How To Configure Juniper SRX Security Policy?
To secure networks network administrators create security policies for network resources within the business required to establish security level for network resources. All standard firewalls allow creation or setting up baseline and advanced security policies to enforce rules for transit of traffic, what traffic shall pass through the firewall, and define actions as policies which need to take place as traffic passes through the network firewall.
Today we look more in detail about how to configure Juniper SRX security policy, understand security policy elements, rules etc.
Juniper SRX Security Policy Elements
A security policy is nothing but a set of statements to control traffic flowing from one specific source to a specific destination while using a specific service. Policies permit, deny, or perform tunnelling specific traffic type in between two points unidirectionally.
Each policy comprises of :
- Unique name to policy
- From-zone to to-zone such as user@myhost#set policies from-zone untrust to-zone untrust
- Matching criteria to define conditions which must be met to apply the rule which could be based on IP address source or destination, and applications.
- Set of actions to be performed based on match status – permit , deny or reject
- Accounting and auditing such as count, logs, and system logging in structured way
Juniper SRX Security Policy Rules
Security policies apply security rules to transit traffic and each policy is uniquely identified. Each policy has a set of characteristics:
- Source zone
- Destination zone
- One-many source address name or address name sets
- One-many destination address name or address name sets
- One-many application names or application name sets
The rule characteristics are match criteria. Every policy has an action linked with it: permit, deny, reject, count, log, and VPN tunnel. Using wildcards policy can be configured with IPv4 or IPv6 addresses. When flow support is not enabled then all matches happen with IPv4. Flow based forwarding based on IPv6 is enabled using set security forwarding-options family inet6 mode flow-based command.
With IPv6 traffic enablement, the maximum number of IPv4 and IPv6 addresses which are configurable in security policy is based on match criteria. IPv6 requires four times more memory space than IPv4.
Number_of_src_IPv4_addresses + number_of_src_IPv6_addresses * 4 <1024
Number_of_dst_IPv4_addresses + number_of_dst_IPv6_addresses * 4 <1024
Security Policy Configuration
To create a security policy following steps are required we will use a scenario to define steps to configure security policy on firewall
P1: allow http
P2: allow telnet
P3: allow icmp
P4: explicit deny-all ; log and count
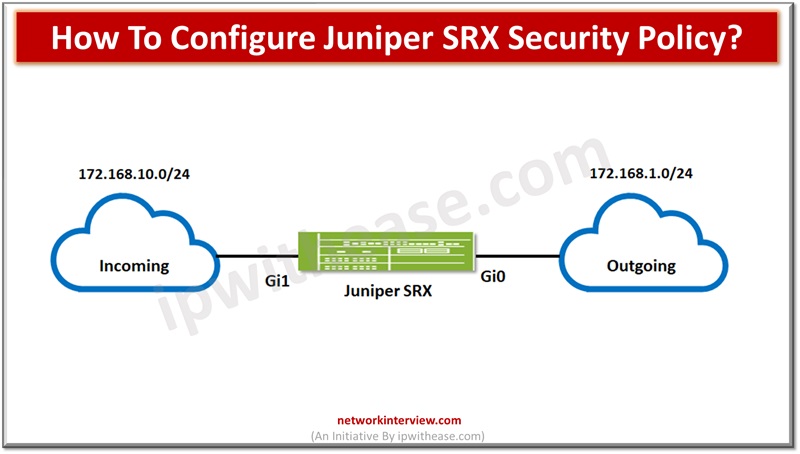
Juniper SRX is connected with IP subnet 172.168.1.0 to outgoing zone through G0 Ethernet and connected to incoming zone with G1 Ethernet and IP subnet 172.168.10.0
Policies are configured from incoming-zone to outgoing-zone
[edit]
FW1# show | compare
[edit security policies]
from-zone outgoing to-zone junos_fw-host { … }
from-zone incoming to-zone outgoing {
policy ALLOW-WEB {
match {
source-address NET_172_168_10_0__24;
destination-address any;
application junos_fw-http;
}
then {
permit;
log {
session-init;
session-close;
}
count;
}
}
policy ALLOW-TELNET {
match {
source-address NET_172_168_10_0__24;
destination-address any;
application junos_fw-telnet;
}
then {
permit;
log {
session-init;
session-close;
}
count;
}
}
policy ALLOW-ICMP {
match {
source-address NET_172_168_10_0__24;
destination-address any;
application junos_fw-icmp-all;
}
then {
permit;
log {
session-init;
}
count;
}
}
policy DENY-ALL {
match {
source-address any;
destination-address any;
!
P1: allow http
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB match source-address NET_172_168_10_0__24
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB match destination-address any
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB match application junos-http
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB then ALLOW
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB then log session-init
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB then log session-close
set security policies from-zone incoming to-zone outgoing policy ALLOW-WEB then count
!
P2: allow telnet
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET match source-address NET_172_168_10_0__24
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET match destination-address any
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET match application junos-telnet
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET then permit
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET then log session-init
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET then log session-close
set security policies from-zone incoming to-zone outgoing policy ALLOW-TELNET then count
!
P3: allow icmp
set security policies from-zone incoming to-zone outgoing policy ALLOW-ICMP match source-address NET_192_168_10_0__24
set security policies from-zone incoming to-zone outgoing policy ALLOW-ICMP match destination-address any
set security policies from-zone incoming to-zone outgoing policy ALLOW-ICMP match application junos-icmp-all
set security policies from-zone incoming to-zone outgoing policy ALLOW-ICMP then permit
set security policies from-zone incoming to-zone outgoing policy ALLOW-ICMP then log session-init
set security policies from-zone incoming to-zone outgoing policy ALLOW-ICMP then count
!
P4: explicit deny-all ; log and count
set security policies from-zone incoming to-zone outgoing policy DENY-ALL match source-address any
set security policies from-zone incoming to-zone outgoing policy DENY-ALL match destination-address any
set security policies from-zone incoming to-zone outgoing policy DENY-ALL match application any
set security policies from-zone incoming to-zone outgoing policy DENY-ALL then reject
set security policies from-zone incoming to-zone outgoing policy DENY-ALL then log session-init
set security policies from-zone incoming to-zone outgoing policy DENY-ALL then count
set security policies pre-id-default-policy then log session-close
Continue Reading:
Palo Alto Security Profiles and Security Policies
Checkpoint Firewall Policy: Rules & Configuration
Tag:Juniper SRX



