How to Prevent Against MFA Fatigue Attacks?
Leaked or stolen credentials are primary sources being used by cybercriminals in breach networks and steel company confidential and sensitive data. Normal authentication involving a username and password is an old technique and no longer provides protection against sophisticated attacks adopted by cyber criminals. Multi Factor authentication combined with password is considered to be a highly secure mechanism to prevent credential compromise by enterprises.
In today’s topic we will learn about MFA fatigue technique, how multi-factor fatigue attack works and how to defend against MFA fatigue attacks?
What is MFA?
Before we deep dive into MFA fatigue attack lets understand the basics of MFA and why it is used? MFA or multifactor authentication is a technique which provides more than one layer of authentication based on something the user knows (password), something the user is (biometric) and something the user has (authentication code, token etc.).
The authentication method used in multifactor authentication is independent and creates layers of defense to make it difficult for hackers to breach into the enterprise network even if one of the factors gets compromised. MFA uses user name and initial password which is followed by a second authentication factor which is usually an auth token which is valid for a few seconds only making it difficult for hackers to generate code at the right time. MFA provides several benefits by reducing risk of compromise.
Related: Types of Hackers
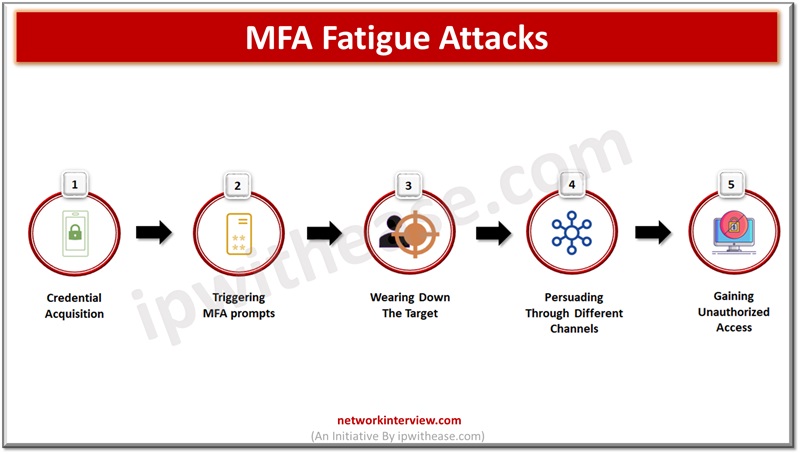
What is MFA fatigue?
MFA fatigue happens when an attacker makes repeated attempts of authentication requests until the target is fatigued or confused. When a user tries to login multi factor push a notification prompt appears, these notifications are generally used to verify if login attempt is legit, it also shows location of the login and devices used etc.
An attacker can misuse push notification feature by running a script which sends multiple push MFA login prompts on account owner phone or authentication device in a short span of time to eventually confuse the user.
The aim is to bombard the target with multiple MFA requests which inflicts a sense of fatigue in the target. In many such cases hackers might attempt to contact the user via email, SMS, or any other messaging platform and try to trick the user to accept the MFA prompt.
User is frustrated with so many requests flooding in and clicks the approve button to stop flow of MFA requests it gives full access to the attacker. Such techniques are used by ransomware gangs Lapsus$ and Yanluowang to breach multiple top organizations such as Microsoft, Uber, etc.
How to Prevent MFA fatigue Attacks?
There are several ways for prevention of MFA fatigue. Let’s learn about them more in detail.
FIDO Authentication
This is considered one of the most secure ways to authenticate keeping user and device in proximity and prevents man-in-the-middle and Modlishka attacks. FIDO enables usernameless and passwordless experience. Adoption for FIDO however could be slow because it means to equip every user in the organization with a FIDO authenticator which requires a computer with platform biometrics like Windows Hello or Mac TouchID. Another option is to provide every user a security key.
Limit number of Push Notifications
Putting a limit on the number of push notifications in a short span of time can reduce the chance of human error. Even trained users approve a push notification if it is sent multiple times so putting a limit on push notification can help here.
Using Push Notification with Number Selection
This method uses push notification but users need to input a two-digit number appearing on their device and ask the user to choose from a list of three numbers presented on mobile application. If the user inputs the right number then only an authentication request is approved.
This method is more secure than just sending the push notification alone.
Risk Based Authenticator (RBA)
The RBA also looks at other aspects before approving authentication requests such as is user logging from the same device always used by them, which application user is accessing, what is the location of user or device?
RBA learns user patterns, devices in use, location, network etc and provides simple to digest risk scores. MFA policy uses this score to decide to approve/challenge/reject authentication requests.
Continue Reading:
8 Common Web Application Vulnerabilities
IP Address Restrictions for Improved Access Control
Tag:Security



