Agent based vs Agentless Micro segmentation
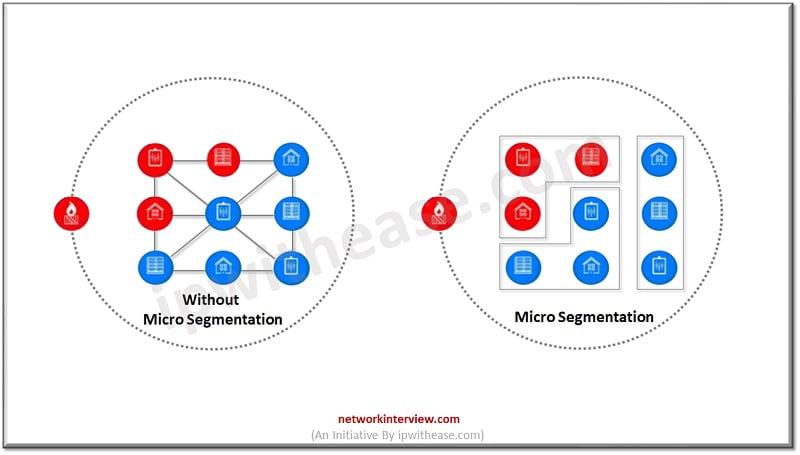
Granular level management of access and security controls is the focus of security techniques deployed nowadays as attacks have become more and more sophisticated so is the dynamics of protection also getting changed frequently. Virtually restricted access to any device across endpoints and applications irrespective of VLAN they reside on is all about Micro Segmentation technique. Micro segmentation approach lets Cyber protection approach into proximity of each application or service request hence helps to put a precise level of access control.
Today we look more in detail about two Micro Segmentation techniques – agentless and agent based, how they differ from each other, their advantages and limitations and which technique is best suited in what kind of scenario and so on.
What is Agentless Micro segmentation?
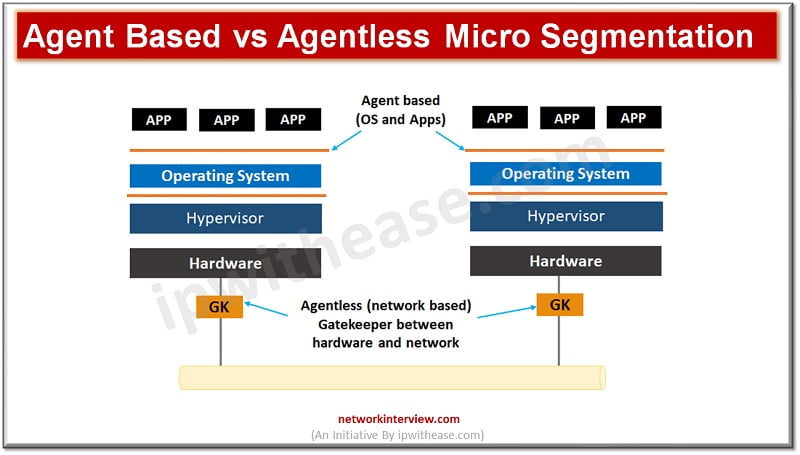
Micro segmentation lets manage network access between workloads based on the principle of least privileges and zero trust. It helps to limit the effect of malicious lateral movement. Agentless Micro Segmentation also referred to as “gatekeeper’ approach which deploys an appliance inline with workloads to be protected. It can work with any typical workload. Third party APIs , span ports and NetFlow etc. collect and control the traffic which can be used to set security policies.
What is Agent based Micro segmentation?
Agent based solutions use software agents on endpoints. The agents monitor and analyze traffic which flows in and out of the host to identify suitable granular policies and offer application visibility. The agent-based generally leverages Windows Filtering platform (WFP) to enable either a firewall which is built into the operating system itself or the proprietary firewall bundled with agent software.
The WFP filters traffic on OSI layer 3 and layer 4 and processing of data collected from WFP is used to make policy decisions. Use of lightweight agent with additional capabilities such as file integrity monitoring (FIM), deception capabilities, endpoint detection and response (EDR) capabilities are also offered as bundled.
Advantages of Micro segmentation
- Reduction in attack surface by integration of security policy definition early into the application development lifecycle to ensure application updates and deployments do not create new attack vectors.
- Containment of breaches by providing ability to monitor network traffic against predefined policies and reduction in time to respond to breaches
- Regulatory compliance adherence – can create policies to isolate systems subjected to regulations apart from existing infrastructure
- Simplification of policy management – perform automated discovery of applications and policy suggestions based on application behaviour
Use cases for Micro segmentation
- Segregation of development and test environments and more disciplined separation enablement with granular enforcement to limit connections between the two
- Soft assets such as confidential customer data, employee details, financial data, intellectual property to be protected from malicious action
- Seamless protection in hybrid cloud environments where applications might span across multiple clouds
- Limit lateral movement of attack and log information to help in analysing attack tactics and identify policy violations quickly
Agent based vs Agentless Micro segmentation
Below is a tabular comparison of these two different approaches to implementing network security within a micro segmentation framework:
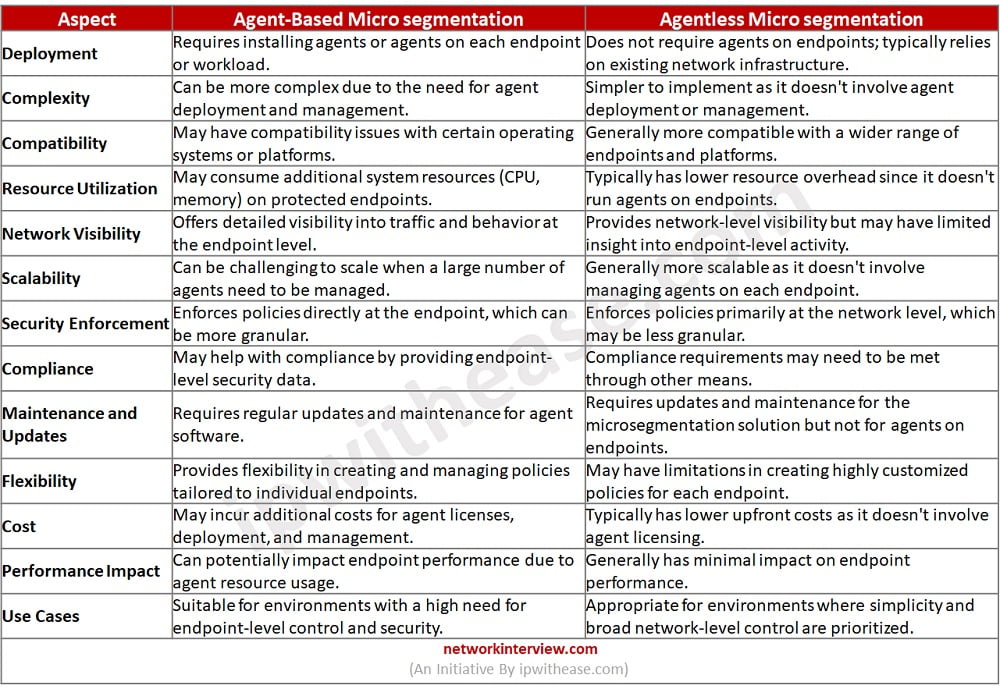
Download the comparison table: Agent based vs Agentless Micro segmentation
Conclusion
Micro segmentation has allowed organizations to better govern network access between resources having unique identification of each resource such as server, application, host , user etc. permissions can be configured which gives fine grained control over data traffic. It enables lateral movement prevention of threats, workload compromise, and data breaches.
The choice between agent-based and agentless micro segmentation depends on the specific requirements, constraints, and priorities of your organization, as well as the existing infrastructure and the level of control and visibility you need over your network.
Continue Reading:
Micro segmentation vs Network Segmentation
Microsegmentation vs Zero Trust
Tag:comparison, Security



