URL Filtering vs Content Filtering
In this post, we shall discuss about comparison of URL filtering and Content filtering. Both the terms are interrelated, however differ in flavor of how they protect and assets they protect. SO, lets understand them in more detail –
URL Filtering :
URL filtering limits access to specific URLs by comparing address of sites that users are attempting to visit against a database of either permitted or blocked sites. The purpose of URL filtering is to prevent employees from accessing sites that may interfere with the operation of the business – such as sites not related to work, sites with objectionable or illegal content, or sites associated with phishing attempts.
While unfettered web access is useful for employees and can make them more productive, it can also expose organizations to a wide range of security risks, such as propagation of threats, data loss or seizure, or legal issues.
How URL Filtering works?
URL filtering matches all web traffic against a defined database, and then permits or denies access to a site based on whether it is found in the database. A URL filtering database will assign cataloged websites a URL category, or group. It will also define the conditions of access to that URL. For example, an address could be:
- Blocked: Defined on a site by site basis. This can apply to distracting sites, like social media or local news, or sites known to host various forms of malware.
- Allowed: SaaS websites, relevant to the organization and its workflow.
- Attached to defined IT policies: Visits to a particular website could be logged and organized, so that IT can see who visits certain sites, and at what time.
- Blocked or allowed URL categories: When actions are determined not on a site-by-site basis, but rather by the category encompassing multiple sites. This could include categories for malware or phishing sites, innocent but distracting sites, or questionable sites.
The databases used by URL filters can be stored on premises, live in the cloud, or both, depending on the needs of the system. Local lookups will help reduce latency between the user and the filter, if sites are frequently visited.
A cloud database, on the other hand, can be relied upon to maintain an up-to-date catalog of all known sites.
In a hybrid solution, devices can adapt to unique traffic patterns, and use known users’ traffic to store more recently accessed URLs in an on-device cache, reducing latency. When needed, a master database stored in the cloud can be queried when the site isn’t found in the local cache.
Ideally, sites are classified automatically. URL filtering systems can use machine learning and other techniques to correctly categorize sites, or flag sites for manual categorization if necessary. Algorithms can also help URL filtering systems classify related sites automatically – for example, sites on the same domain or related domains, or sites with similar content in different languages.
Content Filtering:
Content filtering is the use of a program to screen and/or exclude access to web pages or email deemed objectionable. Content filtering is used by corporations as part of their firewalls, and also by home computer owners. Content filtering works by specifying content patterns – such as text strings or objects within images – that, if matched, indicate undesirable content that is to be screened out. A content filter will then block access to this content.
Content filters are often part of Internet firewalls, but can be implemented as either hardware or software. In such usage, content filtering is serving a security purpose – but content filtering is also used to implement company policies related to information system usage. For example, it’s common to filter social-networking sites unrelated to work.
Objectionable, inappropriate, or illegal content creates risk for organizations. For example:
- Allowing pornographic content into the workplace can put a company at risk for sexual harassment claims, or otherwise create a hostile or demeaning work environment.
- Spam sites can lead to malware or other malicious software being installed onto work computers.
- Hate sites or sites with violent content can compromise employee safety and also reflect poorly on the company as a whole.
- Social networking sites can reduce productivity and distract employees from routine tasks.
Content filtering helps to mitigate these risks by making such content difficult to access in the workplace, and by demonstrating the company’s intolerance for inappropriate, illegal, or objectionable content in general.
To be effective, content filtering has to be deployed across all content channels. The most common channels include:
- Web: The screening of Web sites or pages, as well bookmarks and other web traffic.
- Email: Screening of email for a variety of spam, malware and other undesired or malicious content. This is usually done by scanning the subject line of the emails forwarded through the filtering system. When a message is received that fills the relevant criteria, the message will be placed in the recipient’s junk folder. In some cases, it will even be sent back to the sender as undeliverable.
- Executables: The screening of executable files that may install malicious software without warning.
The motive is often to stop access to content that the user or administrator might determine is objectionable. Some of the restrictions can be applied at all levels: a national government can attempt to apply them nationwide, or an ISP can apply the filtering to its clients, even an employer to its personnel or a school to the student-body. There are no limitations to the scope of email filtering, and it can often be a strong step towards providing security to any and all users accessing the web.
Difference between URL Filtering and Content Filtering:
The two are complementary. Together, URL blocking and content filtering offer a more complete Internet access control solution for the customer. The majority of undesirable traffic is killed quickly and efficiently by URL blocking on the outbound path. The rest is caught on the return path. The customer also has the flexibility to allow access to a site but selectively block certain content from that site.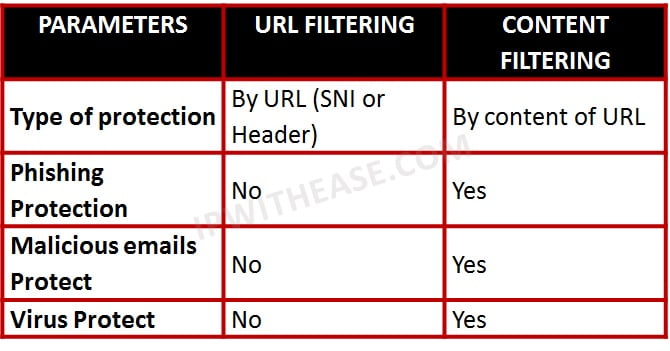
Continue Reading:
Tag:comparison



