What is a Remote Access Trojan (RAT)?
Remote access and control over systems remotely is widely used to provide technical support to users or work outside the boundaries of offices. With the rise of remote working however, especially during Covid-19 pandemic had allowed attackers to use remote access and control for nefarious purposes. There are several types of malware which exist in the cyber world such as trojans which are considered dangerous and used to gain access and control over systems.
In today’s topic we will learn about Remote access trojan (RAT), how remote access trojan works, how to detect a remote access trojan, how to protect against remote access trojans.
Remote Access Trojan (RAT)
The word Trojan finds reference in the mythological Trojan horse used to conquer the city of Troy in Trojan war in Greek mythology, Greeks left this giant hollow horse as an offering to goddess Athena. The Greek soldiers were hiding the belly of a hollow horse and once they entered the city they ravaged the city of troy. Same way RAT fools its recipient by inviting them into the malicious software onto their system. Once malicious software is installed it provides access to RAT hackers.
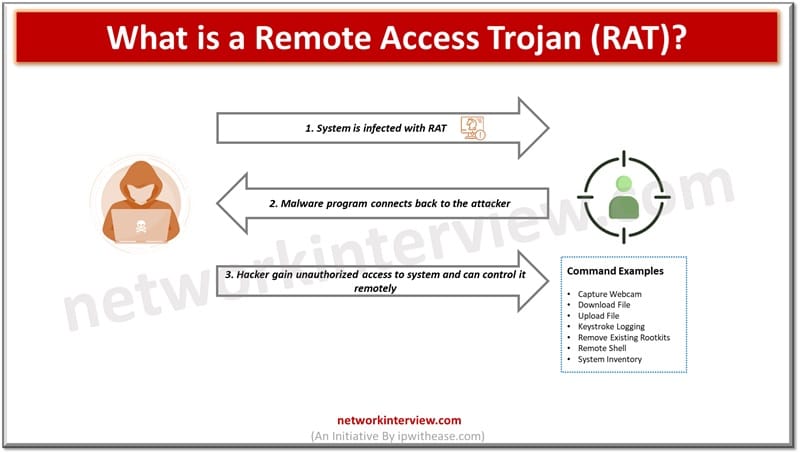
Hacker gains remote access to a system disguised as a harmless file or application it opens a backdoor to devices over the network, exposing data and other sensitive information. It gives malicious actors unrestricted access to devices and can control hardware such as webcam and software or personal information such as financial details – credit card, bank details etc.
How Remote Access Trojan (RAT) works
Remote Access Trojan works like a non-malicious remote access tool. They are designed to stay hidden and carry out tasks without the knowledge or consent of system user. To install a RAT the hacker first tricks user into downloading the software. The bad actor might send a phishing email link containing a legit URL from website. The downloaded application imitates itself as a trustworthy remote application but post installation it will not appear in the list of installed software’s or running processes. They are dangerous because hackers get complete administrative control of the system.
Sometimes RATs are paired with keyloggers to increase the chance of obtaining credential details etc. If RAT gains access to several devices, they can target a server having internet traffic from all of them and launch a DDoS attack and can shut a server down. Some most popular and common RAT viruses are – CrossRAT, Beast, Mirage, Saefko, Poison ivy, Blackshades.
How to detect Remote Access Trojan (RAT)
RAT is difficult to detect however, there could be some tail-able signs indicating its presence on the system.
- Redirection of Websites – if the browser keeps redirecting web searches onto different pages this could be a probable sign that the system is under someone else’s control.
- Strange Files on System – hackers may try to store their files on your system to hide their illegal activities. If you find files on your system which you do not recognize scan system
- Webcam is On – if webcam is randomly on there is a possibility being activated remotely
- Poor System Performance – Slow or poor performance of system could be an indication of hacker using your system for some background activities
How to Protect Against Remote Access Trojan (RAT)
- Enable two factor Authentication – enabling two factor authentication helps to keep hackers at bay in gaining access to online accounts even if they gain access to the system.
- Avoiding Suspicious links and Email attachments – whenever you receive an email or link in your inbox, always check its authenticity and do not open or click on mails from unknown senders.
- Keep Operating System Updated – ensure that your system has latest patches and you update your system regularly
- Software Installation from Legitimate Websites Only – Stick to legitimate websites and stores (Such as Apple and google play store) to get softwares
- Using VPN – VPN encrypts the internet data and hides IP address when you venture online. They block anyone trying to track your system
- Using an Intrusion Detection System – An intrusion detection system (IDS) monitors network activity and alerts you if something suspicious happens, such as an attempt to stop a firewall.
- Install Antivirus Software – having a good quality antivirus software re help to block suspicious software’s getting installed into your system and shield them.



