What is DLP? What are the 3 Types of Data Loss Prevention?
Data is the key differentiator for businesses and enterprises hold a trove of business secrets, customer personal data, and other sensitive information vital for businesses. Hackers’ prime target is this data for their personal gain , and organizations struggle to keep data secured from preyed eyes. It is hard to keep business critical data safe as the IT landscape is no longer confined to closed rooms but now hundreds and thousands of users across globe access data which is stored on premises and over cloud.
Today we look more in detail about three types of data loss prevention philosophy, causes of data loss, strategies and techniques of data loss prevention and types of data loss prevention etc.
Types of Data Loss and Its Causes
Loss of data is defined as data breaches and data leakage or data exfiltration. A data breach is a kind of cyberattack where unauthorized personnel gain access to sensitive and confidential information including personal information such as bank account numbers, healthcare data, customer records, intellectual property, financial data etc. Average cost of such data breaches as per latest IBM 2023 report is USD 4.45 million which has increased 15 times in the last three years. Accidental exposure and actual data theft are on rise.
Data loss could occur due to numerous reasons such as
- weaknesses or flaws in system,
- applications which hacker can exploit,
- Stolen credentials,
- insider threats wherein authorized users put data at risk due to carelessness or intentionally,
- malware such as ransomware encrypts data so it cant be accessed and demands a ransom for decryption key,
- social engineering fool people in sharing data they shouldn’t share,
- physical device theft wherein laptop,
- smartphone or any other device gets stolen.
Related: What is Homomorphic Encryption? 2 Types of HE
Data Loss Prevention Strategies
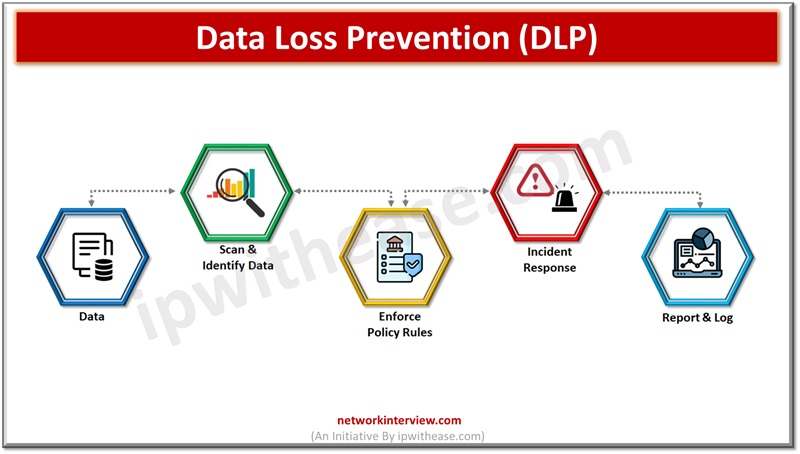
Organizations implement Code Signing Certificates and prepared for data loss prevention(DLP) strategies to protect against all types of data loss and theft. DLP strategies are a set of policies which define how data will be handled by users. DLP policies cover data storage, data access, data security controls. Instead of implementing a single policy across enterprises, different sets of policies are created by security teams to handle different types of data.
Data related to personal health records, financial information require more stringent controls and might enforce controls its access is restricted to a specific set of people, wherein intellectual property protection shall require a different kind of controls. Policies are reviewed regularly to ensure they are aligned to changes in relevant regulations, enterprise network and operations.
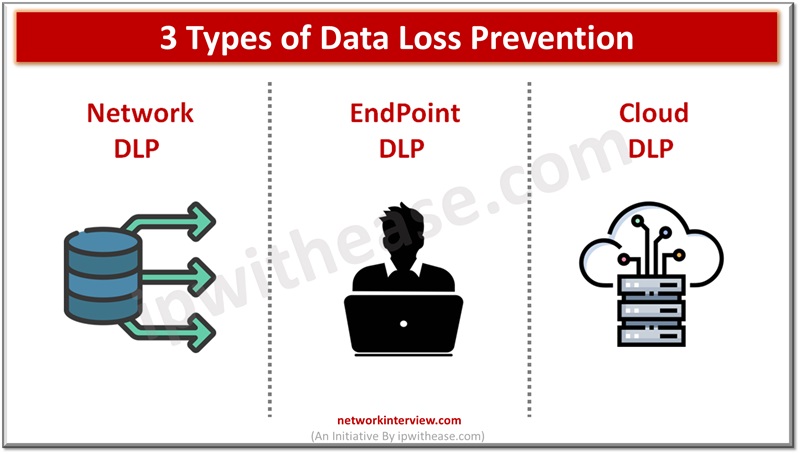
Types of Data Loss Prevention
There are three main types of data loss prevention solutions: endpoint, cloud, and network. Organizations choose to use one type of DLP solution or combine all three depending on their business needs and how storage of data happens.
Network DLP
Network DLP solutions is more about data movement through, into and outside. They often deploy artificial intelligence (AI) and machine learning for detection of abnormal network traffic to signal data loss. Network DLP is designed to monitor data in transit but also provides visibility into data in use and at rest. Network DLPs keep track of all network traffic and monitor messages, file transfers, and emails.
Endpoint DLP
Endpoint DLP monitors activity on end user systems such as laptops, servers, mobile devices, and any other devices which are accessing the network. These solutions are installed locally and stop users from performing actions which are prohibited as per DLP policies on systems. DLP policies enforce action such as stopping unapproved data transfers between systems or outside the network. All endpoints are monitored in real time to prevent misuse, leakage, and transfer of confidential information.
Cloud DLP
Cloud DLP solutions focus on data stored on cloud storage and accessed over cloud. They scan , classify , monitor, encrypt and block data from leaving cloud repositories. These tools enforce access controls to individual end users and on cloud services which might have access to business data. It keeps a log about what files got accessed with user identity.
Quick Fact !
Cloud based DLP has 60% of market share due to quick adoption of cloud by enterprises.
Continue Reading:
8 Common Web Application Vulnerabilities
What Is Data Masking? Types & 8 Techniques



