What is CASB (Cloud Access Security Broker)?
What is CASB?
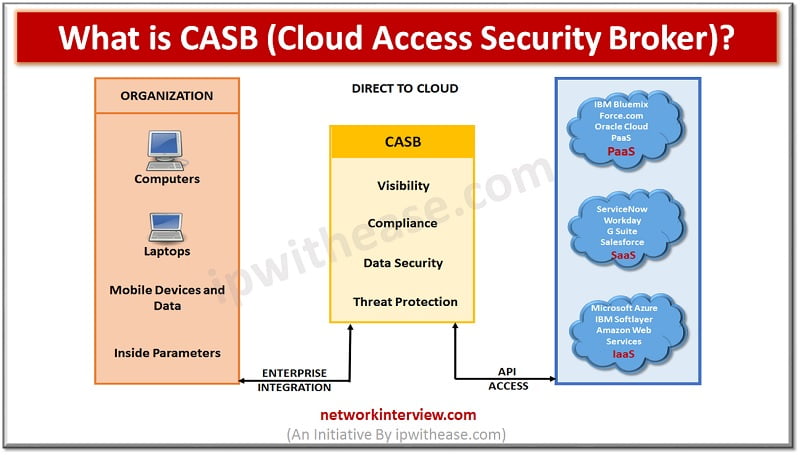
Cloud access security brokers (CASBs) is a cloud hosted solution placed between cloud service consumers and cloud service providers to implement security, compliance and governance security policies for cloud applications. CASBs help organizations to extend the security controls of their infrastructure over the cloud.
CASB Features
- Identifies malware attack and prevent it from entering into the organization network.
- Checks user authentication credentials and makes sure they only access appropriate resource.
- Web application firewalls (WAFs) designed to breach security at the application level rather than at the network level.
- Data loss prevention (DLP) to ensure that users cannot transmit organization’s confidential information outside of the corporation.
Four pillars of CASB –
- Visibility: CASB gains visibility into user activity over the cloud applications. Cloud apps that are uncontrolled and outside of governance risk and compliance processes of the organization. It enhance visibility into cloud app account usage like who uses which cloud app, their departments, locations and devices used.
- Compliance: Identify sensitive data in the cloud and enforce DLP policies to meet data compliance requirements.
- Data Security: CASB implements data security such as encryption, tokenization and access control including information rights management.
- Threat Protection: Detect and respond to malicious threats, privileged user threats and compromised accounts.
Why Do We Need a CASB Solution?
Some of key reasons which justify need for using CASB solution are enlisted below –
- Cloud application discovery and risk rating
- Adaptive access control
- Data loss prevention
- User and entity behaviour analytics
- Threat protection
- Client-facing encryption
- Pre-cloud encryption and tokenization
- Bring your own key (BYOK) encryption management
- Monitoring and log management
- Cloud security posture management
How does a CASB work?
Cloud Access Security Broker (CASB) works by securing data flowing to and from cloud environment by implementing an organization’s security policies. CASB protect organization systems against cyber-attacks through malware prevention and provide data security with encryption making data streams unreadable to hackers.
CASBs use auto-discovery to find cloud applications in use and identify high-risk applications, users and other key risk factors. Cloud access brokers may implement a number of different security access controls including encryption and device profiling. CASB also provide other services such as credential mapping when single sign-on is not available.
Deployment Modes
There are 3 key modes in which CASB can be deployed. More on the deployment modes is shared below –
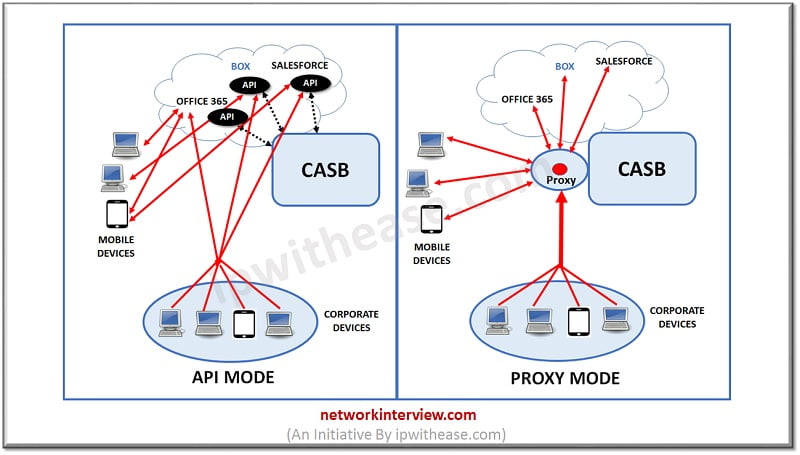
- Proxy mode: CASB can be deployed in proxy mode between users and cloud applications. This can be deployed in two ways:
- Reverse proxy: In reverse proxy mode, cloud applications are configured to allow traffic through the proxy. This can be deployed as a gateway or as more popular method of SaaS. This is performed by changing the way of authentication works by the cloud service that the CASB passes the authentication to the IDaaS provider. IDaas stands for Identity-As-Service (IdaaS).
- Forward proxy: In forward proxy mode, traffic is allowed to pass the CASB proxy by network devices (for office users) or by agents on each endpoint (for external users). This can be implemented as on-premises and some vendors may deploy software agents on endpoint devices.
- API mode: API mode allows organization to perform a number of functions like log telemetry, policy visibility and control on application and data security inspection in the cloud application. CASB offers on-premises or hosted key management options. API mode makes it possible to take advantage of both CASB-native and a growing number of SaaS service data protection features offered by the SaaS provider itself where it performs encryption and tokenization functions.
- Hybrid mode: CASB also offers a hybrid mode that combines API mode and proxy mode. This allows the CASB to support with visibility, policy enforcement and ways to deal with unmanaged devices.
Vendors
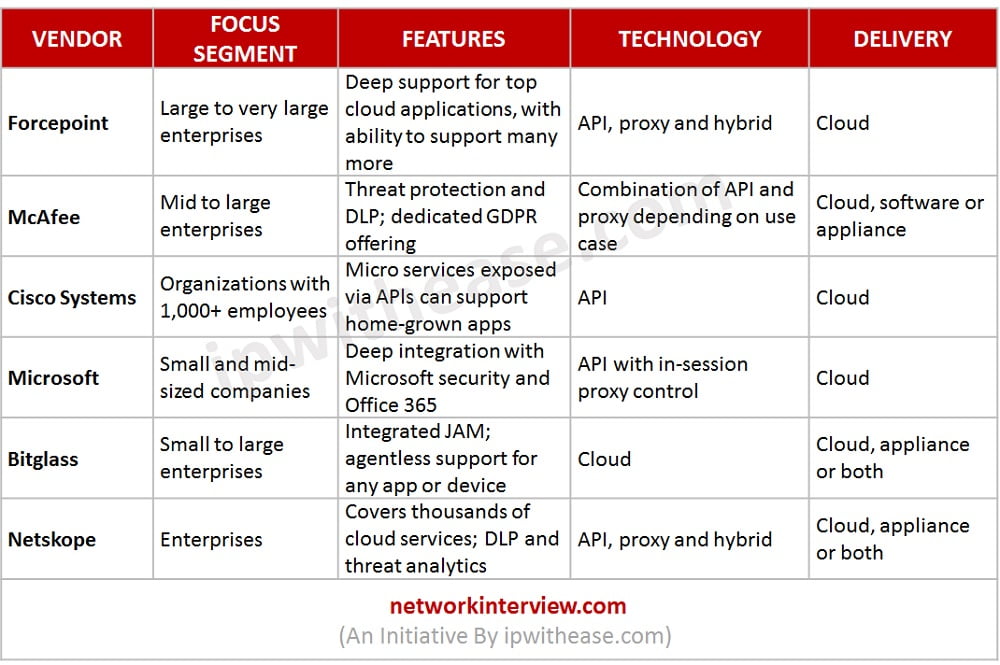
VENDOR | FOCUS SEGMENT | FEATURES | TECHNOLOGY | DELIVERY |
| Forcepoint | Large to very large enterprises | Deep support for top cloud applications, with ability to support many more | API, proxy and hybrid | Cloud |
| McAfee | Mid to large enterprises | Threat protection and DLP; dedicated GDPR offering | Combination of API and proxy depending on use case | Cloud, software or appliance |
| Cisco Systems | Organizations with 1,000+ employees | Micro services exposed via APls can support home-grown apps | API | Cloud |
| Microsoft | Small and mid-sized companies | Deep integration with Microsoft security and Office 365 | API with in-session proxy control | Cloud |
| Bitglass | Small to large enterprises | Integrated JAM; agentless support for any app or device | Cloud | Cloud, appliance or both |
| Netskope | Enterprises | Covers thousands of cloud services; DLP and threat analytics | API, proxy and hybrid | Cloud, appliance or both |
Download the table here.
Conclusion
There is no question that cloud-based applications multiply the challenges faced by enterprise security teams. They lose visibility into the applications and lose control over devices and user behaviours. CASB finds a way to extend visibility, threat protection and policy enforcement to cloud applications. Cloud access security brokers are an innovative response to these challenges.
Tag:cloud