A Definitive Guide to SHA-256 (Secure Hash Algorithms)
Hashing and encryption are one of the key mechanisms to secure data. A variety of algorithms exist in the cyber world to secure data with different key lengths – 64-bit, 128-bit, 256 bit and so on. However, the secure hash algorithm with digest size of 256 bits or SHA-256 is one of the most popular and widely used algorithms in real world applications for data security.
Today we look more in detail about Secure hash algorithm – SHA-256, how it works, what its features and use cases are.
What is Hashing?
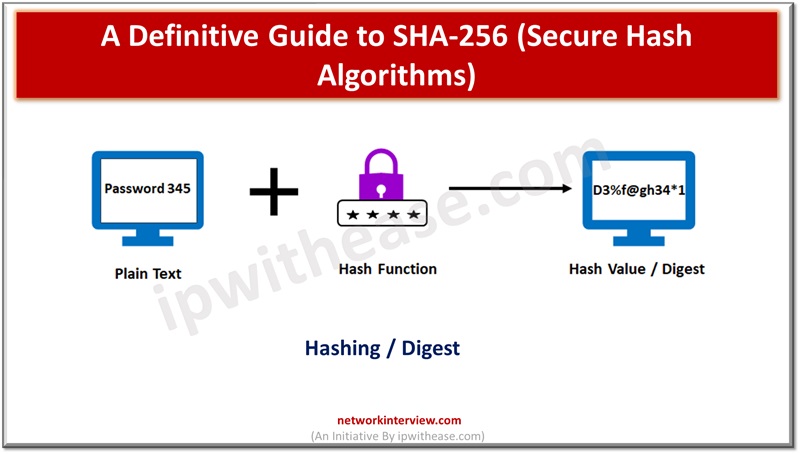
Hashing is a technique to scrambling raw data to the extent that it becomes impossible to reproduce it in its original form. It takes a piece of information which goes through a function which performs mathematical operations on the plaintext. This function is referred to as ‘Hashing’ and its output is termed as ‘digest or value’.
The hash function is responsible for conversion of plaintext into respective hash digest. Hash functions provide the same output value if input is not changed, irrespective of the number of iterations it is undergone.
Hashing Functions
Hashing provides two functions:
- Password hashes – converts user password into hash value before being stored on a web server. Hash value re-calculation occurs to match it with stored value.
- Integrity verification – when a file is uploaded on a website, it shares its hash value as a bundle. When a user downloads a file it recalculates hash and compares it with established data integrity.
Secure Hash Algorithms (SHA-256)
SHA 256 is part of the SHA2 algorithm family published in the year 2001. It was a joint effort between NSA and NIST to introduce SHA successor to SHA 1 which was losing its battle with brute force attacks. The hash value will always be 256-bit. Let’s look in detail at its characteristics.
Characteristics:
- Message length – Cleartext length should be less than 264 bits. The size needs to be in the compression area to make the digest as random as possible.
- Digest length – hash digest should be 256 bits in SHA-2 and 512 in SHA-512. Bigger digest means more calculations at the cost of speed and space.
- Irreversibility – All SHA functions are irreversible as per their design characteristic. You will never get plaintext before having digest in hand nor will digest provide its original value while passing through the hash function again.
Process: Secure Hash Algorithms (SHA-256)
Let’s look at different steps in the process of Secure Hash Algorithms (SHA-256).
Padding bits – some extra bits are added to the message, the length is exactly 64 bits short of multiple of 512. During the addition of extra bits, the first bit should be one and rest bits can be zero.
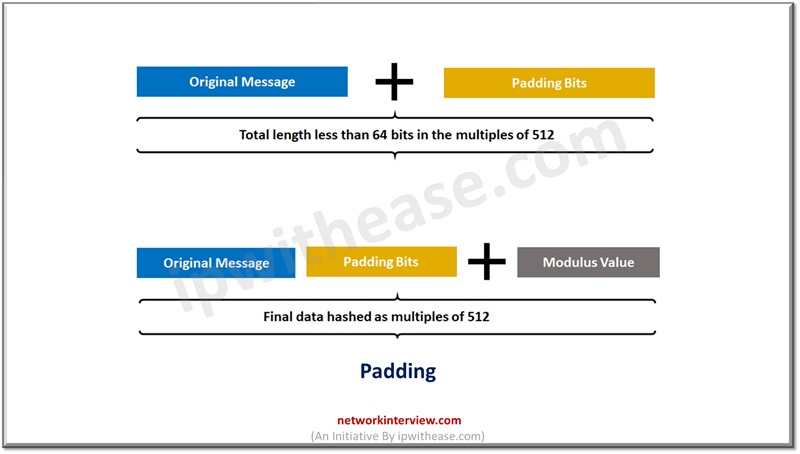
Padding length – Adding 64 bits of data to make the final plaintext multiple of 512. Calculate these 64 bits of characters by applying modulus to the initial plaintext without padding.
Initialization of buffer – Initialize the default value for eight buffers to be used in rounds. You also need to store 64 different keys in an array.
Compression function – the complete message is broken down into multiple blocks of 512 bits. It puts each block via 64 rounds of operation, with output of each block serving as input to the next block.
Output – with every iteration, the output of a block serves as input to the next block. This entire cycle keeps repeating itself until you reach the last 512-bit block and its output is considered the final hash value / digest. The length of this digest would be SHA-256.
SHA-256 Applications
- Digital signature verification – Digital signatures use asymmetric encryption to validate document / files authenticity. Hash algorithm SHA-256 ensures signatures authenticity in the most secure manner.
- Password hashing – websites store user passwords in hashed format and most of the websites use SHA-256 as the most secure way to protect user identity and privacy.
- SSL handshake – The SSL handshakes use encryption and hashing authentication to prepare a secure connection
- Integrity checking – Verification of file integrity helps to maintain full value functionality of the stored files and ensures that they are not altered or tampered during transit.
Continue Reading:
Static Hashing vs Dynamic Hashing
8 Common Web Application Vulnerabilities



