Check the list of Interview Questions:
ASA Firewall
- What is a Firewall?
- What Is Default Route Configuration Command In ASA Firewall?
- What Is Default TCP Session Timeout?
- What Is A Transparent Firewall?
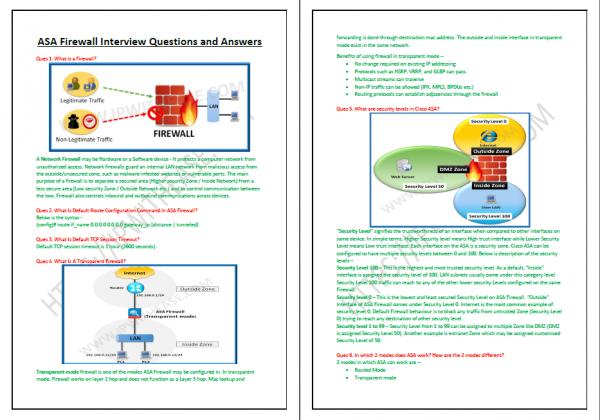
- What are security levels in Cisco ASA?
- In which 2 modes does ASA work? How are the 2 modes different?
- What Is Default Security Level For Inside Zone In Asa?
- How to allow packets from lower security level to higher security level?
- How to allow packets from between VLANs/Interfaces across same security level?
- What Command to Check NAT Table in Cisco Asa?
- Can We Block HTTPS Traffic On Firewall?
- Can We Mix Different Models In Clustering I.e. Can 5510 Be Clustered With 5520?
- Does ASA support Server Load Balancing?
- Can we use ASA For Web Filtering Like Proxy?
- Firewall Works at which layer?
- Difference between Stateful and stateless firewall?
- What information does stateful Firewall maintain?
- Does ASA inspect ICMP by default?
- What are timeout values in ASA firewall for TCP, UDP and ICMP sessions?
- Active FTP vs. Passive FTP?
- Does Cisco ASA support BGP?
- What is FWSM? Where is it used?
- Difference between PIX and ASA?
- Which command is used in ASA to view connections?
- What is functionality of NAT control in Cisco Firewalls?
- What are types of Contexts in ASA?
- Difference between checkpoint and ASA?
- What are hardware and software requirements for 2 ASA to be configured in high availability?
- Explain different NAT types – Dynamic NAT, Static NAT, Identity NAT, Static PAT, Dynamic PAT and Policy Based Nat?
- Which command will forcefully activate secondary firewall to become active firewall?
- What is spoofing and what is anti-spoofing?
- Which are ASA platform series in use nowadays?
- What is DMZ Zone? What is DMZ zone used for?
- What is DOS and DDOS?
- Explain Active/Active failover?
- Explain Active/Standby failover?
- What are different types of ACL in firewall?
- What is syn flooding?
- What is difference between ACL on ASA and Router?
- Can we create loopback on ASA?
- Which command is used to capture packets on ASA?
- How to configure a static and default route on ASA?
- Which features are not supported in transparent mode?
- Which commands are used to convert routed mode to transparent mode and vice versa?
- Which features are not supported in multiple context mode?
- What is order of preference of NAT types in Cisco ASA?
- What type of end systems/connections reside in DMZ Zone?
- What type of end systems/connections reside in EXTRANET Zone?
- Which command is used to verify the failover state?
- Which command is used to check the traffic on interfaces, the packet and byte counters?
Palo Alto Firewall
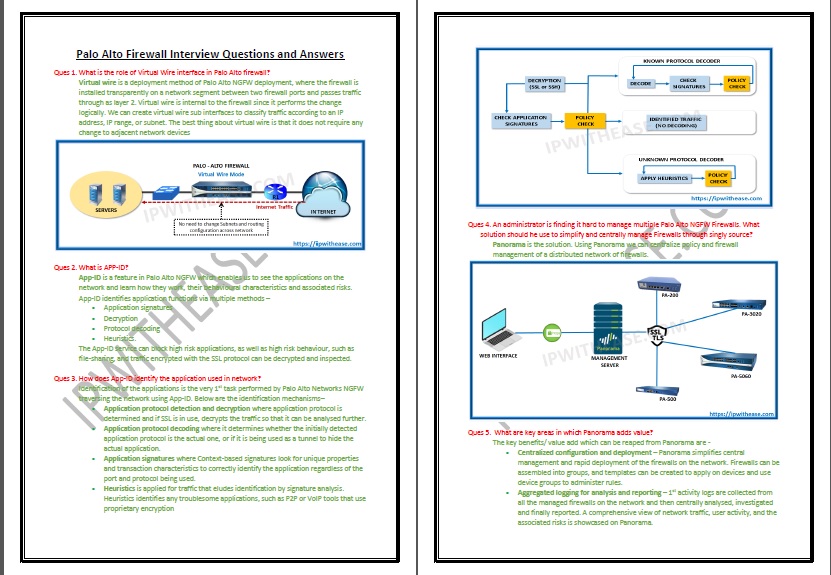
- What is the role of Virtual Wire interface in Palo Alto firewall?
- What is APP-ID?
- How does App-ID identify the application used in the network?
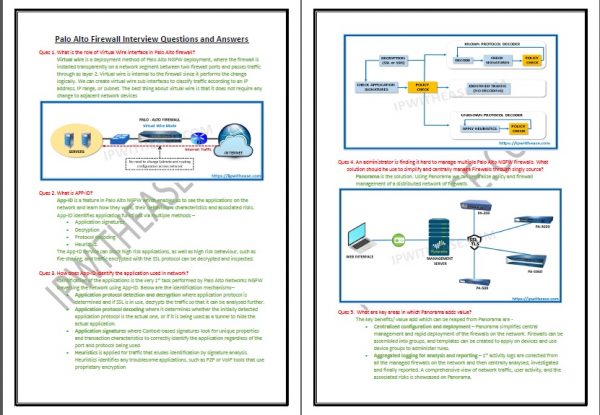
- An administrator is finding it hard to manage multiple Palo Alto NGFW Firewalls. What solution should he use to simplify and centrally manage Firewalls through singly source?
- What are 3 focal areas in which Panorama adds value?
- What are the benefits of using Panorama?
- Which Palo Alto Networks solution targets endpoint security from Cyber-attacks?
- What are different modes in which interfaces on Palo Alto can be configured?
- Which command is used to show the maximum log file size?
- What is function of Zone Protection Profile?
- What is difference between Palo Alto NGFW and WAF?
- What is U-Turn NAT?
- Explain the difference between Virtual Routers and Virtual Systems in Palo Alto?
- A new customer wants to setup firewall to process 10Gbps of traffic. Which firewall models could be recommended to the customer?
- Which Dynamic Routing protocol cannot be configured on the Palo Alto Firewall?
- What is difference between stream-based and file-based application scanning?
- Which all IPS mechanisms are used for Content-ID to secure network from attacks?
- What widget allows administrators to quickly investigate security incidents by correlating threats with applications and user identity?
- Which all types of logs can be viewed on Palo Alto NGFWs?
- A malicious file was not blocked by WildFire evaluation and somehow was allowed to execute. Can such malicious activity still be blocked?
- What is Wildfire? Explain its functioning?
- By default, what is the IP address of management port on Palo Alto Firewall and default username/password?
- What is the key difference between superuser and device administrator?
- How many virtual systems can be carved out fromPA-800?
- What are the HA modes in which Palo Alto Firewall can be configured?
- What is HA Lite?
- Explain Active/Active HA in Palo Alto NGFW?
- Explain Active/Passive HA in Palo Alto NGFW?
- What are the different states of HA Firewall?
- Which ports types are used in HA Pair?
- What are the prerequisites while configuring an HA pair?
- The Palo Alto Networks firewall supports how many VPN deployments?
- What is a service route? What interface is used by default to access external services?
- How many zones can an interface be part of?
- 2 Zones are configured on a Palo Alto Firewall. IP communication is not happening between both zones. What is required to allow this?
- What interface options are available to manage Palo Alto Firewall?
- Which file is mandatory for bootstrap process to function?
- What is the basic approaches to deploy certificates for Palo Alto Networks firewalls?
- What are different types of links related for Firewall HA?
- What parameter decides a primary and secondary HA pair?
- What is the Application Command Center (ACC)?
- An administrator to configure a Palo Alto Networks NGFW to provide protection against worms and trojans. Which Security Profile type will protect against worms and trojans?
- Which virtualization platforms support the deployment of Palo Alto Networks VM-Series firewalls?
- A traffic log displays “incomplete” for a new application. What does that mean?
- What are options available on Palo Alto firewall for forwarding the log messages?
- What happens when a URL matches multiple patterns (multiple custom URL filtering categories and allow/block-list) within a URL filtering profile?
- What actions are available while filtering URLs?
- Which are pre-defined administrator roles?
- What is the Captive portal and its usage?
- How Does Panorama address new logs Logs when It Reaches Maximum Storage limit?
Checkpoint Firewall
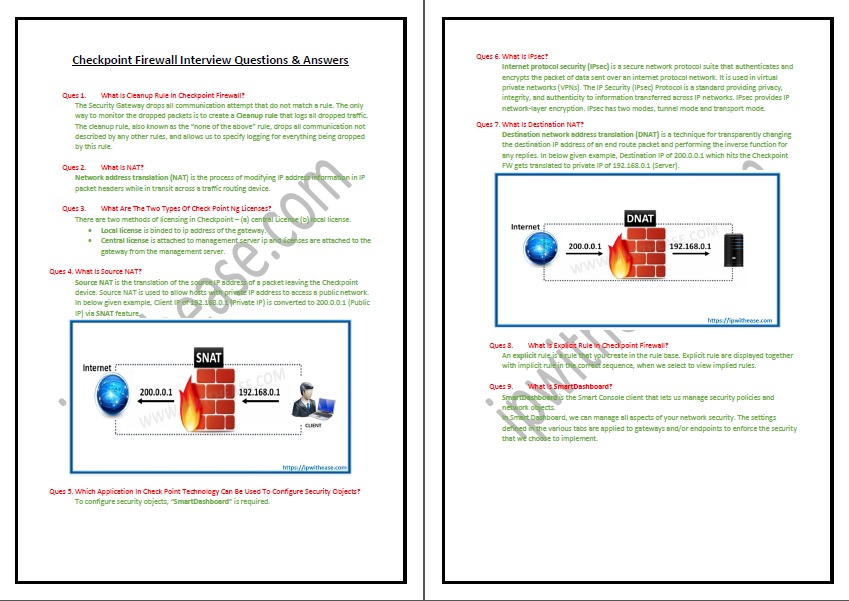
- What Is Cleanup Rule In Checkpoint Firewall ?
- What Is NAT ?
- What Are The Two Types Of Check Point Ng Licenses ?
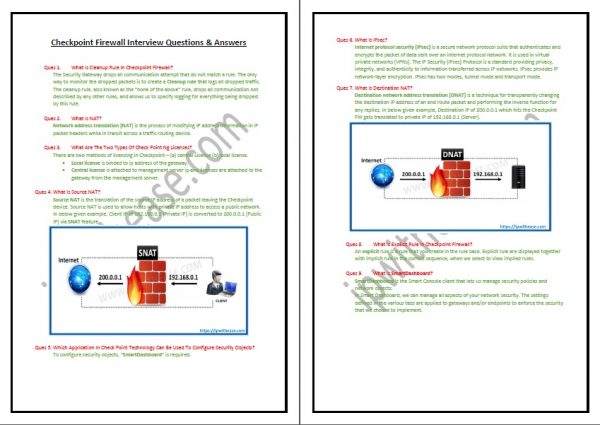
- What Is Source NAT ?
- Which Of The Applications In Check Point Technology Can Be Used To Configure Security Objects ?
- What Is IPSec ?
- What Is Destination Nat ?
- What Is Explicit Rule In Checkpoint Firewall ?
- What Is Smart Dashboard ?
- What Is 3 Tier Architecture Component Of Checkpoint Firewall ?
- Difference Between Automatic NAT And Manual NAT ?
- What Are The Functions Of Cpd, Fwm, And Fwd Processes ?
- What Is the main Different Between Cpstop/cpstart And Fwstop/fwstart ?
- What Is The Packet Flow Of Checkpoint Firewall ?
- What is Stealth Rule in checkpoint firewall ?
- What Is SIC ?
- What are the major differences between SPLAT and GAIA ?
- What is Checkpoint Architecture ?
- What is Hide NAT ?
- difference between standalone deployment distributed deployment ?
- What is Anti-Boat ?
- Difference between fwstop and cpstop ?
- What is CPinfo? And why it is used ?
- What is MDF Database ?
- How to configure SMC HA ?
- Which protocol use in Checkpoint for Clustering ?
- What are Delta and Full Mode in Clustering ?
- How to Install Checkpoint Firewall NGX on SecurePlatform ?
- What is the Packet Flow of Checkpoint firewall ?
- What are major differences between NGFW and NGTP ?
- Does Checkpoint NGFW support following Software blades – URL filtering, Antivirus, Anti-spam? If answer is “No”, then which Checkpoint Appliance supports above blades ?
- Which Checkpoint NGFW/NFGT Models are used in Data Center environement ?
- 40 Gbps (QSFP) support in Checkpoint Security Gateway Appliances starts with which model ?
- What is Asymmetric Encryption ?
- What is Anti-Spoofing ?
- What is VPN ?
- What is the difference between standalone deployment distributed deployment ?
- Types of NAT in Checkpoint firewall ?
- What is use of Database Revision Control ?
- Which blade do we investigate when you see high CPU caused by the pdpd process ?
- Which command would be best suited for viewing the connections table on a gateway ?
- Which command you run to list established VPN tunnels ?
- Which command displays compression/decompression statistics ?
- Which program you use to analyze Phase I and Phase II packet exchanges ?
- Which folder contains the VPN debug files ?
- What does a high confidence rating mean in IPS ?
- What command you should run to determine if Accept, Drop and NAT templating is enabled ?
- What causes the kernel message: kernel: neighbor table overflow ?
- How you would determine the value of ‘Maximum concurrent connections’ of the NAT Table ?
- What command displays the IPV6 routes ?
Juniper SRX Firewall
- What is latest Firmware version in Juniper SRX110H2, SRX550 and SRX650 Firewall?
- Which models of Juniper SRX as preferred for Branch locations and which for Data Center/Head Office?
- How many FPCs can be installed in
- SRX1400
- SRX3400
- SRX3600
- SRX5400
- SRX5600
- Which all SRX platforms have dedicated HA ports for cluster?
- Which all SRX platforms support dual control ports?
- What is VR wrt SRX firewall?
- What is Cisco ASA equivalent of Context in Juniper SRX?
- What is Web interface for SRX called?
- What application is used in Junos Space to manage SRX policies?
- What is the key differentiator and core design change that SRX brought over the NetScreen devices?
- What is difference between Stateless and Stateful Firewall?
- What is Juniper solution of IPSEC VPN for users over internet to access corporate resources like email or application servers called?
- What does a Services Processing Card do?
- Which SRX platforms support the UTM feature set?
- What tool does Juniper make to handle log management?
- What is JFlow?
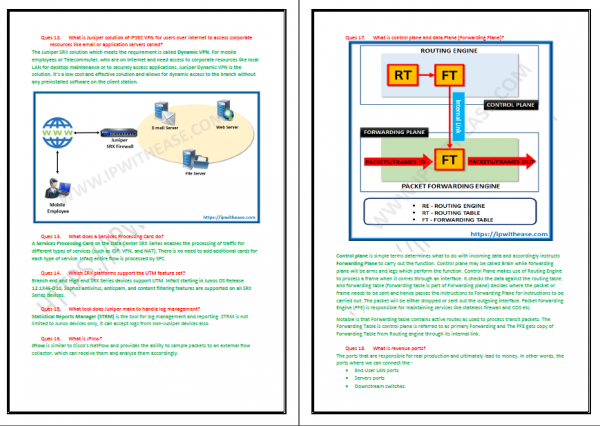
- What is control plane and data Plane (Forwarding Plane)?
- What is revenue ports?
- Can we reset root password if we forget one? How?
- What is a cluster and why is it required?
- Is cluster supported on all SRX platforms?
- How does clustering works?
- What is the concept of GARP?
- Is the Network affected during data plane failover?
- Is the Network affected during control plane failover?
- What are prerequisites while configuring 2 SRX in HA/cluster mode?
- Cisco IOS feature set of “IP SLA” is a method of monitoring and reliably reporting on network performance. What is the Juniper equivalent feature name called?
- If FAB link goes down, what happens to cluster?
- If Control link goes down, what happens to cluster?
- What is Active-Active Cluster vs Active-Passive cluster?
- What type of interfaces need to be configured in clustering?
- What is use of “Configuration GROUP” Hierarchy in cluster?
- Which config portion controls the permissions for traffic flow (sec policies)?
- What is a security Zone?
- Is the traffic by default permitted for Inter Zone or Intra Zone?
- How would you troubleshoot high CPU?
- Name few types of screen options?
- What are stateless Firewall filters?
- What are 3 types of VPN tunnels?
- How to troubleshoot when VPN goes down?
- Name few VPN proposal sets that can be configured on SRX?
- Is SSL VPN Supported on SRX Firewall?
- What is the best interface to use for network management on the SRX?
- What are components of the security policies?
- What is an ALG and how does it function?
- What are NAT types in Juniper SRX?
- What is difference between Virtual Router and Logical System?
- Why would you use no-NAT rules in your NAT policy, and which NAT types support them?
- What is the difference between DPD and VPN monitoring
- What is NAT-T and when must it be used?
Fortinet (Fortigate) Firewall
- You have opened a fresh Fortigate firewall, and need to access it. What is the default password for Fortigate firewall?
- As a new firewall is out of the box, and you need to connect it to your laptop for accessing it and then configure it, what is the management IP subnet you should assign to your laptop to access Fortinet firewall? In addition, what is the default IP address for managing the Fortinet firewall?
- As a network security expert you should have fair idea of configuring aggregate interface via CLI on fortigate, write basic set of commands needed to configure multiple ports in aggregate interface of IEEE 802.3ad?
- You are assigned to work on a new Fortigate firewall. What are the options available to access it (mention all those protocols/mechanisms?
- In FortiOS, which menu in Web GUI allows you to see the overall status in the form of widgets and to configure some system options?
- In Fortigate GUI, which menu allows to configure routing options?
- You are assigned a task to configure some security features like web filtering and antivirus. Which FortiOS GUI menu will you navigate in order to configure these features?
- You are working as a network security engineer with Fortinet firewalls in your network. Where would you navigate in order to configure user accounts, groups, and authentication methods, including external authentication and single sign-on (SSO)?
- You are supposed to setup an alert mechanism to be automatically notified in case of a critical event. You should setup an email alerts to your network team and management in such cases. Where should you be able to do the same in WEB GUI of fortigate firewall?
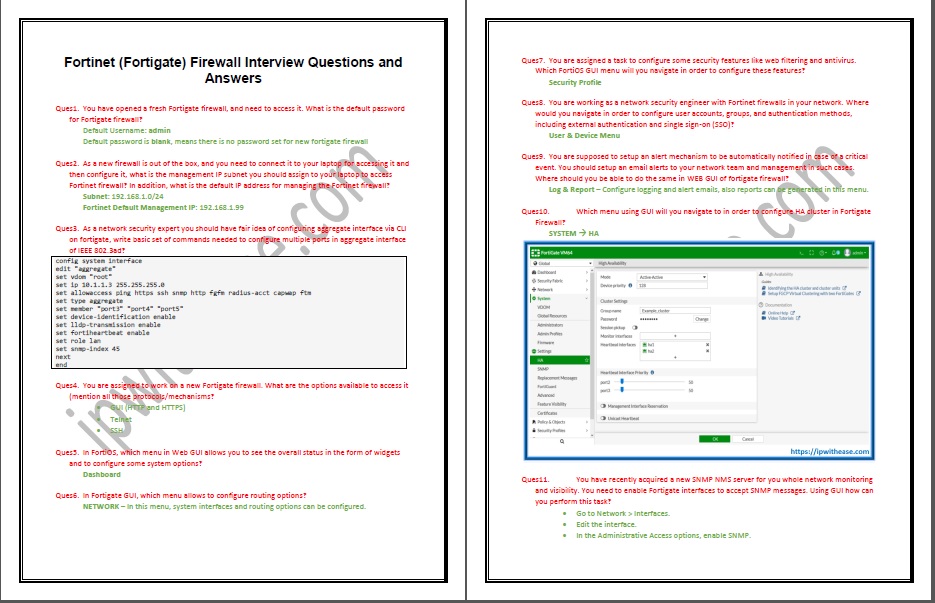
- Which menu using GUI will you navigate to in order to configure HA cluster in Fortigate Firewall?
- You have recently acquired a new SNMP NMS server for you whole network monitoring and visibility. You need to enable Fortigate interfaces to accept SNMP messages. Using GUI how can you perform this task?
- As a network Engineer, you prefer to work on CLI always over GUI, because not all settings are available for GUI to configure. So in Fortinet we should be aware of ways to connect with CLI. Can you briefly describe all these ways?
- As a network engineer, you are required to create a new soft switch on Fortigate firewall. Using CLI, mention the configurations you should perform to achieve this task.
- You have a new FortiGate firewall and for management and testing purposes, need its Port 1 to be allowed for ping, Http and SSH access. What will be the configuration?
- You are given a task to back up your configurations using SCP i.e. Secure File Copy and for this, you would need to enable it globally on firewall. How can you configure it to do so?
- Explain very briefly the steps you will perform using FortiGate GUI to take configuration backups?
- Mention basic configuration from CLI to configure new Zone?
- You are working as operations engineer and for that, your daily task is to take configuration backups to make sure you have latest configurations in case of any disaster. Using CLI, what one line will make sure you can take configuration backup on USB?
- You are informed that some users are not getting the servers access, which was working unit recently. After basic information gathering you figured out that there was some change performed on Fortinet, which could have caused services outage. You quickly made a decision to restore the configuration to last best one, which was taken recently. Using GUI how can you restore the configurations?
- You are informed that some users are not getting the servers access, which they used to get. After basic information gathering you figured out that there was, some change happened on Fortinet, which could have caused services outage. You quickly made a decision to restore the configurations to last best configurations, which was taken recently. Using CLI and having backup configuration on your USB how can you restore the configurations quickly?
- Define briefly what a security policy is and why a firewall security policy is very important for any type of traffic passing through the firewall?
- Using Fortigate in HA, you should always make sure to put hostnames on each device separately so that you can identify them in cluster that which firewall is active or backup. Using CLI how can you configure the hostname on firewall?
- You have been using FortiGate on your multiple sites since long time. Now you have decided to move one of your firewalls and dismantle it from one office location because it has been closed. Your plan is not to re-use this Firewall on another location, and for that, you need to erase all configurations to default. Which command you may use to do it?
- Your firewall has many settings; including NAT, VPNs, and routing which is all messed up. Now you have decided to re configure all these settings but making sure that interface configurations are not changed during this reset. Which is the shortest way to do it?
- You have many Users who need auto IP assignment. Being aware that Fortigate does provide DHCP feature and so it can act as a DHCP server as well. Using GUI how can you configure it as a DHCP server?
- Which menu will you go to and what steps will be performed to configure an interface on FortiGate firewall?
- Briefly explain the standard configurations set which is required to configure pair of FortiGate firewalls in Active-Active High Availability cluster?
- You need to configure virtual pair in your FortiGate Firewall, and using GUI, you must know all steps to do so. Mention those steps briefly?
- What are the basic CLI commands, which you must know as a network security engineer, to configure an interface under VDOM?
- As a network operations engineer, you need to ensure that not everyone can access or ping your firewall interfaces. For that purposes there is a feature called administrative access. Using FortiOS GUI, how can you allow restricting users for ping, http, https etc. protocols for a particular interface?
- You need to make sure your virtual Pair interface forwards traffic properly between the paired interfaces Port 3 and Port 4; you are required to make security policy to allow that. Write down CLI configurations to do so?
- As a network operations engineer, you need to ensure that not everyone can access or ping your firewall interfaces. For that purposes there is a feature called administrative access. Using FortiOS CLI, how can you allow restricting users for ping, http, https etc. protocols for a particular interface?
- You are going to setup new firewalls and that too in High Availability Active-Active Mode (cluster). Using GUI, you should be able to do so. Mention all steps, which you should take to do so?
- What is the name of protocol for link aggregation to combine multiple links for achieving more bandwidth as well as link redundancy?
- You are given a task by your manager to create link aggregation on ports 1 to 3 on Fortigate firewall using GUI, and assign IP address of 10.1.1.1/24 along with administrative access of ping and HTTPs. How would you accomplish these steps?
- What is the main difference between a redundant interface type and aggregate interface type?
- Using CLI, you should know how multiple interfaces could can be configured in redundant type mode. Mention cli configurations to make port 1, 2 and 3 as redundant ports.
- Using GUI, which steps you need to follow to configure Virtual Pair Interface Security Policy?
- You have setup a new SSL VPN for customers, but somehow it is not working. You want to see the VPN logs and events to troubleshoot further and zero in on the specific area where you will need to fix the issue. How can you configure VPN logs using CLI?
- You have been given task to separate the networks of different departments into different broadcast domains, using which feature technology can this be achieved so that each network is separated from other in layer 2 broadcast domain?
- What is the main different between FortiGate firewall setup in NAT mode and in transparent mode?
- If you are configuring Fortigate with multiple sub interfaces, related to separate networks and vlans. In such case which mode you have to use on FortiGate?
- You have been working on an existing network without any security appliance. It has been decided to integrate FortiGate firewall between trusted LAN network and Internet Gateway router. You don’t want to disturb existing network and using minimum possible changes want to achieve this, How can this be achieved?
- Fortigate firewall is being used in enterprise environment. To avoid overhead associated with static routing, you prefer dynamic routing. Which routing protocol should be preferred in LAN setup?
- Write down the basic configurations for creating a sub interface for vlan 10 in firewall with IP address 192.168.10.1/24?
- Describe briefly about the “software switch feature” in Fortigate? What are its main characteristics and benefits?
- One of the strong features of Fortinet Fortiguard is its web filtering and anti-spam. Using GUI how can you setup this feature? Mention basic configuration template to setup web filtering.
- Using GUI, you are supposed to configure a new soft switch, write down all steps, which can achieve this task?
- What is a “ZONE” and what are its benefits in firewall management and administration?
- How to create new Zones in Fortigate using GUI?
- Make a basic firewall security policy, which allows LAN traffic from Zone 1 towards Internet Port# 10?
- In a single Zone, if you need to deny different interfaces to talk to each other, which command or configuration you should apply so that different interfaces under same zone cannot communicate to each other?
- Define the term “virtual wire pair” and in what circuimstances it should be used?
- You are asked by your manager to configure two interfaces as virtual pair in your firewall. Write the configurations steps for adding port 2 and port 4 in virtual pair?
- You need to configure failure detection for your aggregate interfaces so that the specific interfaces goes down or becomes up when the aggregate interface changes its state. How can you configure using CLI such feature?
- Briefly, mention the steps you will take to navigate and configure the DNS servers on Fortigate firewall?
- Using CLI, you are asked to configure DNS settings, including DNS servers and local domain list. How can you do so using FortiOS CLI?
- Fortigate is very powerful and feature rich firewall. One of the main advantages is that it can be used as a DNS server. Using GUI briefly mention these steps?
- If internet users are unaware of any proxy that they are being in use and web browsing has been usual, then what kind of proxy is this being in action?
- Which technique used widely in all over the world to map a range of Private IPs to a lesser range of public or single Public IP for giving access over the internet?
- Your team lead has noticed that many Fortigate firewall interfaces are not being monitored properly in NMS. To ensure that the firewall interfaces receive the SNMP messages you should configure them properly. Using CLI how can you perform this task?
- In Fortigate firewall, you want to give your internet users a seamless internet experience without extra proxy settings at their end. Using CLI, configure the Transparent Proxy settings along with its desired policy to work?
- A new network is being setup in your enterprise, and you need to make sure the users get automatically IP assignment. You have already a working FortiGate firewall, which does provide DHCP server features. Using CLI how can you configured DHCP settings, like default gateway, IP range, DNS etc.
- LLDP is very powerful feature, which is often required in networks where neighboring devices existence and capabilities information is exchanged. You need to allow LLDP to run globally on your devices, for that how can you configure it on FortiGate?
- For administrating the Fortigate firewall for your network security team, you must ensure that your password policy is compliant to the standards. You are asked by the CTO of your company to enforce strict password policy for firewall administration; write a basic configuration template in CLI to do so?
- In case you need to only provide security to the network traffic and avoid using new network or layer 3 settings on firewall, which operating mode you should run your FortiGate Firewall?
- You have purchased many Fortinet firewalls, and one of them needs to be used dedicatedly for NAT purposes to translate private LAN IPs to public ISP assigned IP on WAN interface of Firewall. Which firewall mode you must configure to achieve this?
- What are the two main types of NAT in FortiGate firewall, which you can use?
- You have many engineers working on daily basis as operations team on FortiGate firewall. You want to configure specific profiles for administrating the firewall for such users like Name, Access permissions etc. Using GUI, where will you navigate to specific page to do perform this?
- You are working as a network engineer in an enterprise where a dedicated LDAP server for users exists; you want your firewalls to use this LDAP for remote authentication of your firewalls. Using CLI mention basic configuration template for LDAP settings on FortiOS?
- You need to secure the management of your FortiGate by using technique of changing default ports. Using CLI how can you change the default common ports, like HTTP, SSH and Telnet?
- It happens often that while working on Fortinet, an administrator left his desk for a small break and his system can be accessed physically by someone around. How can you avoid such a situation so that someone around cannot easily take an unattended opened Fortinet access?
- As a network security engineer, you must know about the Virtual Domains or VDOMs in Fortinet terminology. Can you describe briefly about VDOMs?
- All the traffic, which passes through Fortinet firewall, is always inspected by a security policy. Mention the systematic process of packet operation when it enters into firewall?
- Using GUI as well as CLI you must know how to assign an interface to a particular VDOM, briefly explain the steps?
- Which command in CLI in global configurations you can issue to enable Multi VDOM mode in FortiOS?
- Using GUI, you are assigned to create new VDOMs, you should however also know the same task to do in CLI how can you do so using both GUI and CLI?
- Your Fortigate firewall WAN1 interface is connected with ISP and you need to send all the traffic as a default route towards ISP IP. ISP has given you their side IP address as 58.27.1.3. How can you configure a default static route suing both CLI and GUI in your Fortigate firewall?
- You have been assigned a task to NAT all the private networks in your enterprise to single Public IP address configured on WAN interface of FortiGuard and assigned by ISP. What kind of NAT you will use to successfully perform the address translations for giving internet access to your networks?
- Which redundancy feature is used to provide redundancy by employing multiple firewalls for protection against down time of applications and services?
- What are the basic requirements for FortiGate firewalls to be part of a High Availability cluster, name few of them at least?
- In order to make a cluster of Fortigate firewalls how many minimal firewalls are required? In addition, name the protocol which is used for High Availability clustering setup?
- A high availability or HA cluster is very critical and important for any network setup. In order to ensure that it is properly designed what are the main components we must ensure from design perspective are there so that HA is properly deployed?
- In Fortinet HA cluster, Link Failure or device failure can trigger a failover; however, you are now instructed to make sure a failure in SSD can also trigger the failover to backup firewall. Using CLI how can you configure that?
- How many ways you can configure the HA cluster setup for FortiGate firewalls?
- Write down basic set of commands you need to setup an Active-Passive HA cluster on FortiGate firewalls?
- What are the main features you will receive when you subscribe with FortiGuard services on your firewall?
- There are 2 VLANs, VLAN 20 for internal network and VLAN 30 for external network i.e. WAN, and you want to configure STATIC NAT from internal network towards WAN external network. Using GUI, mention all steps you should take to configure such NAT.
- Fortinet firewall has capability to provide both antivirus and IPS services for any traffic passing through it and to block suspected traffic with its latest updated signatures and definitions. You should always make sure to run IPS and antivirus on your firewall with latest signatures and definitions. Using GUI, which steps you, will take to setup antivirus and IPS on FortiGate firewall?
- You have been facing some challenges of inappropriate content coming from Internet to your network. Which FortiGuard feature is used to block access to harmful, inappropriate, and dangerous web sites and how can you configure it?
- In Fortinet Firewall security policy, what are the options you can use or actions you may configure for match criteria to treat a packet or traffic entering the firewall?
- Configuring the Firewall security policy, there are many match criteria, like IP address, port number etc. Write down as many you may remember those parameters, which can be used in a security policy?
- What are the main QOS techniques you can use in FortiGate to limit the traffic rates and optimizing the bandwidth?
- You have been asked to limit traffic rate on a particular network/VLAN, but you are not sure which technique from QoS you should use; you have come to conclusion to use between policing and shaping. Can you define the basic difference between policing and shaping in terms of bandwidth control?
- You need to connect many office locations over VPN but need a quick solution so that your Ike phases, routing and security policies etc. are created automatically. Which kind of Fortinet solution you should use to get this done?
- You are interested in seeing router events in the firewall, and for that, need to enable those logs to be captured by FortiGate. Using CLI how can you enable router events?
- WAN optimization and security are always in demand, and every vendor tries to provide SD-WAN capability. While you are connected to multiple WAN interfaces towards ISP, how can you enable SD-WAN using GUI for WAN1 and WAN2 interfaces?
- You are going to get multiple Internet connections from ISP, and want to ensure you get full flexibility of routing between your network and ISP as gateway. Which routing protocol you should prefer in this case?
- You have multiple office locations, and want remote sites to get the internet access from main site along with many IT services like email server, dhcp server and some IT portals to get access from main head office. What solution you should provide to accomplish that?
- You have one important server in your local area network, which is not accessible from internet. However, there is a requirement to get this server accessible from internet on a specific IP and port. You are supposed to configure this on Fortigate. What kind of NAT will you use for that?
- You are relocating your network room to another building, therefore need a maintenance window to power off all your network devices, including Fortigate firewall. You must know the safe way to power off the FortiGate. Mention the steps in CLI and GUI method to power off FortiGate firewall?
Cisco FTD
- What does FTD and FMC stand for?
- What is the usage and purpose of FMC?
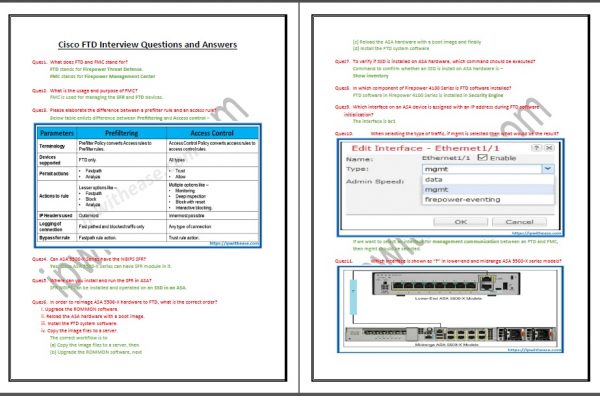
- Please elaborate the difference between a prefilter rule and an access rule?
- Can ASA 5500-X Series have the NGIPS SFR?
- Where can you install and run the SFR in ASA?
- In order to reimage ASA 5506-X hardware to FTD, what is the correct order?

- To verify if SSD is installed on ASA hardware, which command should be executed?
- In which component of Firepower 4100 Series is FTD software installed?
- Which interface on an ASA device is assigned with an IP address during FTD software initialization?
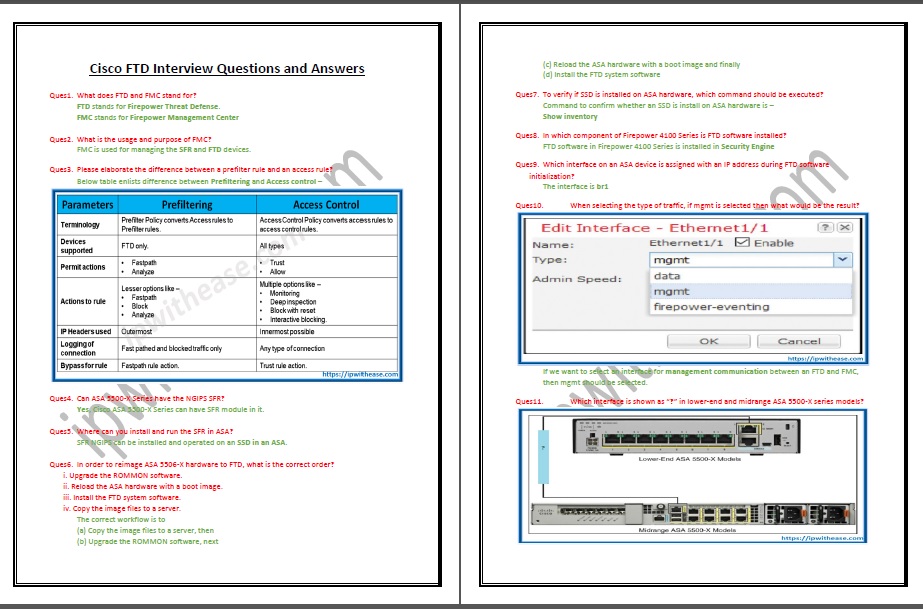
- When selecting the type of traffic, if mgmt is selected then what would be the result?
- Which interface is shown as “?” in lower-end and midrange ASA 5500-X series models?

- What is the name of the Mgmt interface which CLI shows, when connected to Firepower Code and when connected to ASA code?
- Which command is used in FTD to view the statistics of events inside the encrypted tunnel between FTD and the FMC?
- Which command confirms whether FTD is registered with the FMC?
- Which command is used to configure a manager in an FTD?
- What are the capabilities of the Firepower in terms of Licenses?
- Describe the usage and functionality of Base and Threat Licenses?
- Describe the usage and functionality of Malware and URL Filtering licenses?
- If we go to the System > Licenses > Smart Licenses page, we see Evaluation Mode button. What is the time period of the evaluation mode?

- What happens when we turn on the Evaluation Mode on the Firepower System?
- What is the workflow to Purchase, Generate, and Apply a Smart License in Firepower System?
- What is the behaviour of FTD when it is deployed in a Routed Mode?
- If you want to install FTD Version 6.1 on Firepower 9300 appliance having FXOS Release 1.1.4, what is the correct order of action?
- Which file can be deployed directly into an ESXi host if we are installing/running FMC?
- Which command syntax would be correct, if we want to ping test from FTD to the FMC?
- Which port does the Firepower System use for management communication by default?
- If we hit enter in the highlighted prompt, what would be the default firewall mode?

- In below snippet, when registration with the manager is completed, the IP 10.1.1.16 is of which device?

- Which command is used to configure FTD from Transparent Mode to Routed Mode?
- What is the behaviour of FTD when it is deployed in a Transparent Mode?
- In what mode firewall is configured in below snippet?

- In what scenario do Gig interfaces and BVI interface have same IP?

- Which command provides an overview of the various components of an inline interface set?
- What is the first-level-defense mechanism implemented on Firepower Engine?
- Which directory stores the filed related to DNS Policy?
- Which licenses are necessary to block a URL based on its category and reputation?
- Which type of analysis requires a connection to the cloud?
- Which base policy enables the largest number of standard text Snort rules by default?
- Which NAT section has highest priority during rule evaluation?
- After you deploy a new NAT policy, if a connection still uses a rule from the prior version of the NAT policy, how could you ensure that FTD will use the new policy?
- What is Security Intelligence?
- What is the function of Network Analysis Policy?
- What is the function of Intrusion Policy?
- What is Access Control Rule Monitor Action?
- What is Access Control Rule Trust Action? What is Access Control Rule Blocking Actions?
- What is Access Control Rule Interactive Blocking Actions?
- What is the function of Network Discovery Policies? What are 2 types of Network Discovery mechanisms?
- What is the purpose of Firepower Recommended Rules?
- How many connectivity models are there for network analysis and intrusion policies in Firepower System?
- Describe Balanced Security and Connectivity network analysis and intrusion policies?
- Describe Maximum Detection network analysis and intrusion policies?
- Describe No Rules Active intrusion policy?








Reviews
There are no reviews yet.