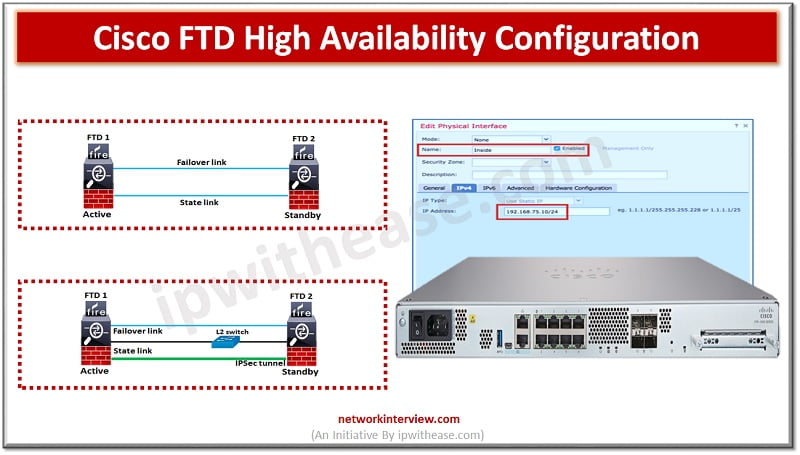
To ensure uptime and continuous availability in the event of disaster is a required key feature for any production environments be it servers, networks and other computing equipment. All Cisco devices majority support high availability (HA) also known as failover. FTD devices support active/standby failover where one unit is active and passes traffic. The standby unit does not actively pass traffic but synchronizes configuration and other state information from the active unit. When an active unit fails, the standby unit takes over.
In today’s blog we will cover in detail about the Cisco FTD high availability feature, how it works and its architecture and configuration.
Cisco FTD High Availability
Cisco FTD high availability configuration has some basic requirements to be met before they can be configured for failover as under.
- Be it same model
- Have the same number and type of interfaces
- Have to be in same firewall mode (routed or transparent)
- Have same version of software
- Be in same domain or group on FMC (FirePower management console)
- Have same NTP configuration
- Fully deployed on FMC with no uncommitted changes
- Not have DHCP or PPPoE configuration on any of the interfaces
- FTD devices in HA must have same license
- HA configuration requires two smart license entitlements one for each device in the pair
- FTD supports active standby mode
- Latency must be less than 10ms, no more than 250ms
- HA is only supported for 2 FTD devices
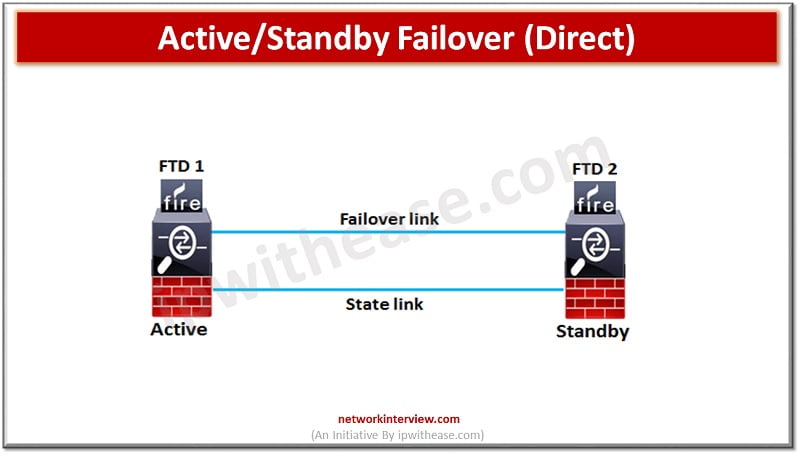
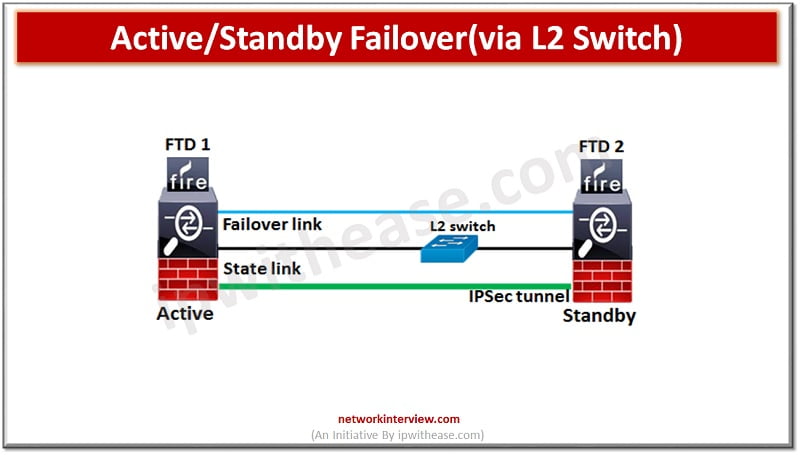
Failover link can be connected using a switch to a dedicated network segment (VLAN or broadcast domain) or could be direct connection between the two devices with the same Ethernet speed and Ethernet number.
Configure High Availability in FTD
To configure FTD for high availability both devices required to be added to the FirePower management console (FMC) manually one by one. Verify version details etc.
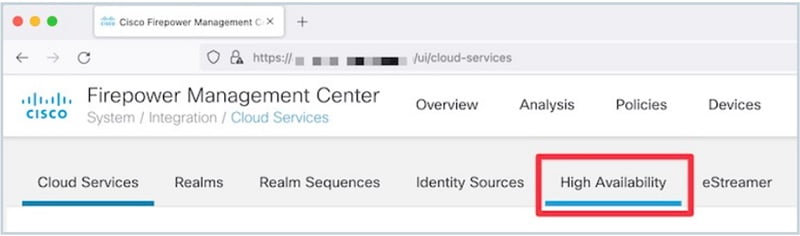
In FirePower management console to configure High availability navigate to Devices-> Device management -> Add -> Add high availability
Enter details as below:
Name: FTD-HA
Device type: FirePower Threat defence
Primary peer: FTDv1
Secondary peer: FTDv2
Click to ‘Proceed’
Enter HA and ‘state link’ details as under (IPsec encryption is optional between HA and state links). Over state link, connection state information like session table and NAT table are synchronized, so that if a failover occurs, existing connections will not be disrupted. The active unit uses the state link to pass connection state information to the standby device.
High availability link
Interface: Ga0/4
Logical name: HA-link
Primary IP: 172.16.31.1
Secondary IP: 172.16.32.2
Subnet Mask: 255.255.255.252
State link
Interface: Ga0/5
Logical name: State-link
Primary IP: 172.16.31.5
Secondary IP: 172.16.31.5
Subnet Mask: 255.255.255.252
Click ‘ok’ to submit and wait for few minutes for HA pair to get deployed.
The HA setup is complete and FTDv1 is primary (active) and FTDv2 is secondary (standby).
Continue Reading:
Fortinet FortiGate HA (High Availability): Detailed Guide
Checkpoint HA Active/Standby and Load Sharing in ClusterXL



